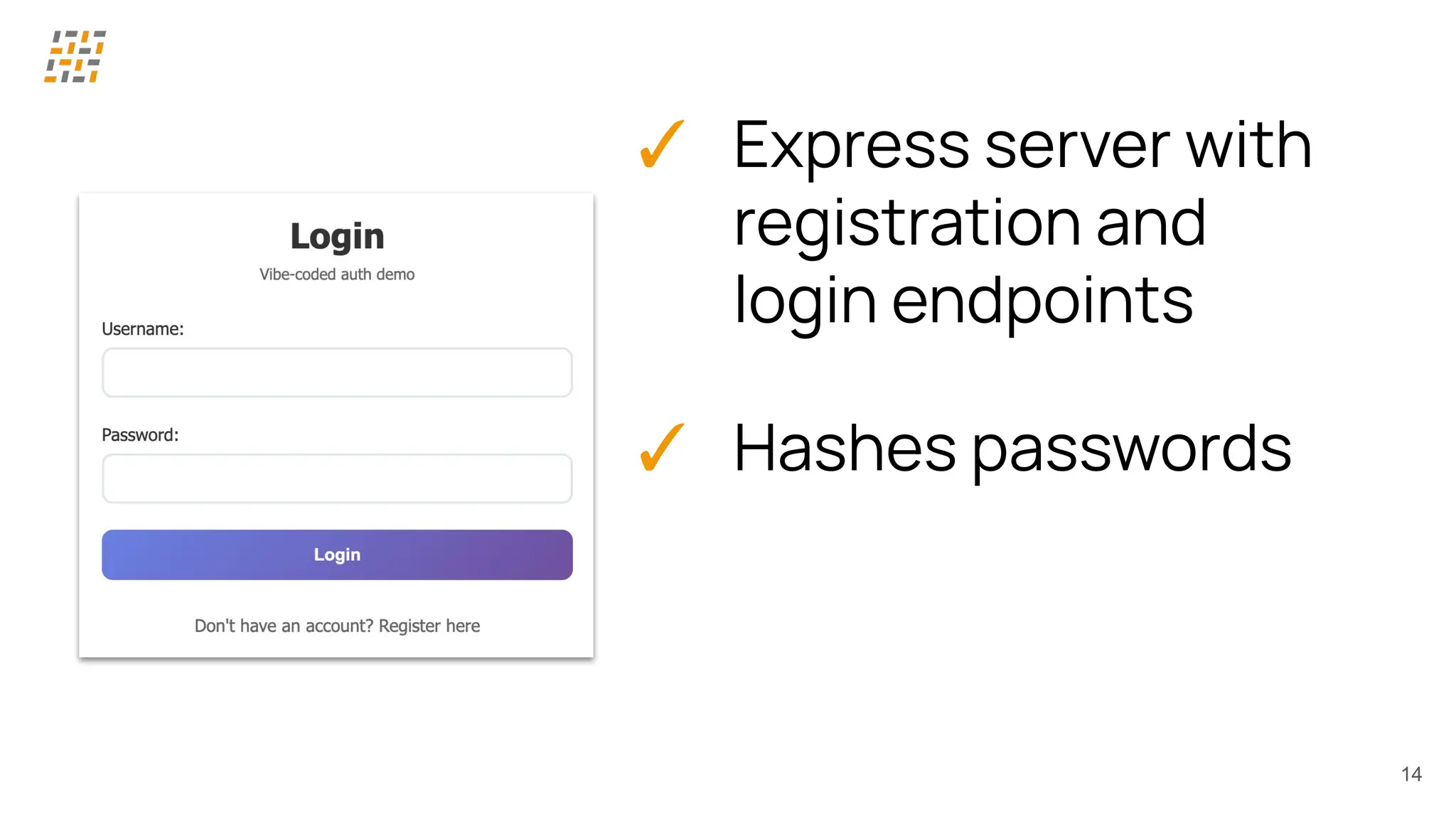
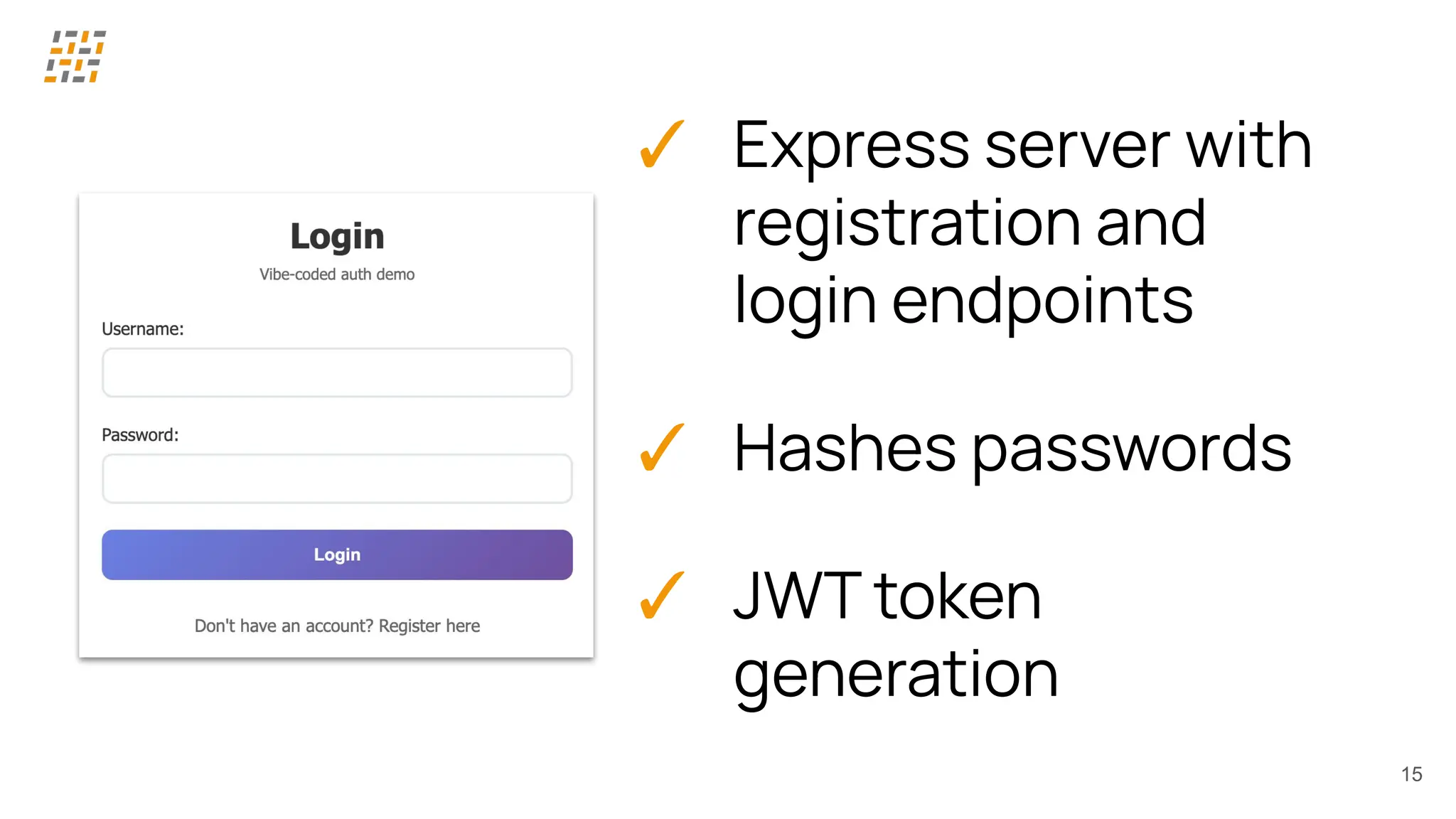
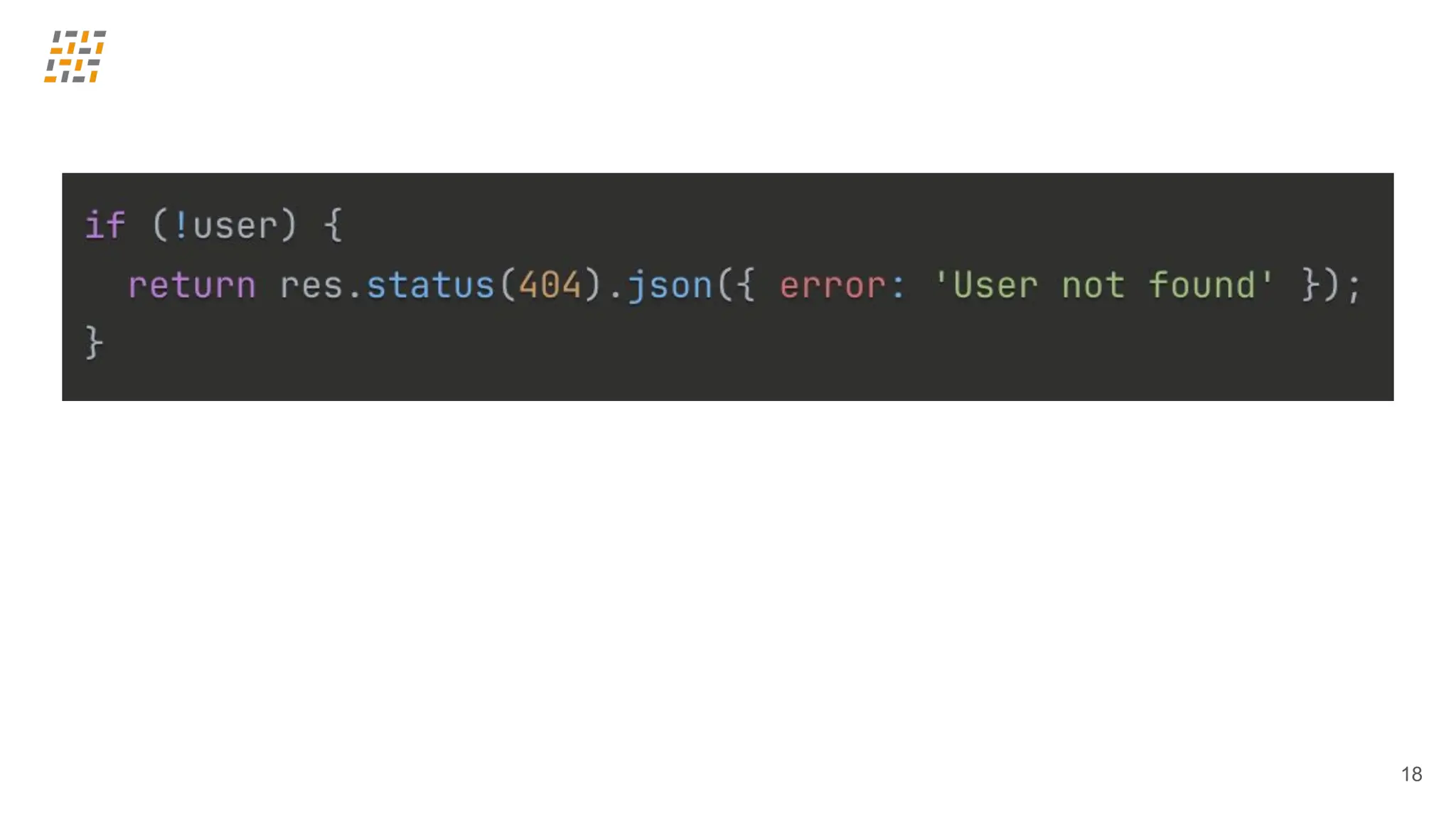
