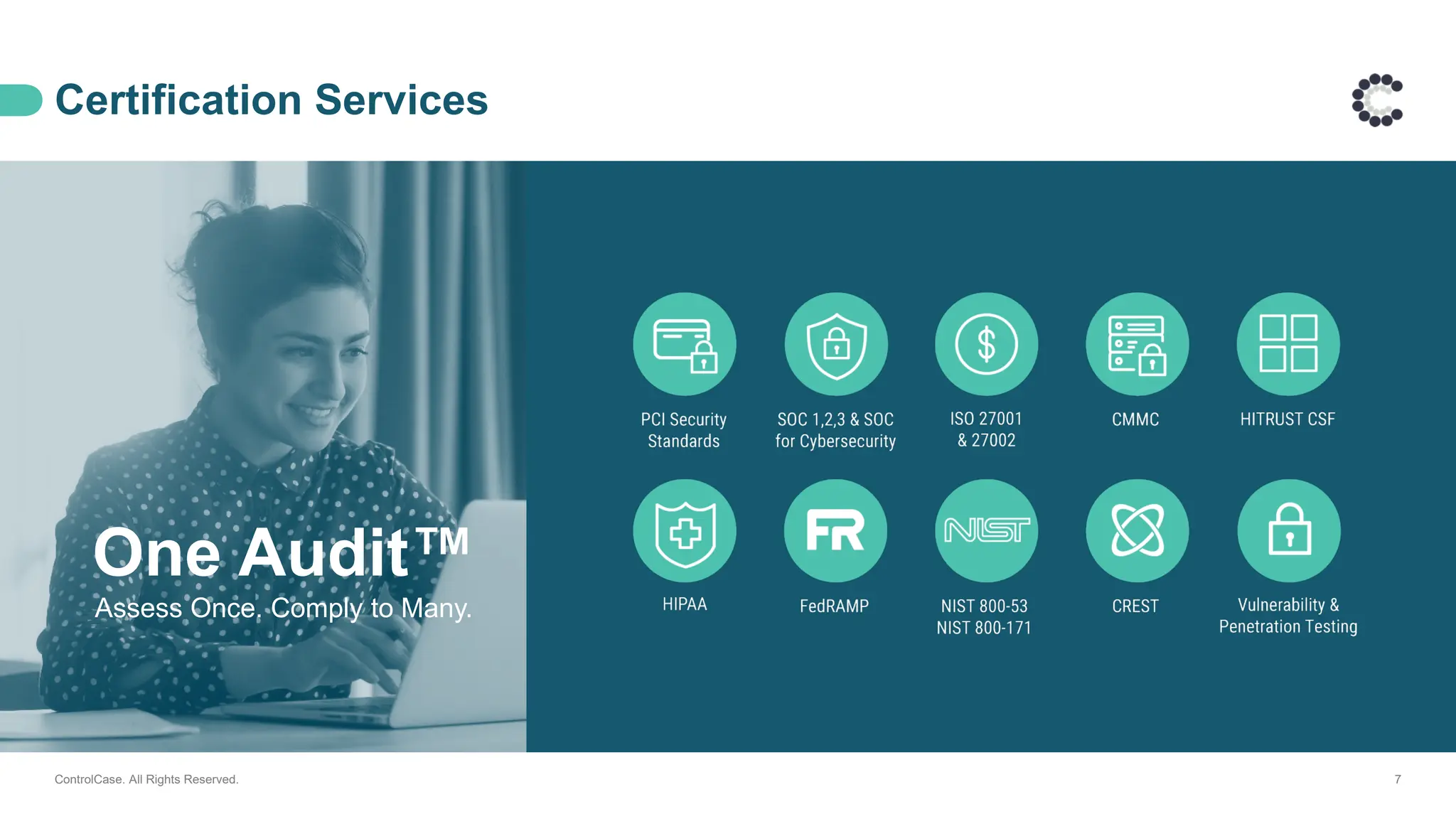
Join us for an exclusive webinar on Logging and Automated Alerting — your key to simplifying compliance and strengthening security.
