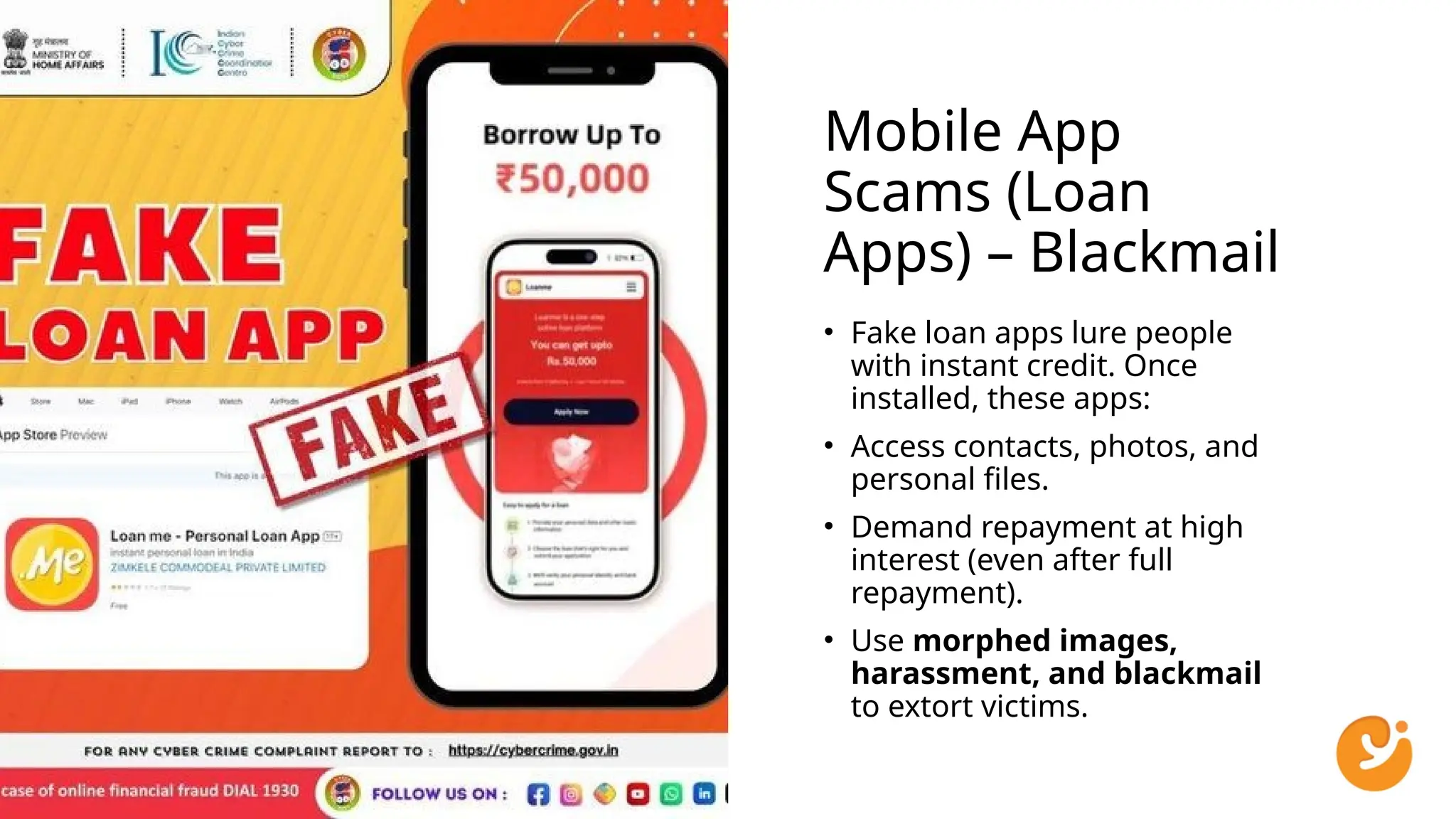
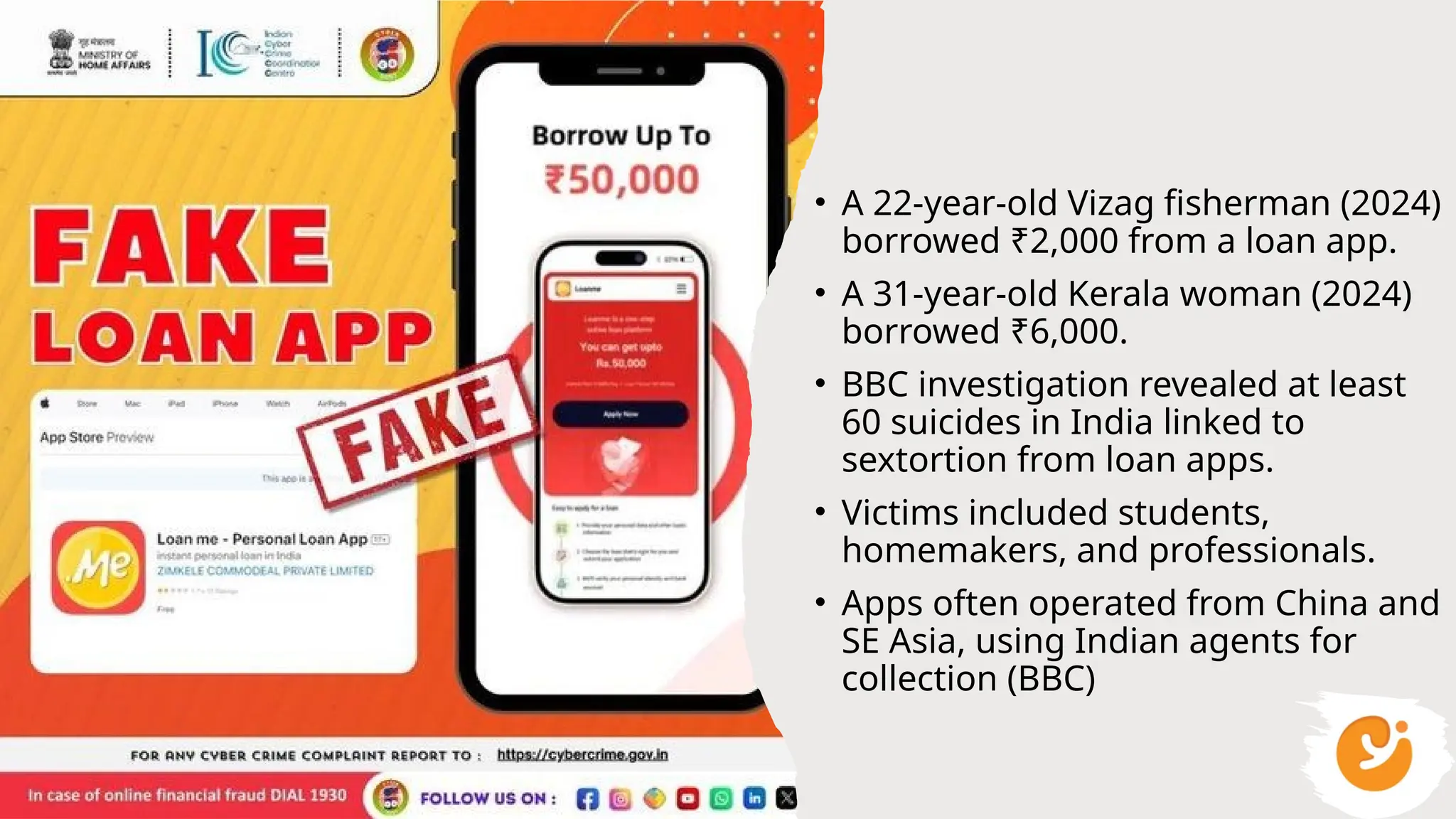
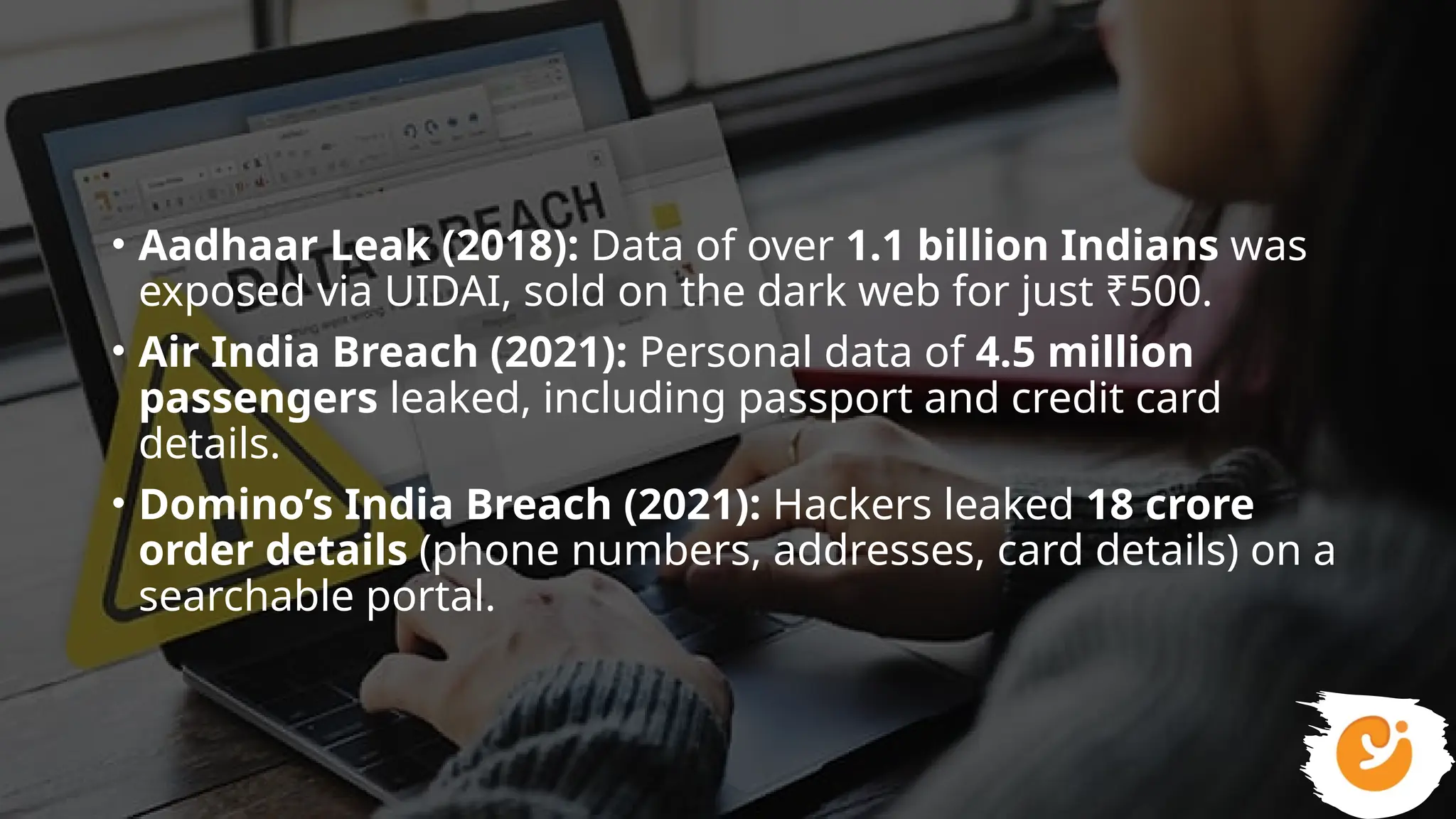