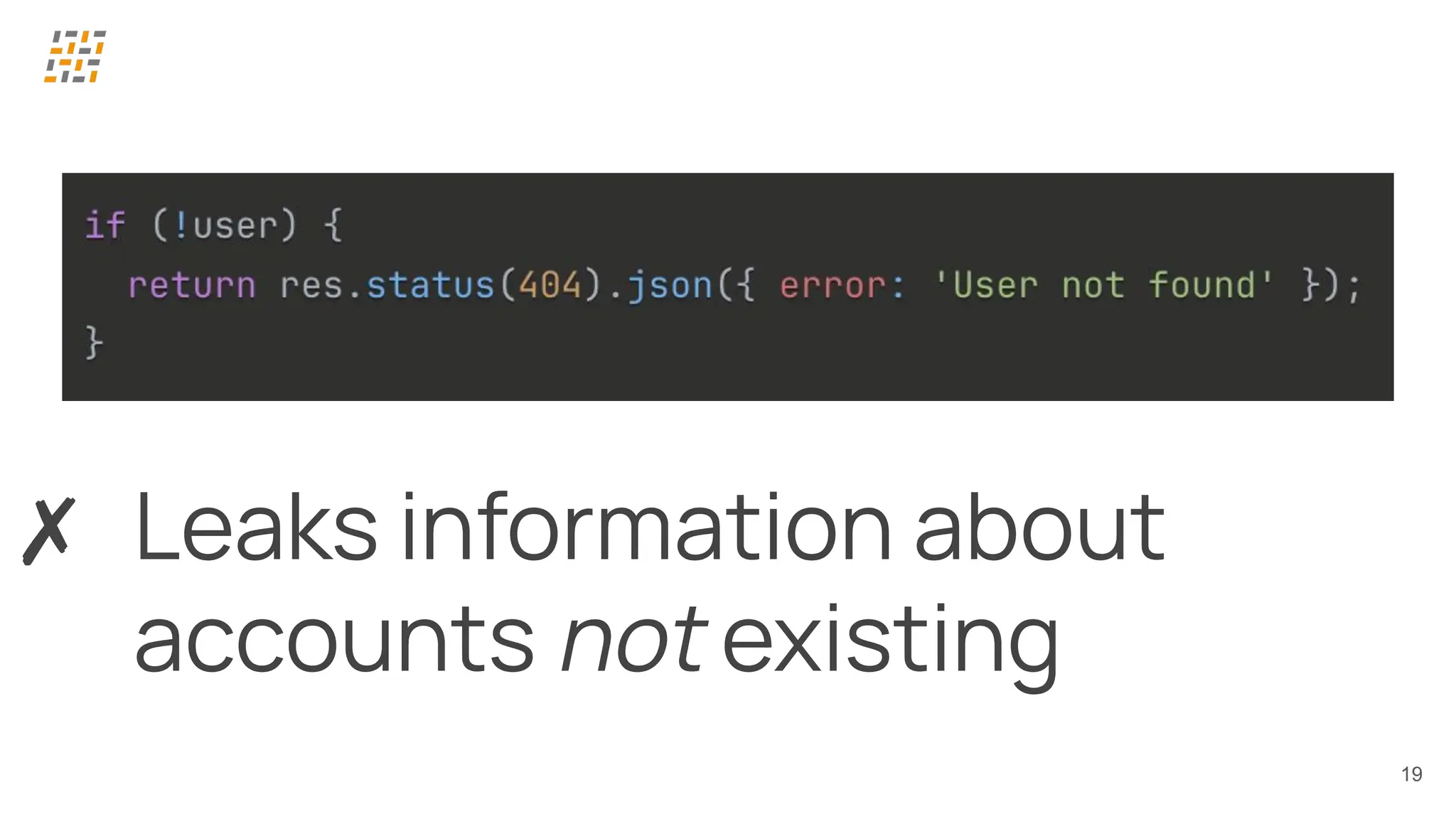
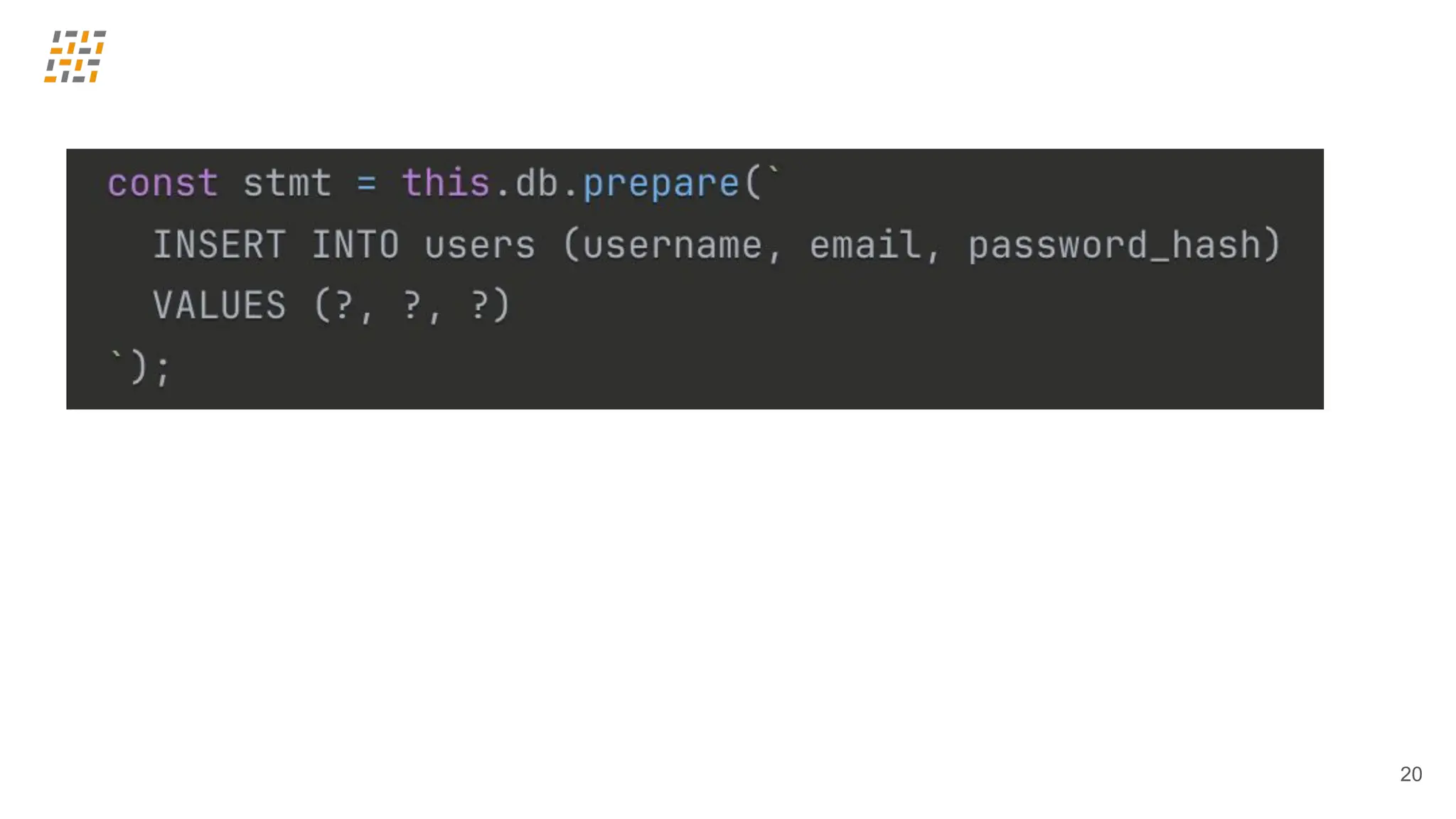
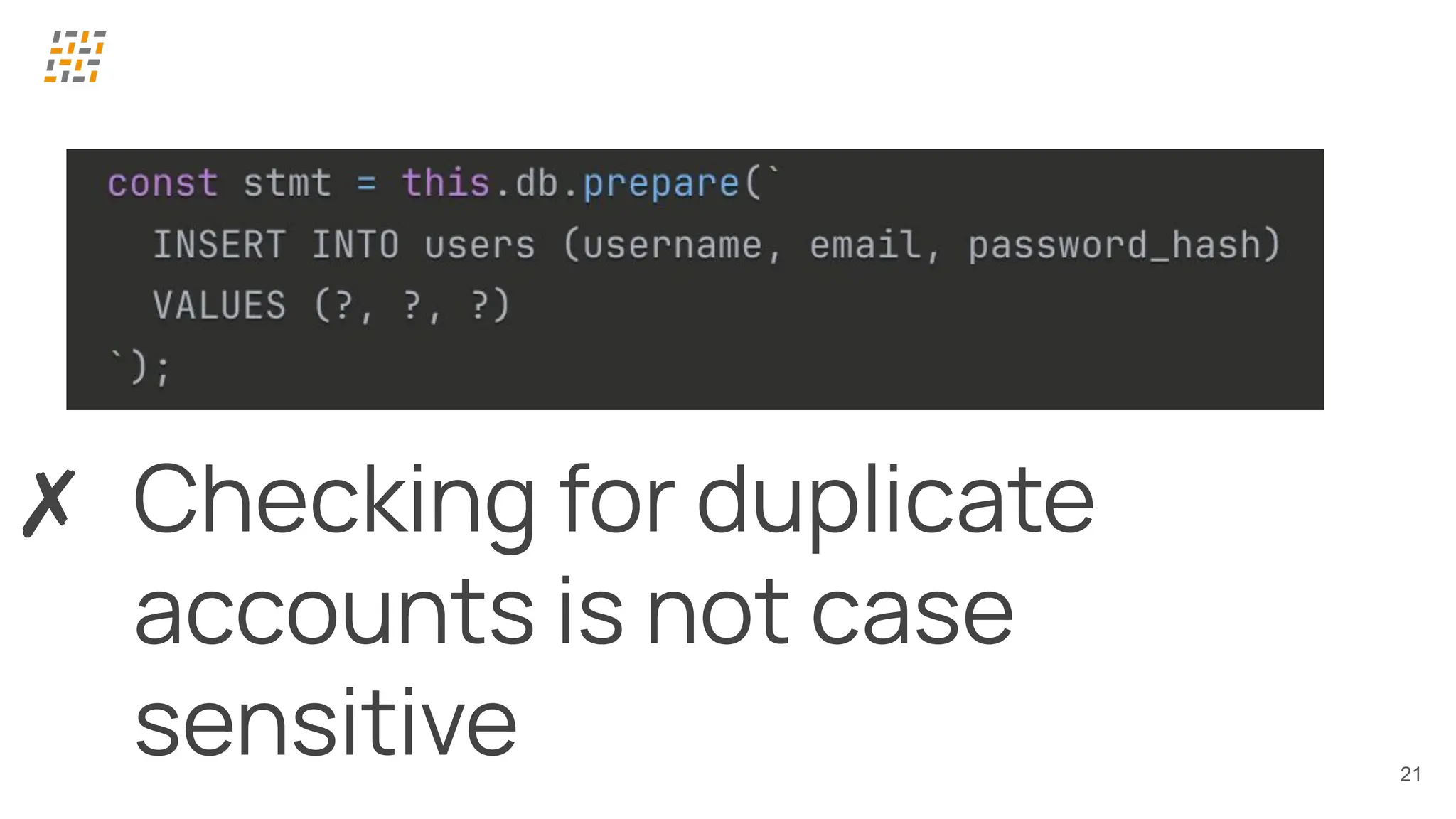
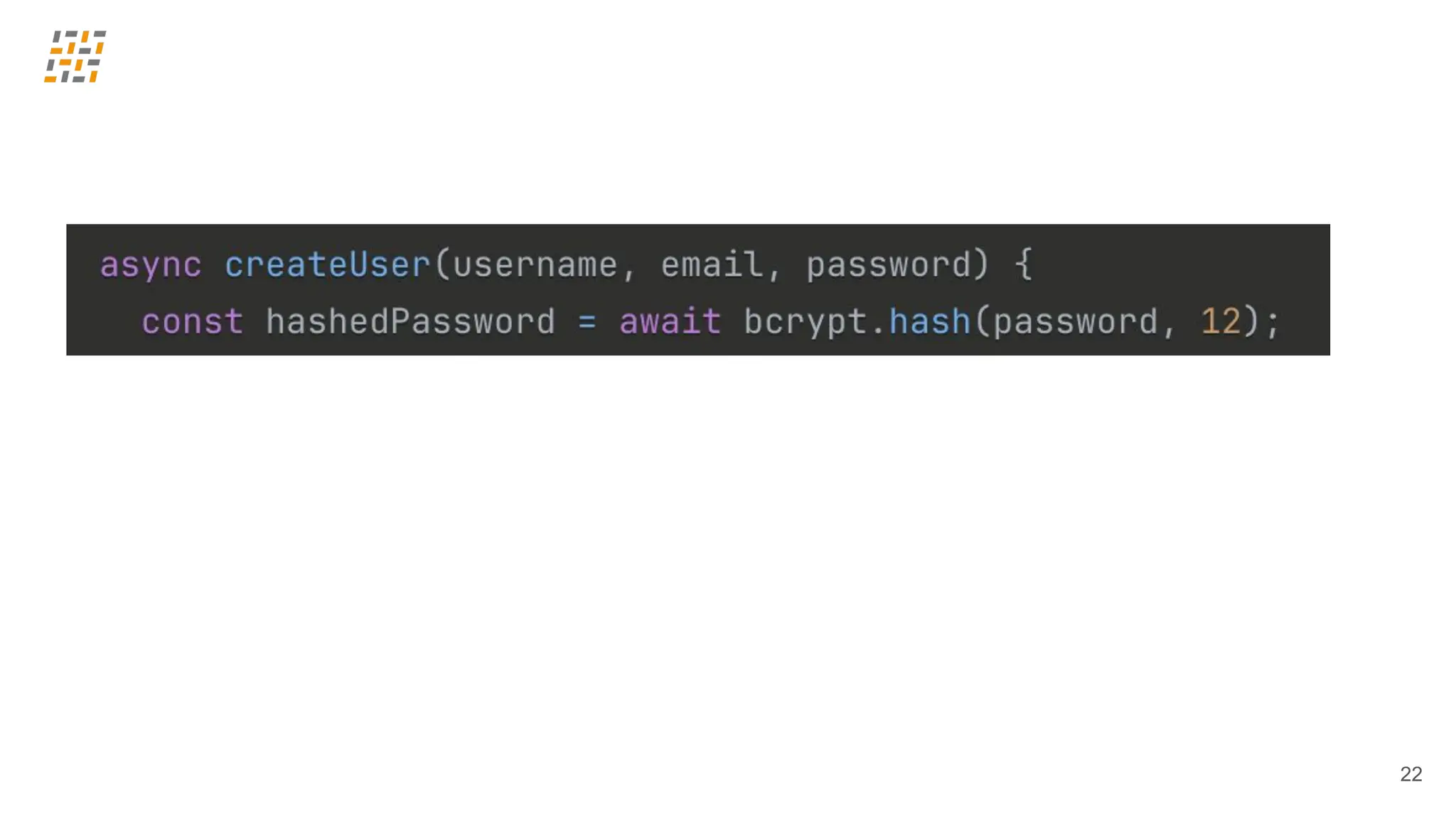