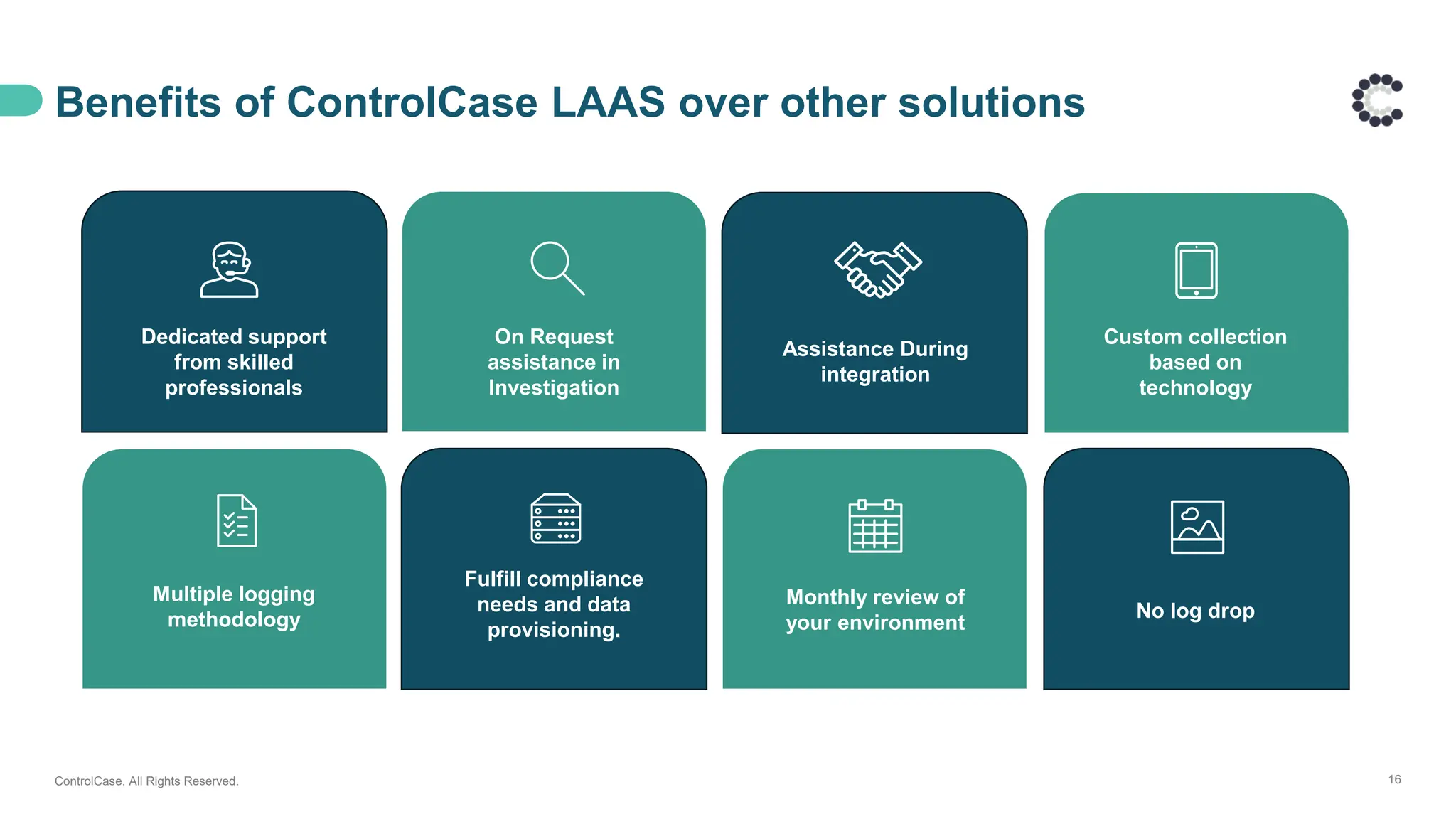
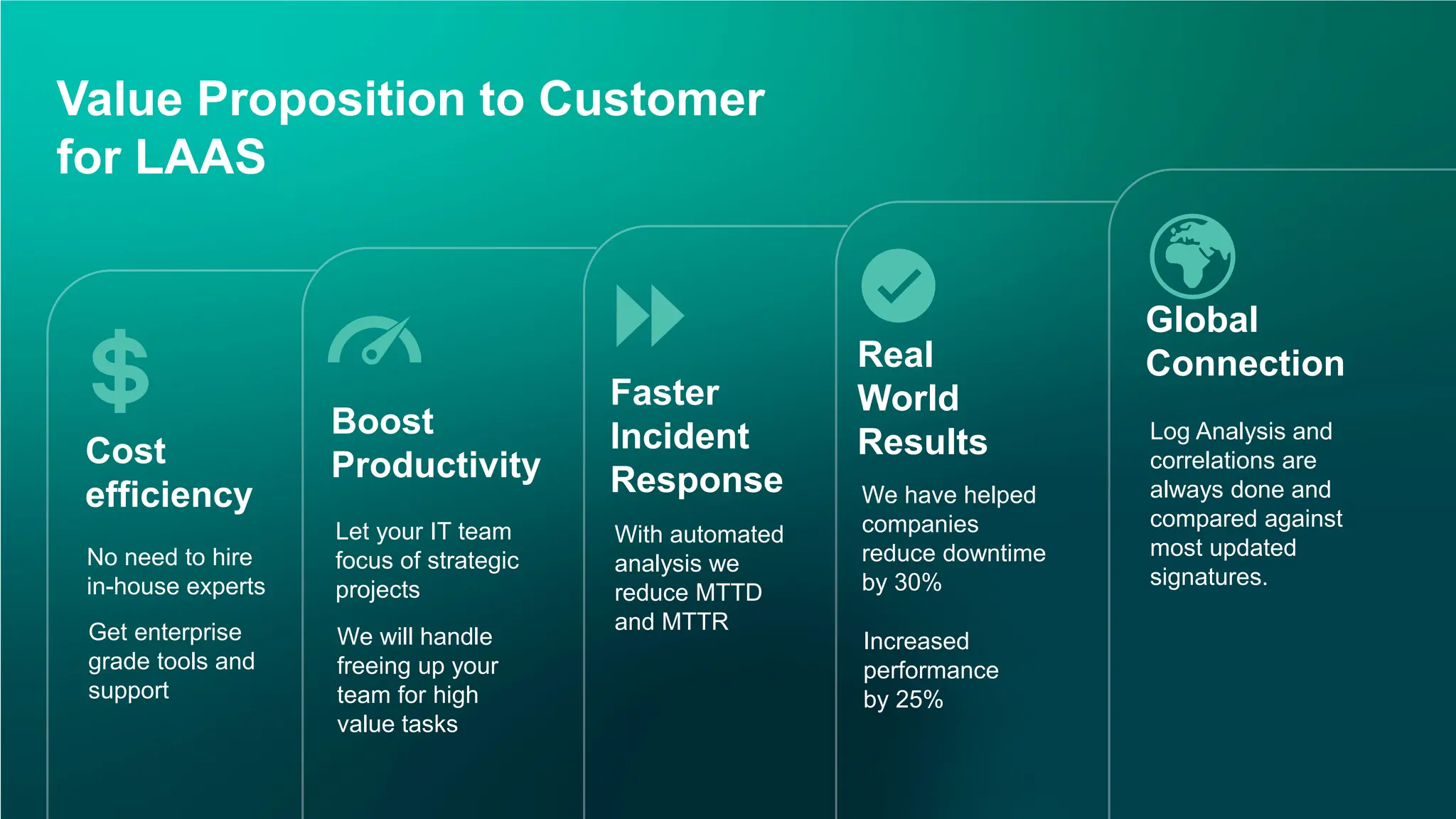