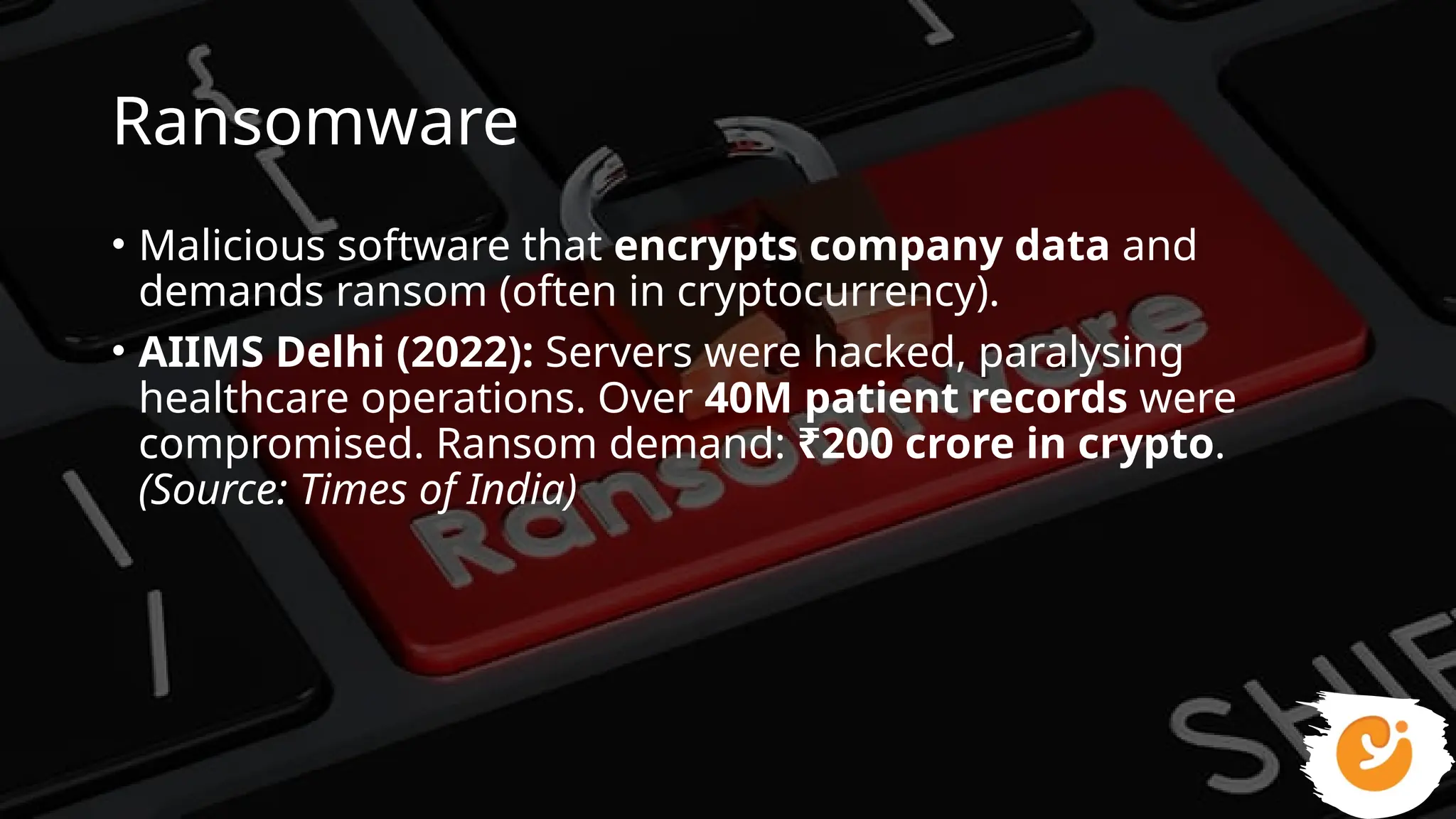
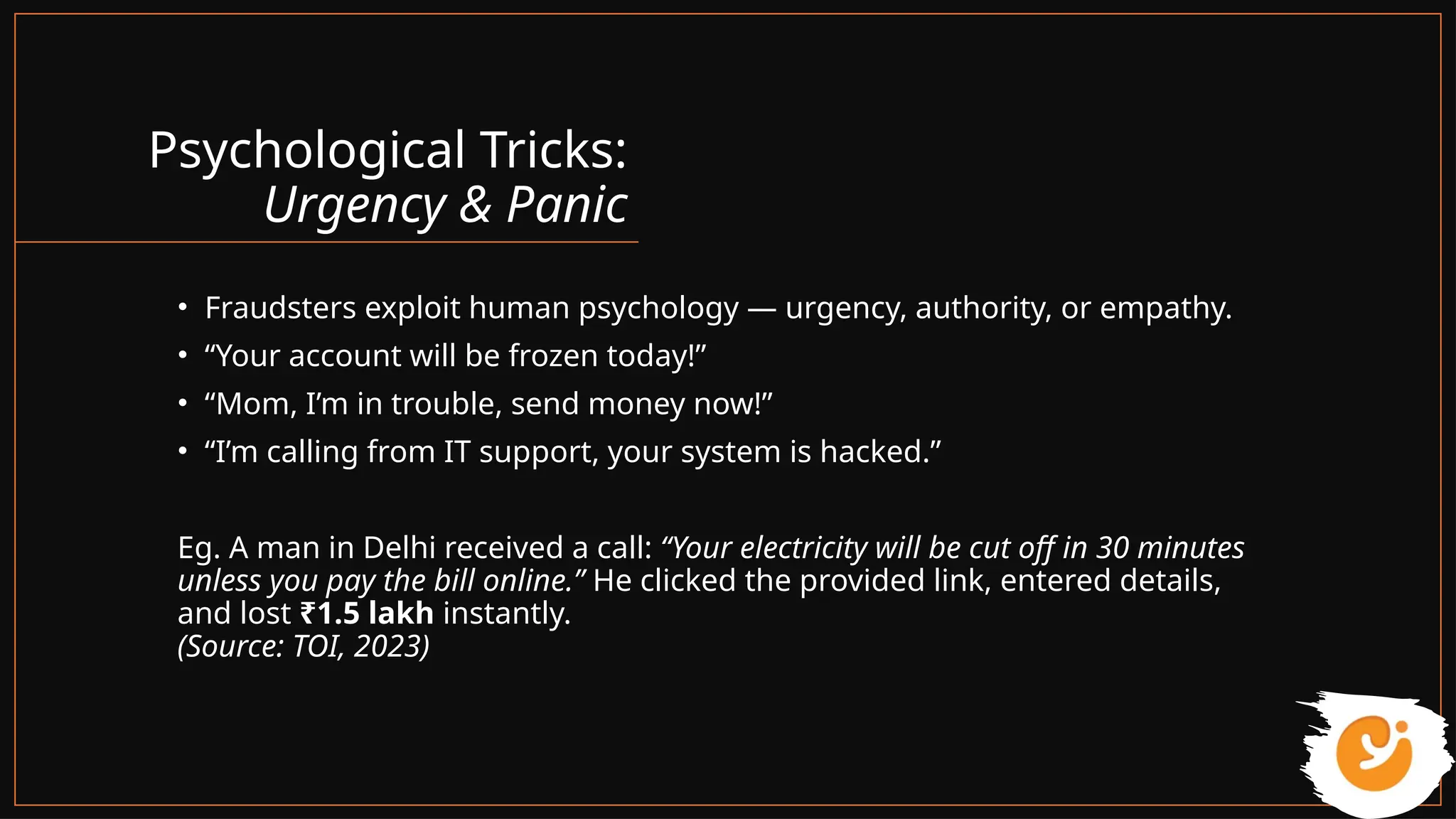
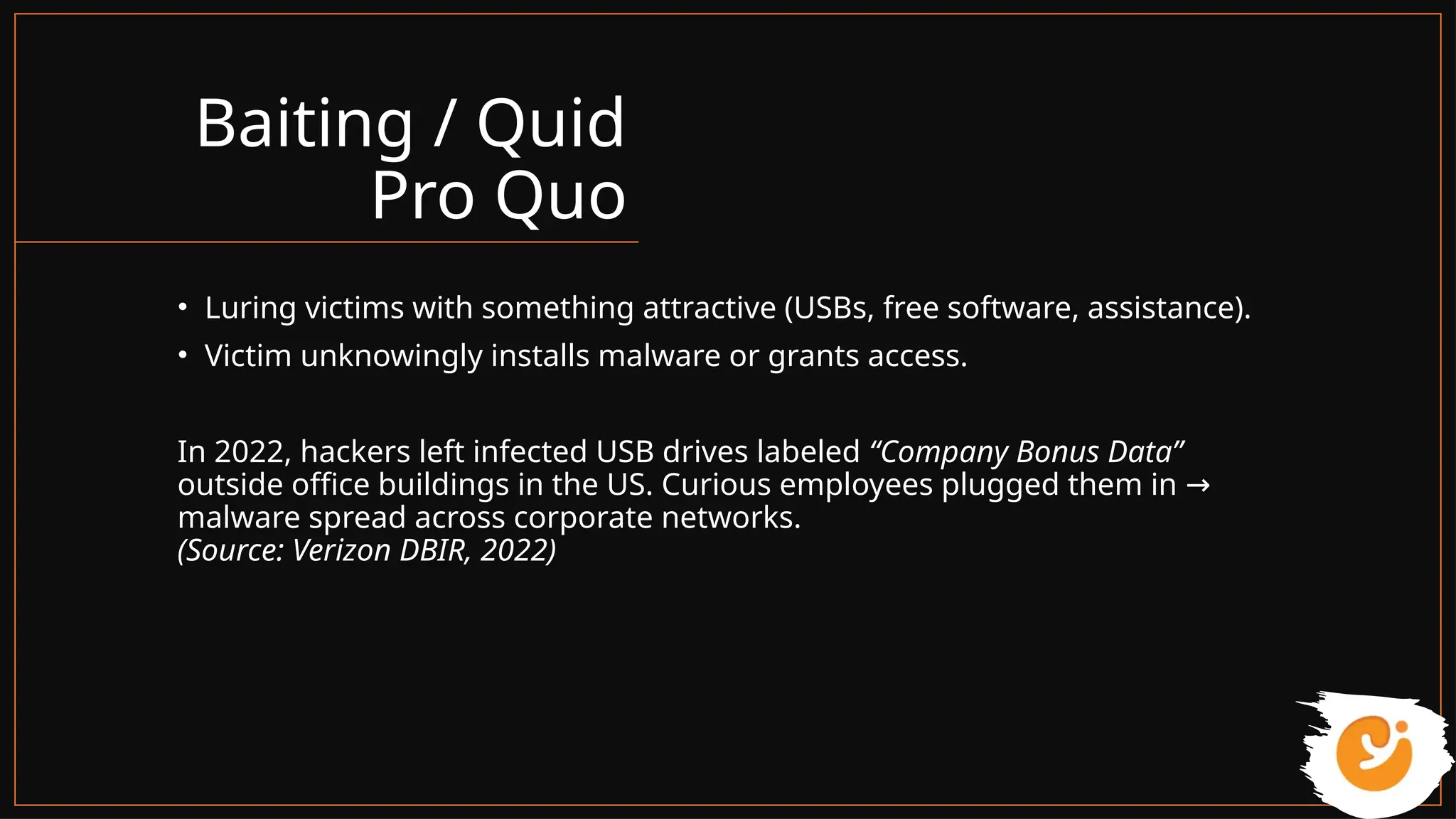
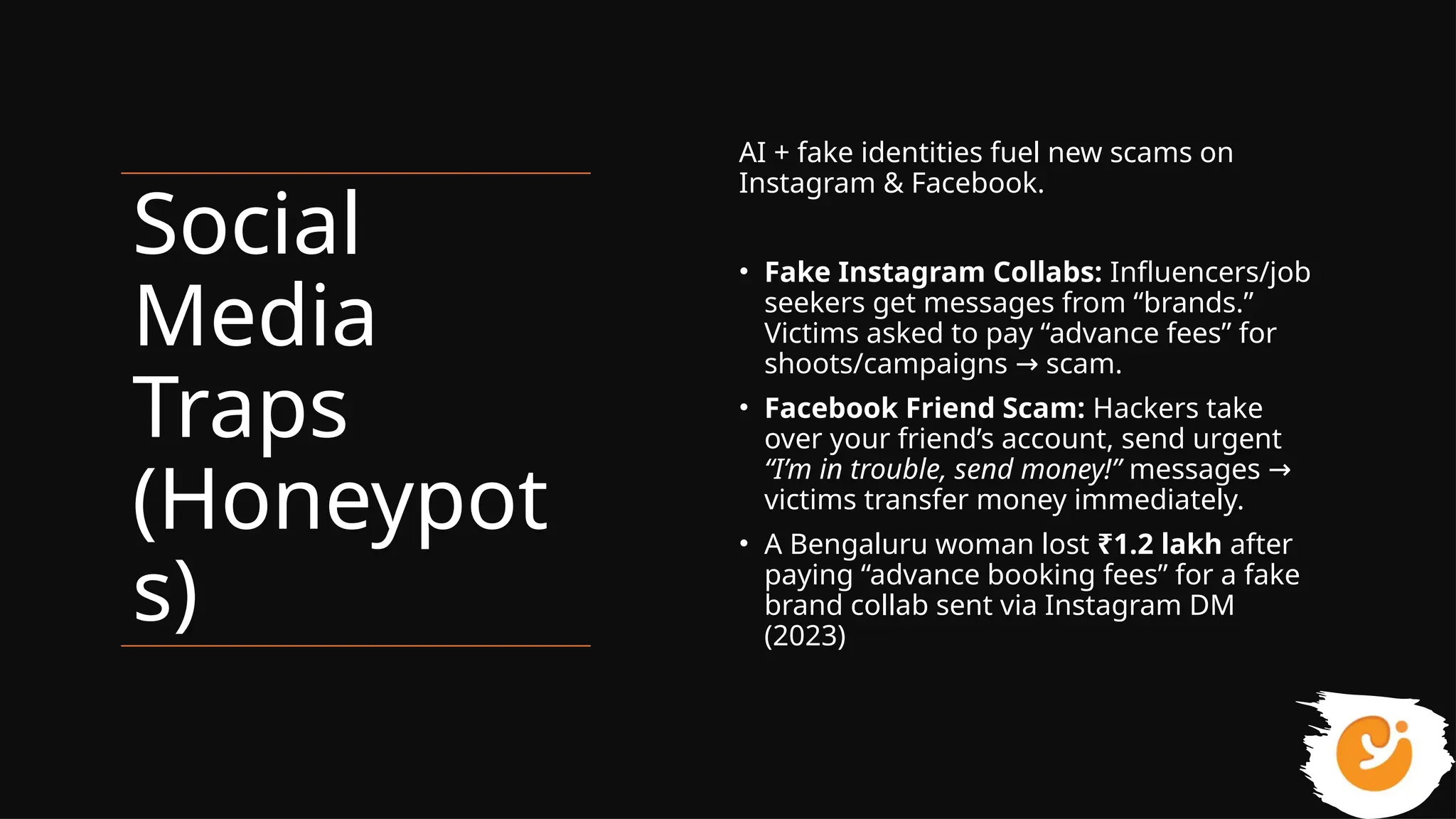