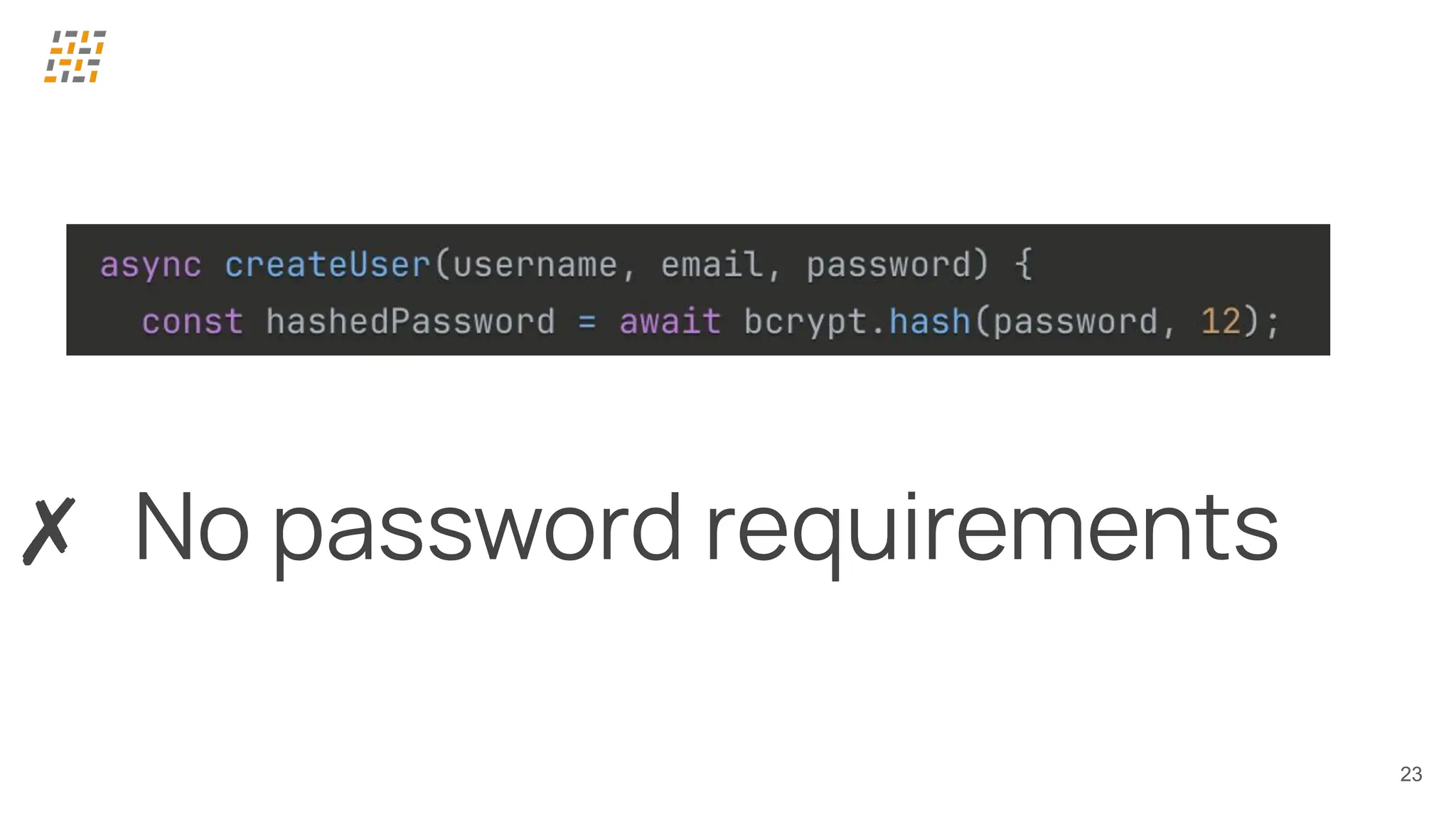
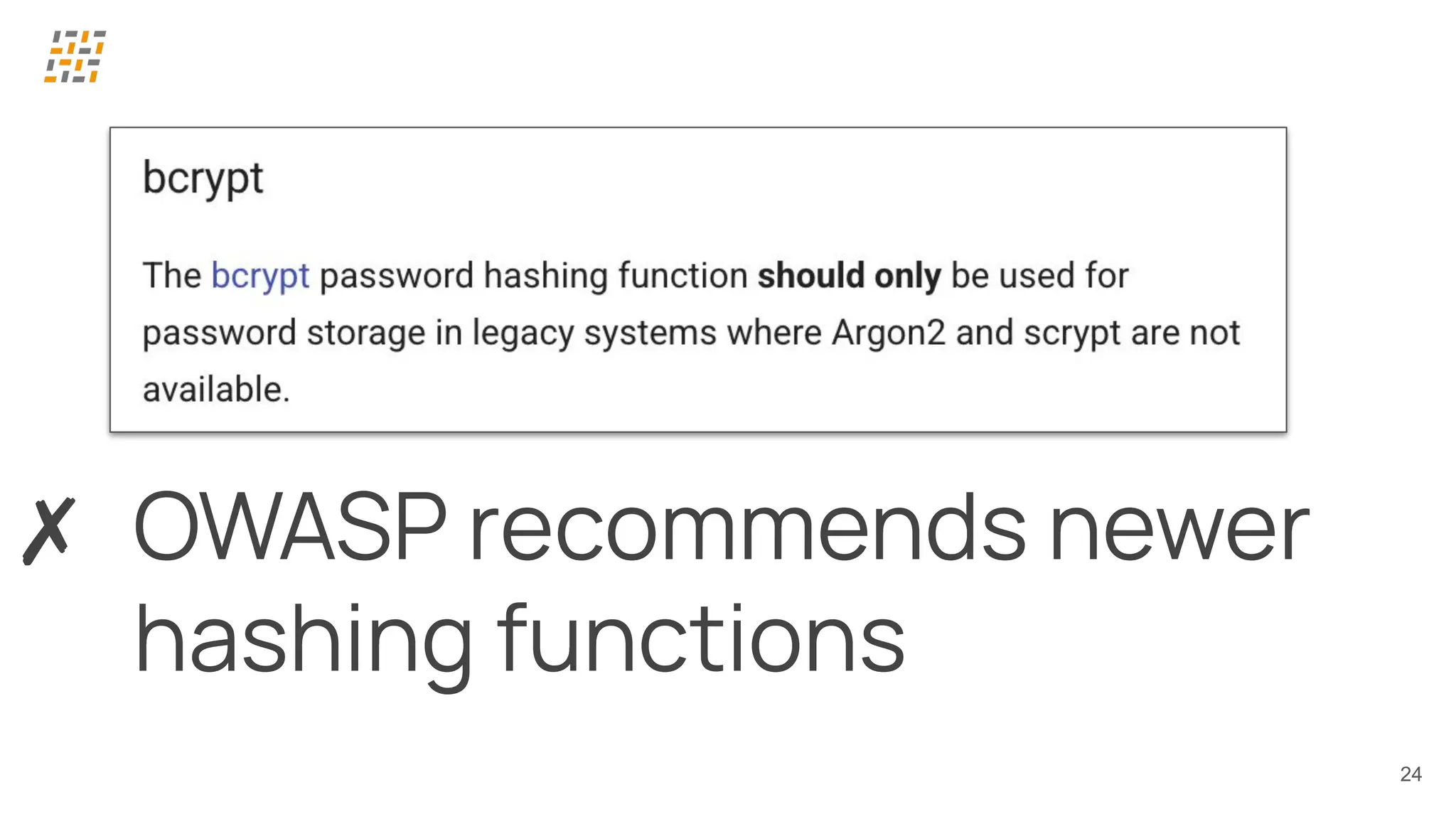
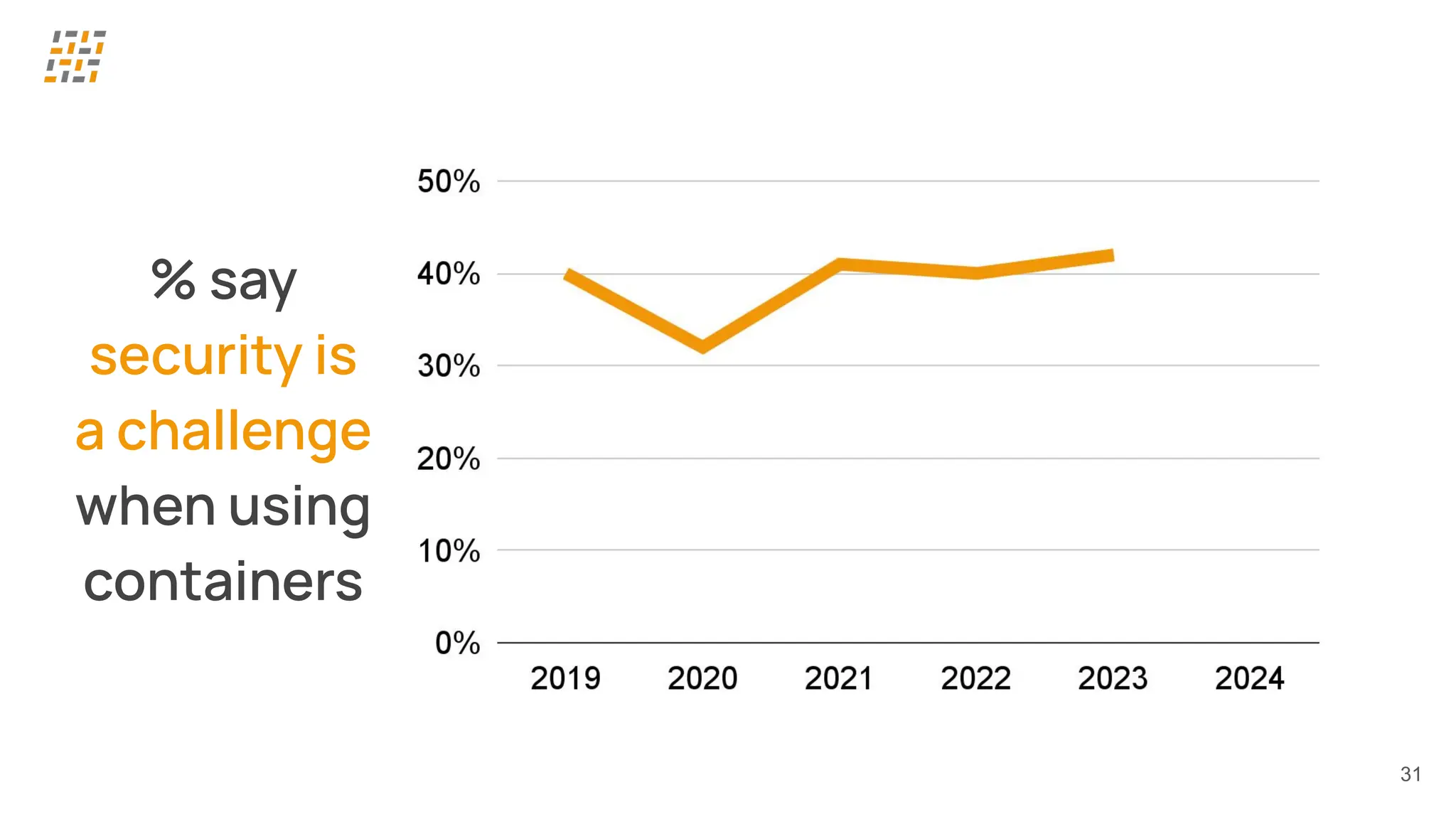