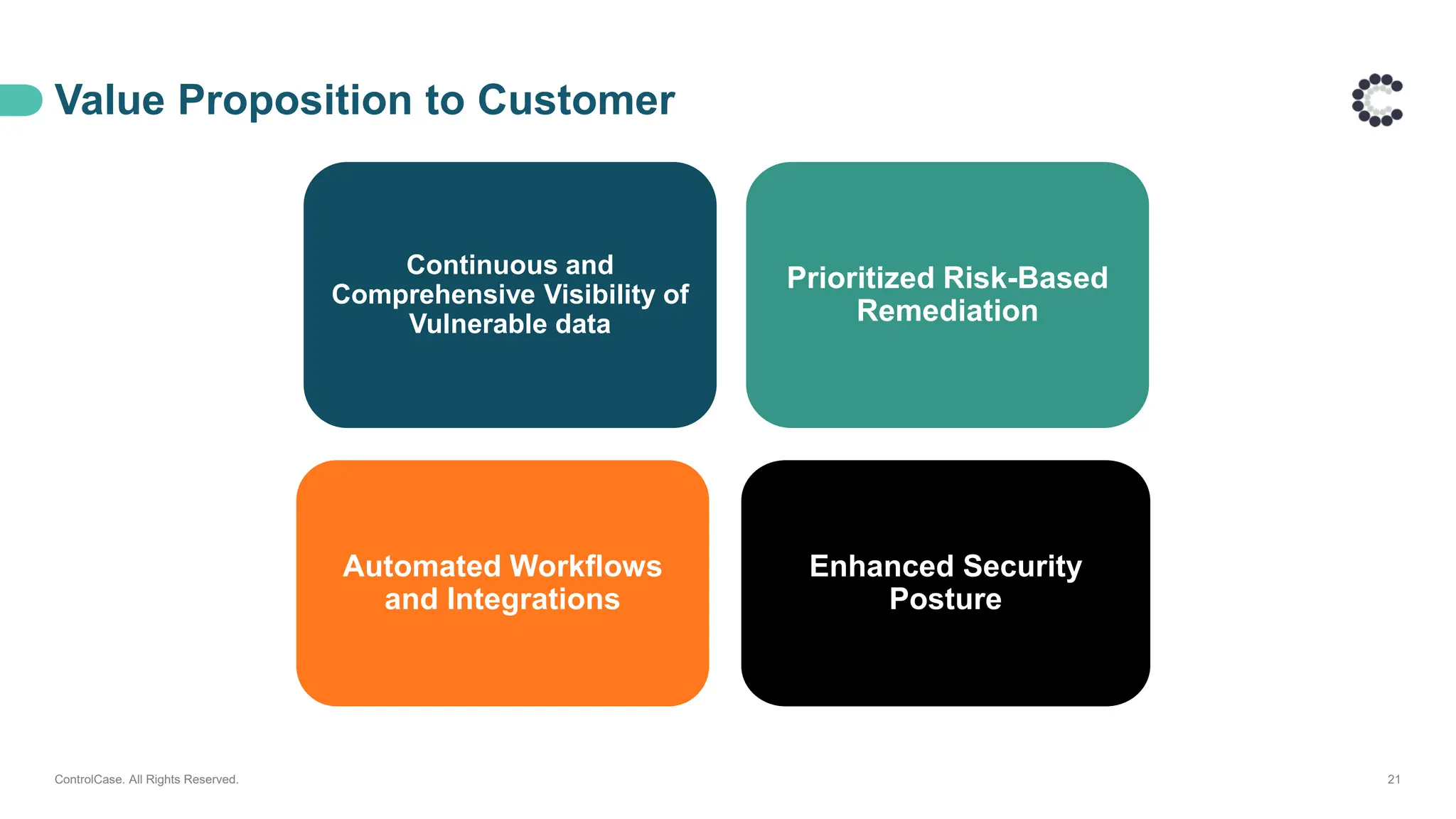
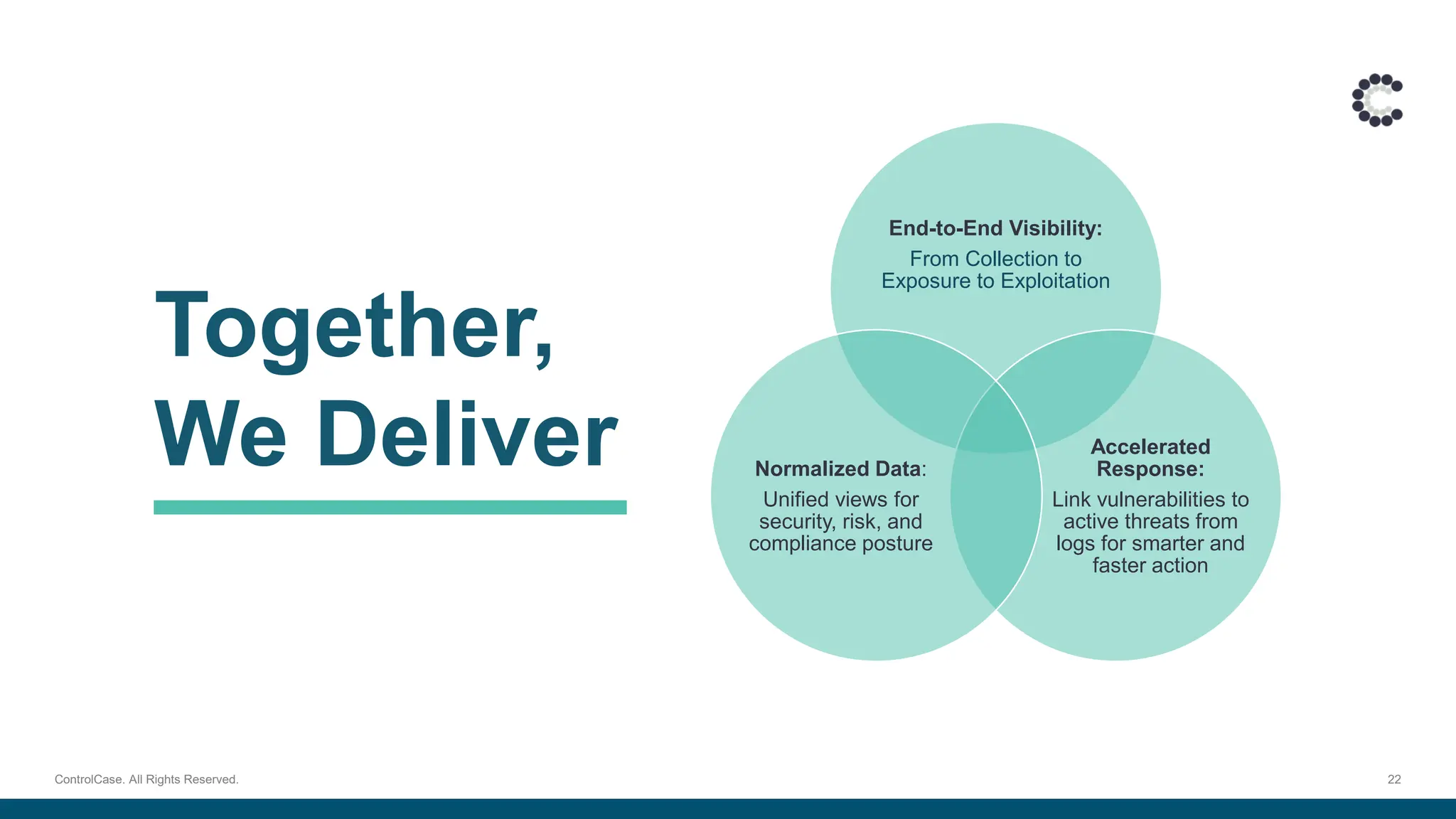
Discover how ControlCase helps organizations move beyond the checklist to achieve real-time monitoring, centralized log management, and faster incident response with minimal internal effort.