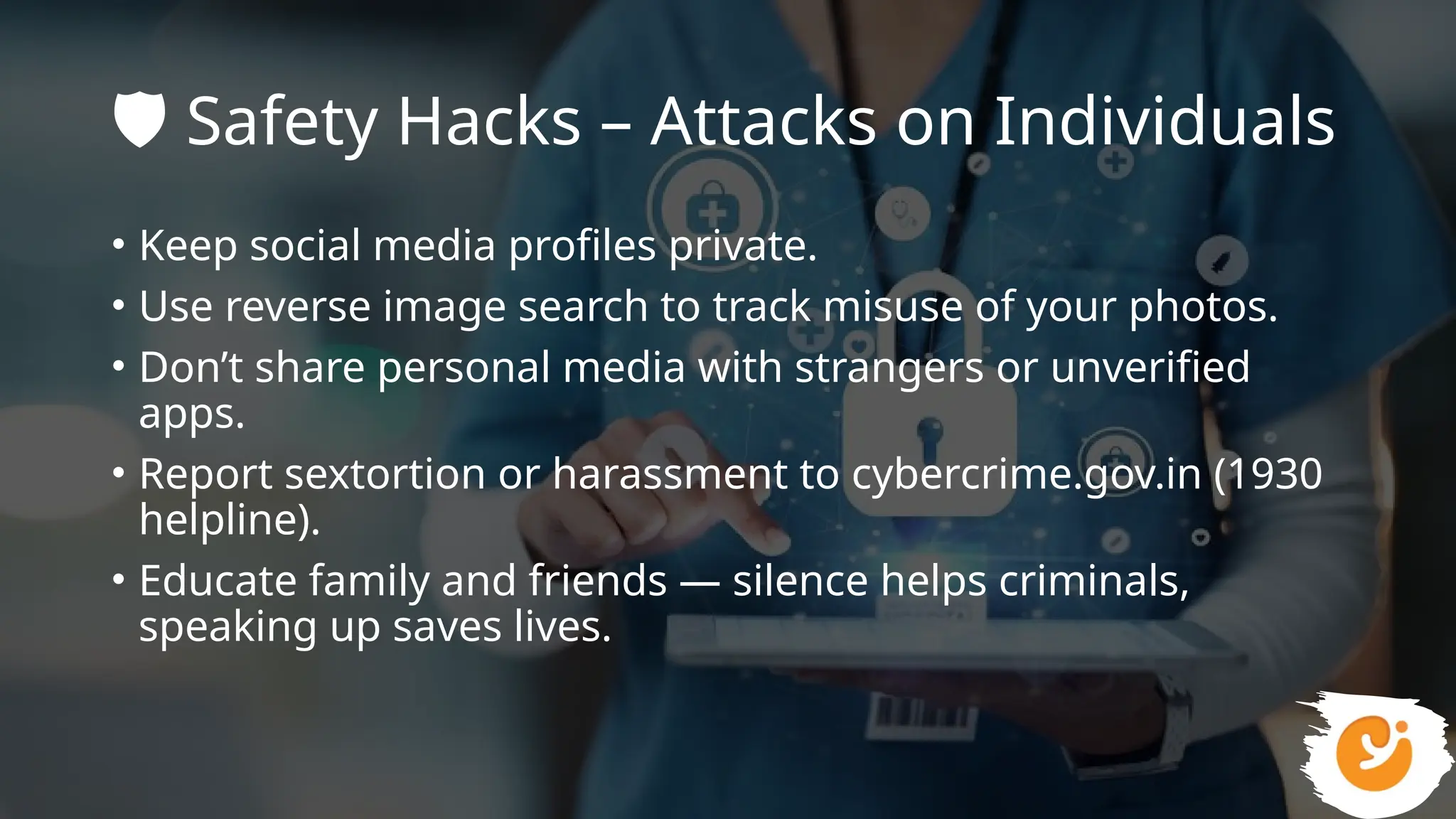
This presentation gives a clear and practical overview of cybercrime, online scams, and essential safety hacks for 2025. It explains the major digital threats people face today, including phishing, UPI fraud, fake loan apps, SIM swap attacks, deepfake harassment, ransomware, and social engineering tricks.
With real case studies and easy-to-understand examples, the presentation helps students, professionals, and everyday internet users learn how to protect their money, data, social media accounts, and digital identity. It also highlights women’s online safety, privacy protection, and trusted reporting methods for cybercrime in India.
Designed for awareness and learning, this presentation empowers viewers to stay alert, identify scams early, and stay safe in the digital world.