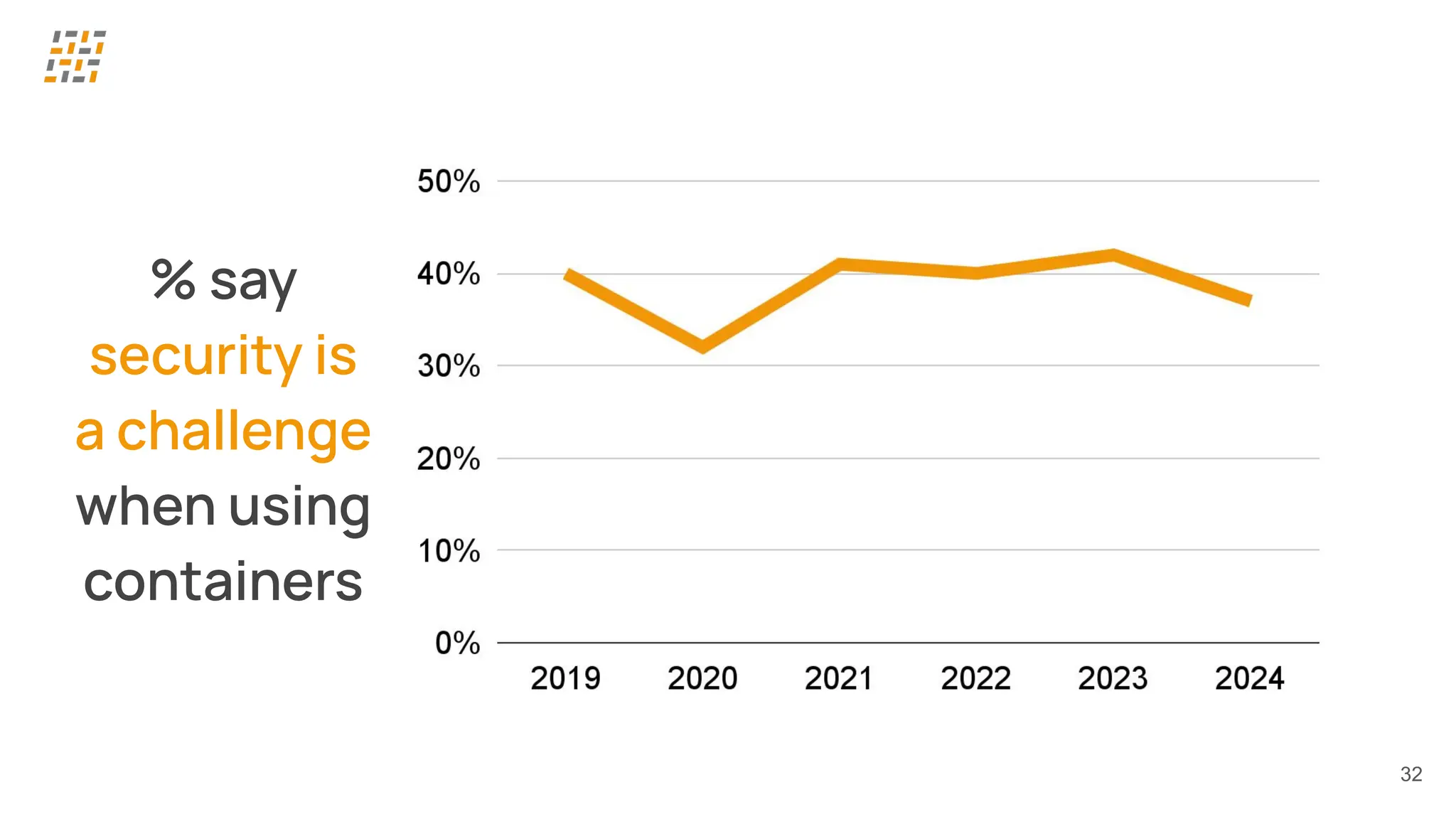
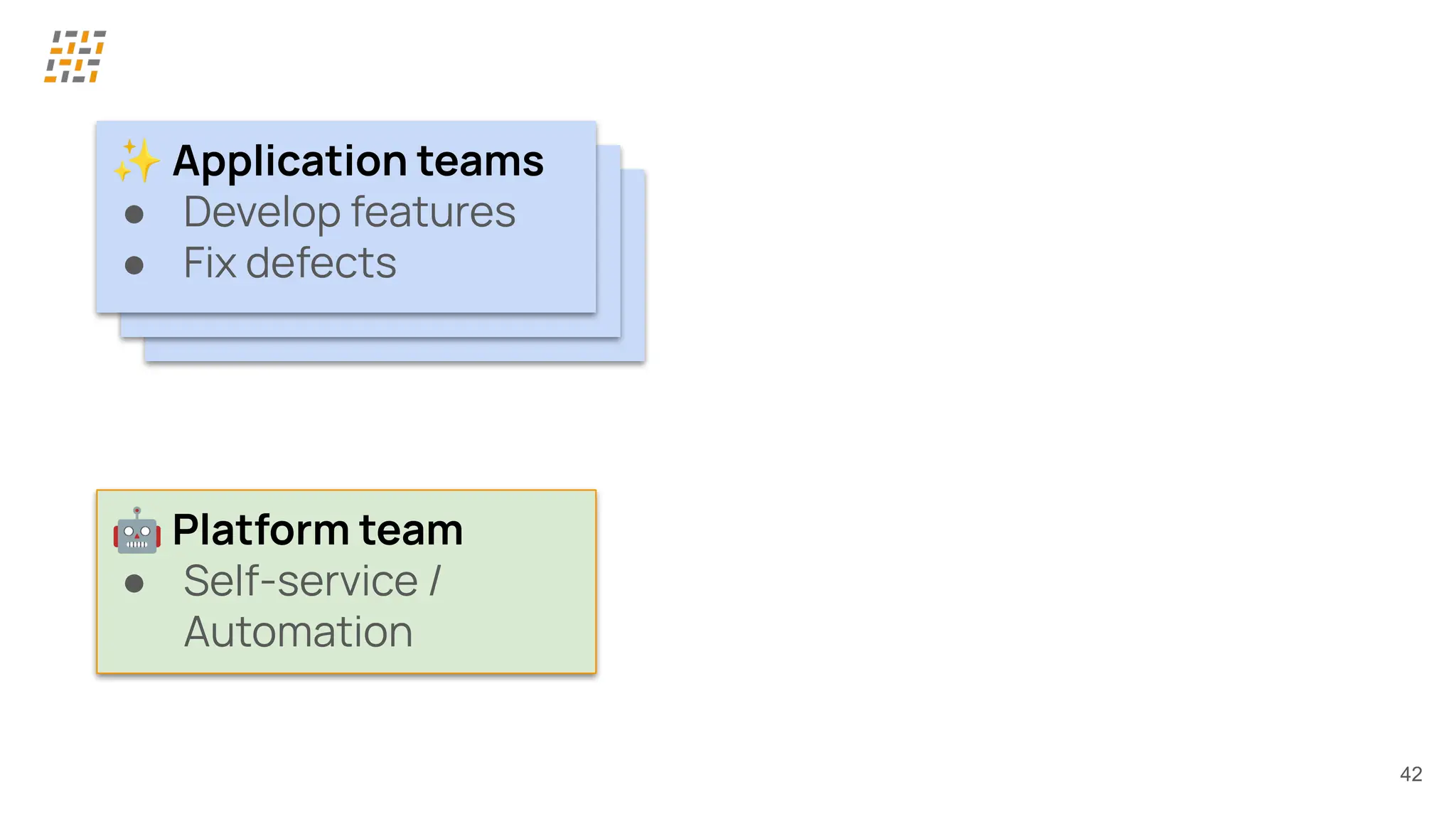
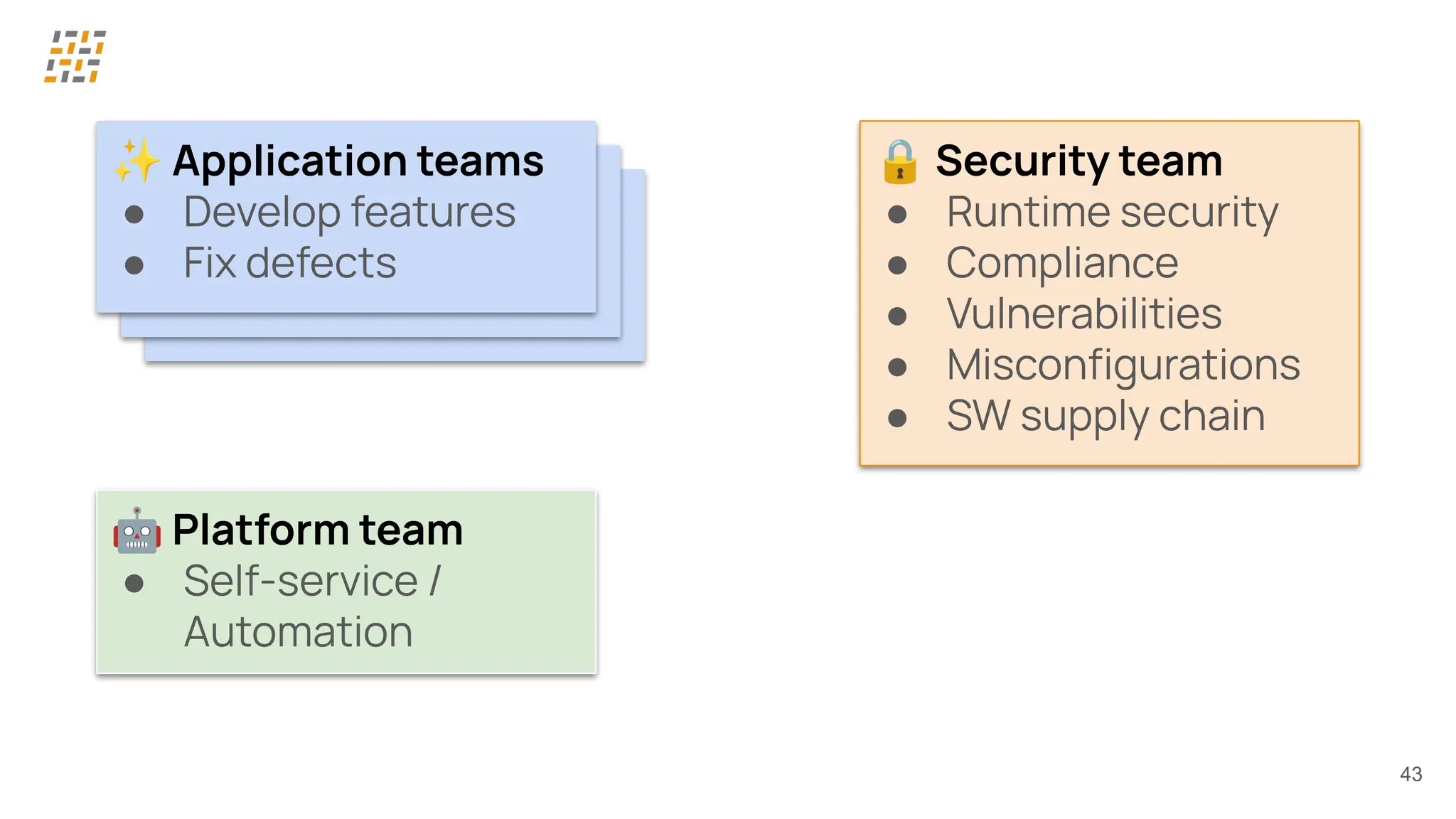
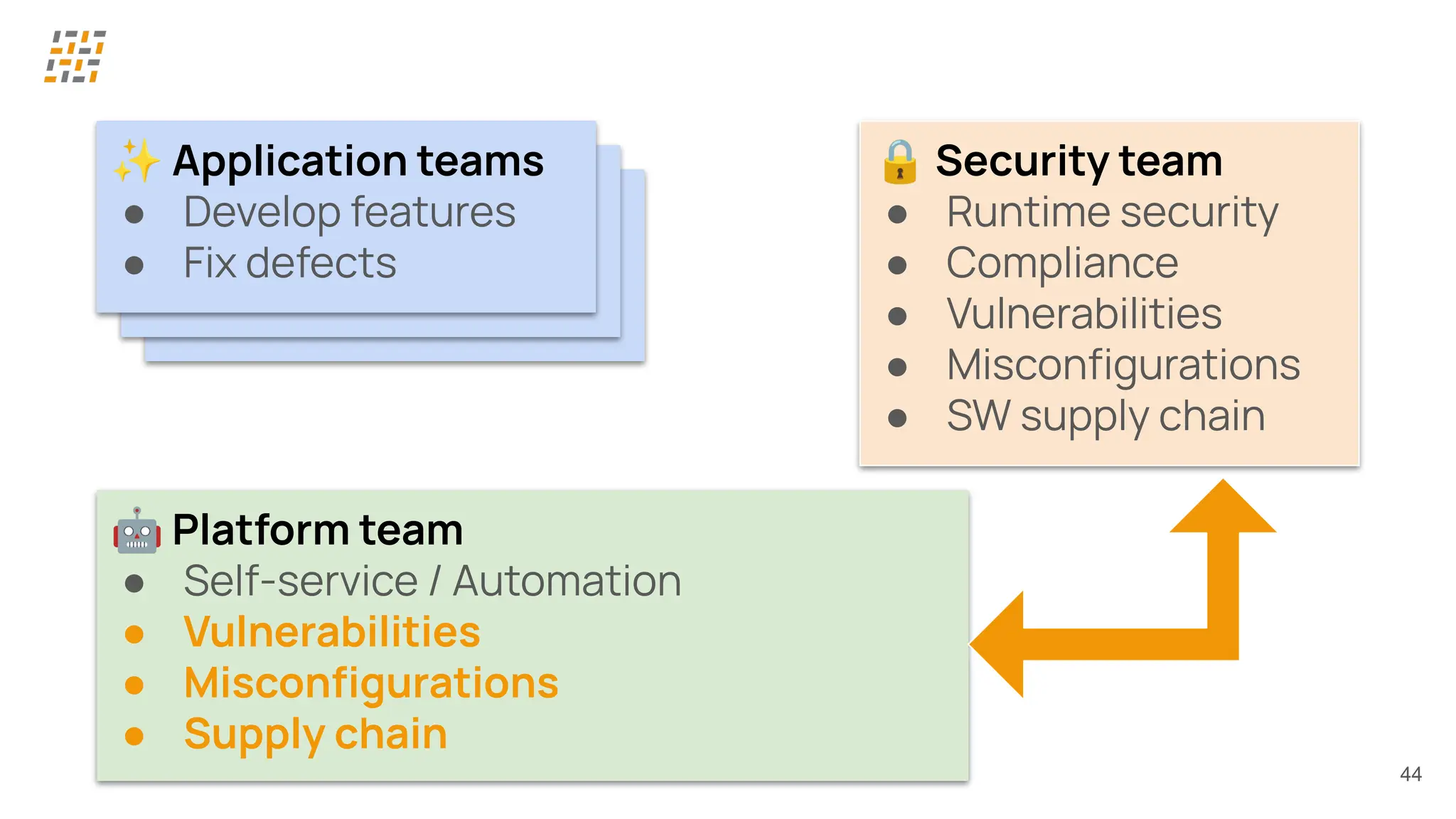
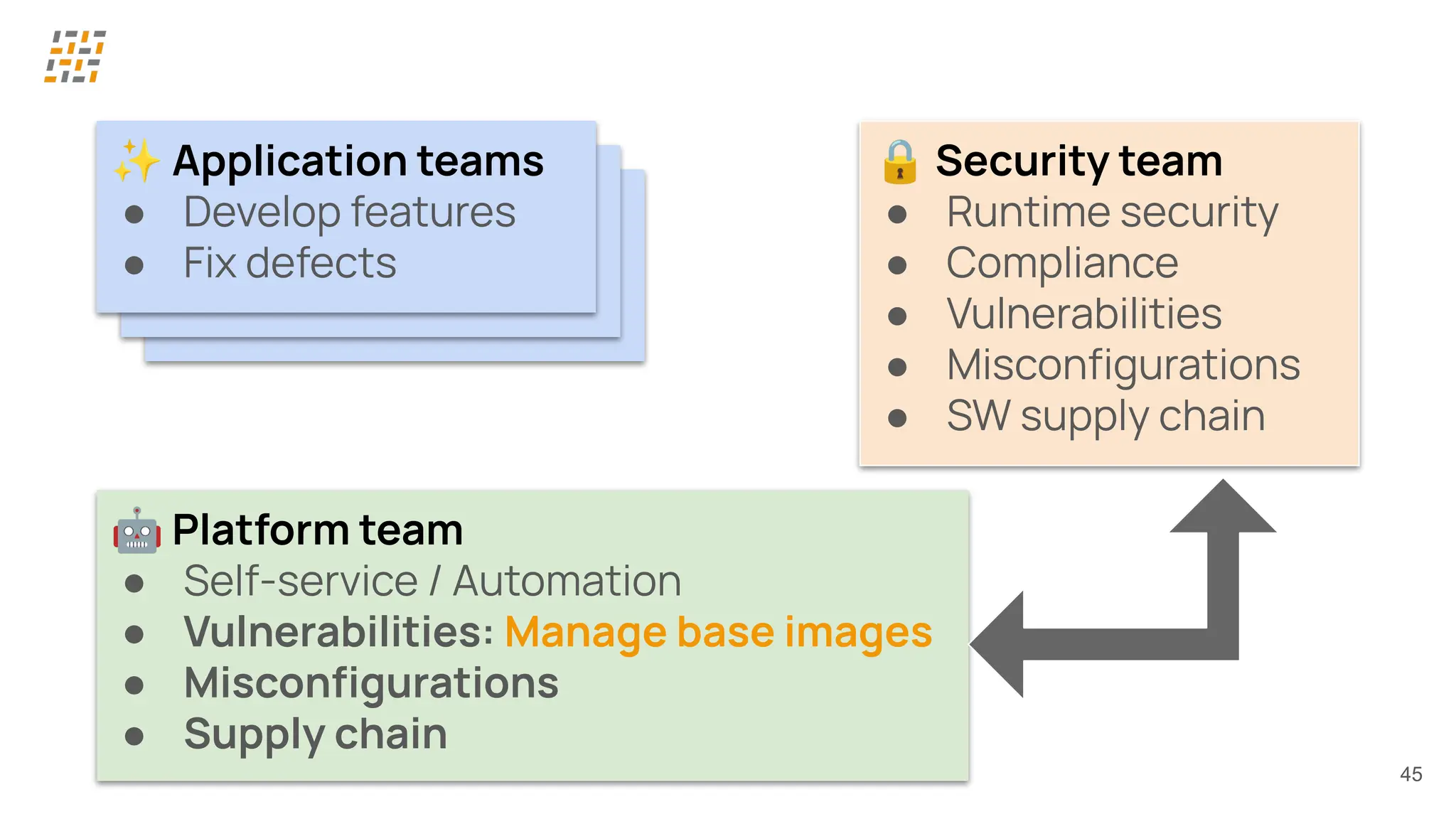
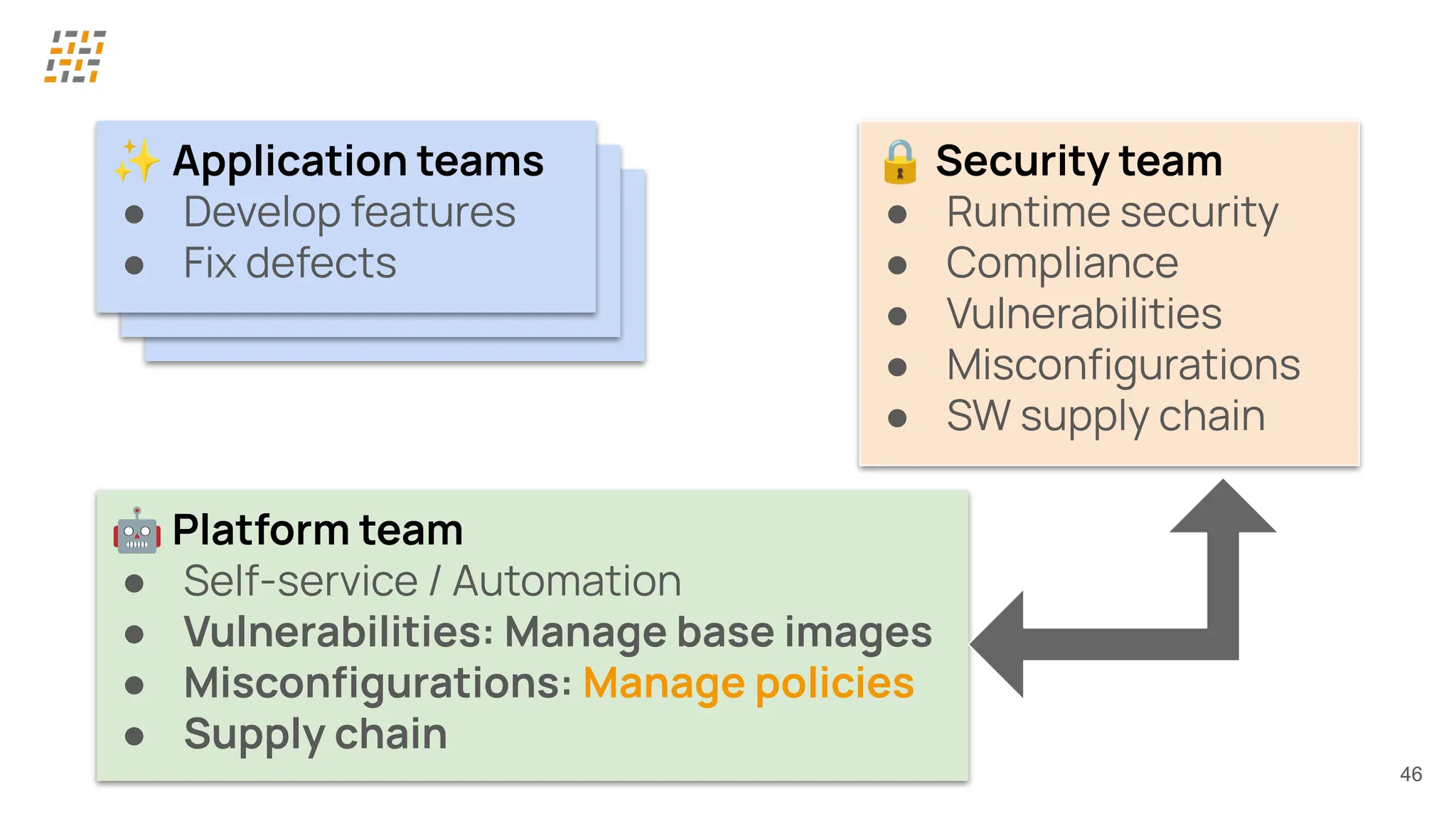
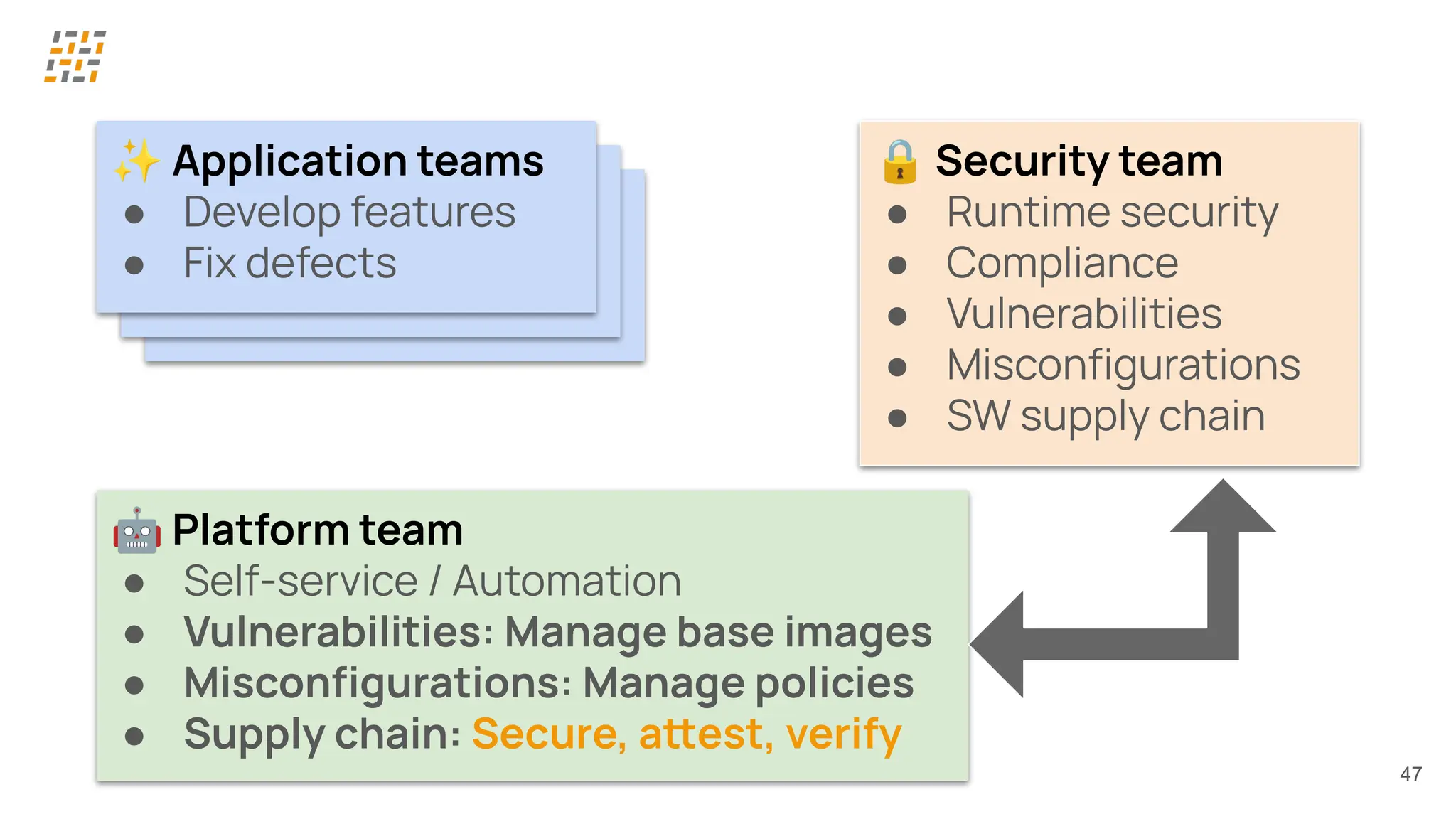
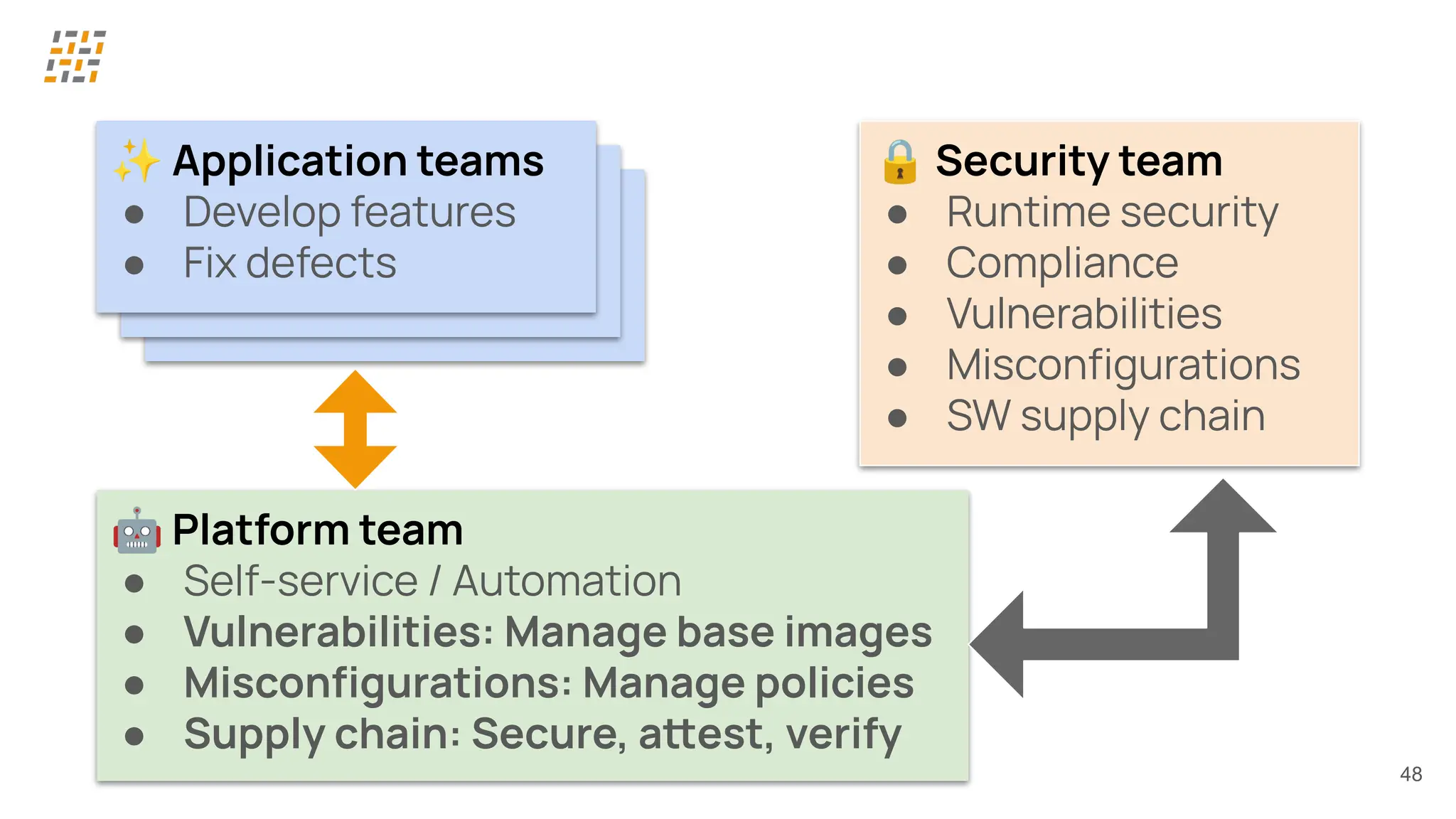
Customer identity and access management (CIAM) has become a critical component in handling complex identity needs in human-AI-machine ecosystems, making it essential for modern application architectures.
Building CIAM is a fine balance between user experience (social login, single sign-on, multi-factor authentication, biometrics), security and regulatory standards (risk-based authentication, GDPR, audits) and scalability (distributed architectures for load balancing and high availability, analytics).
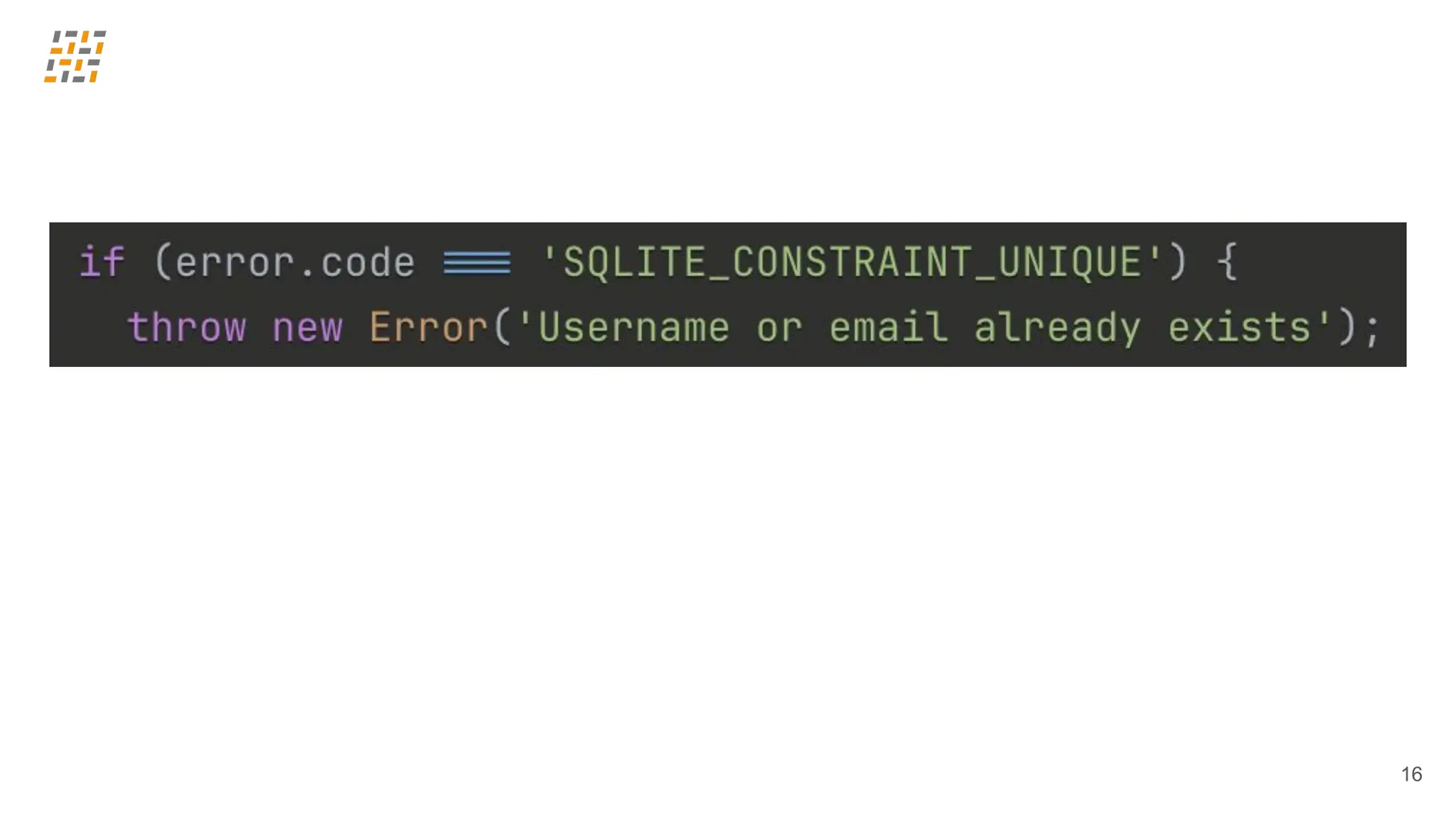
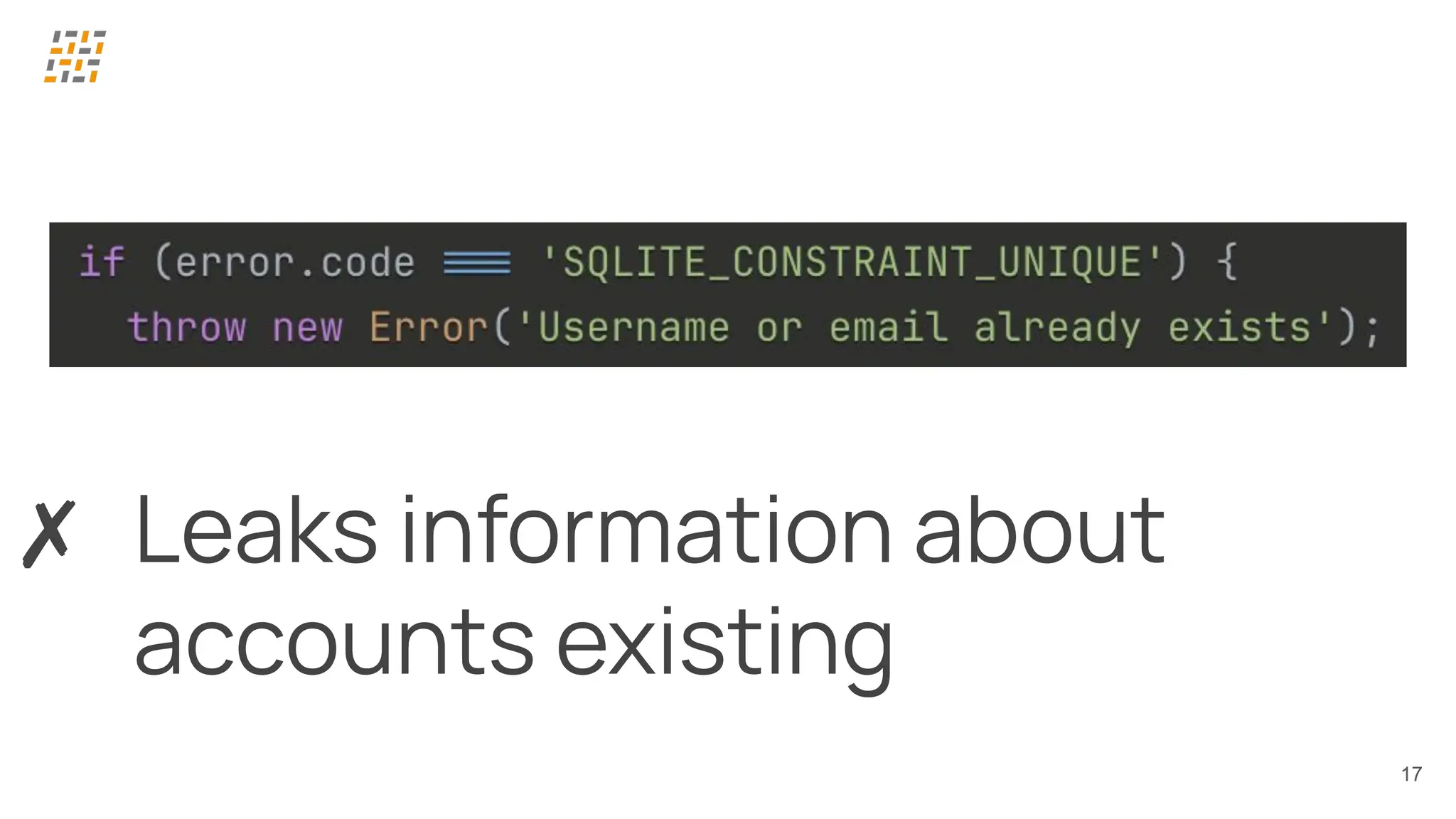
Can vibe coding handle the challenge? In this talk we’ll see how far we can push the limits – anything could happen…