📅 Gain insights into:
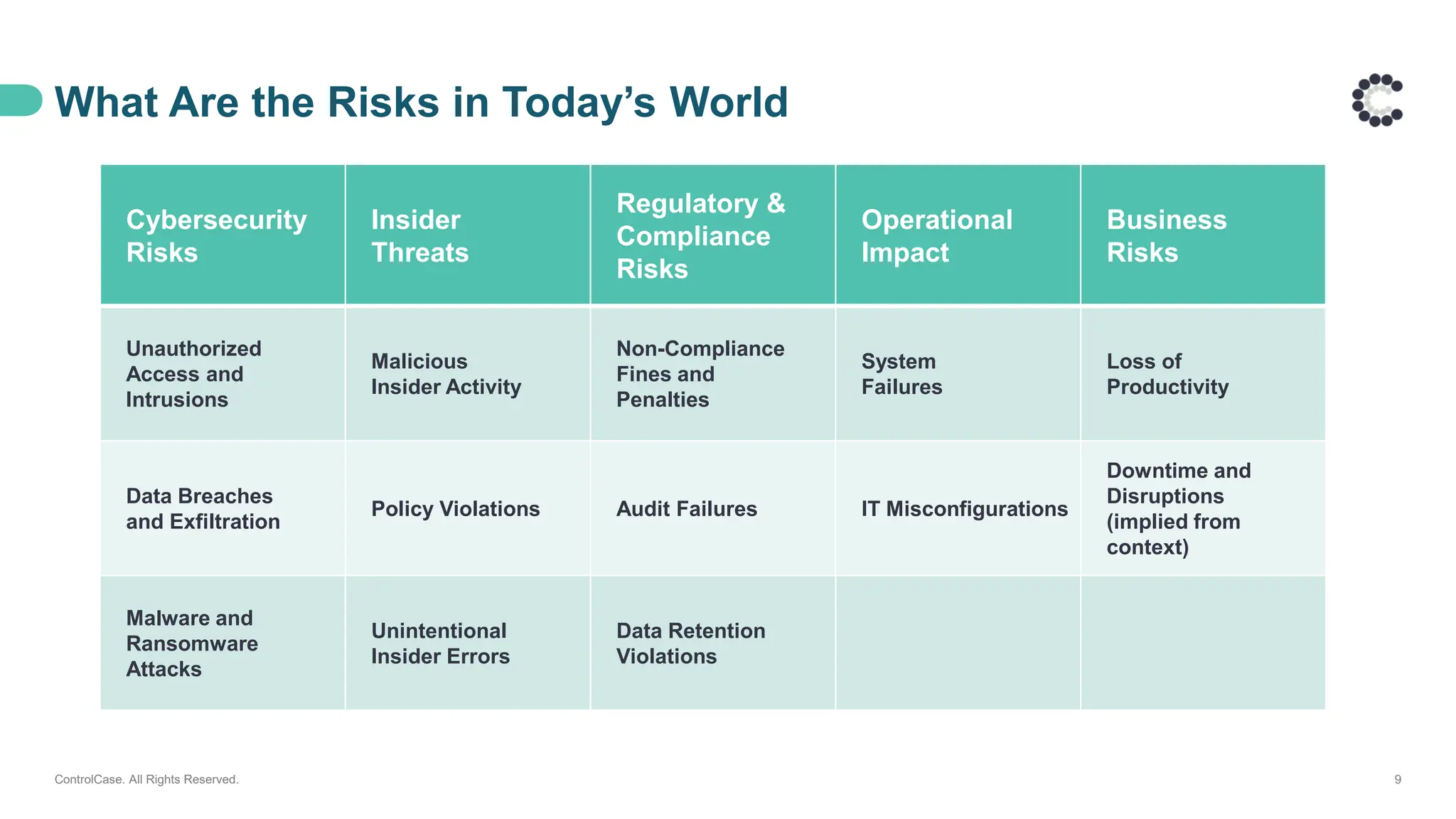
• Emerging risks and compliance requirements
• How automated alerting reduces downtime
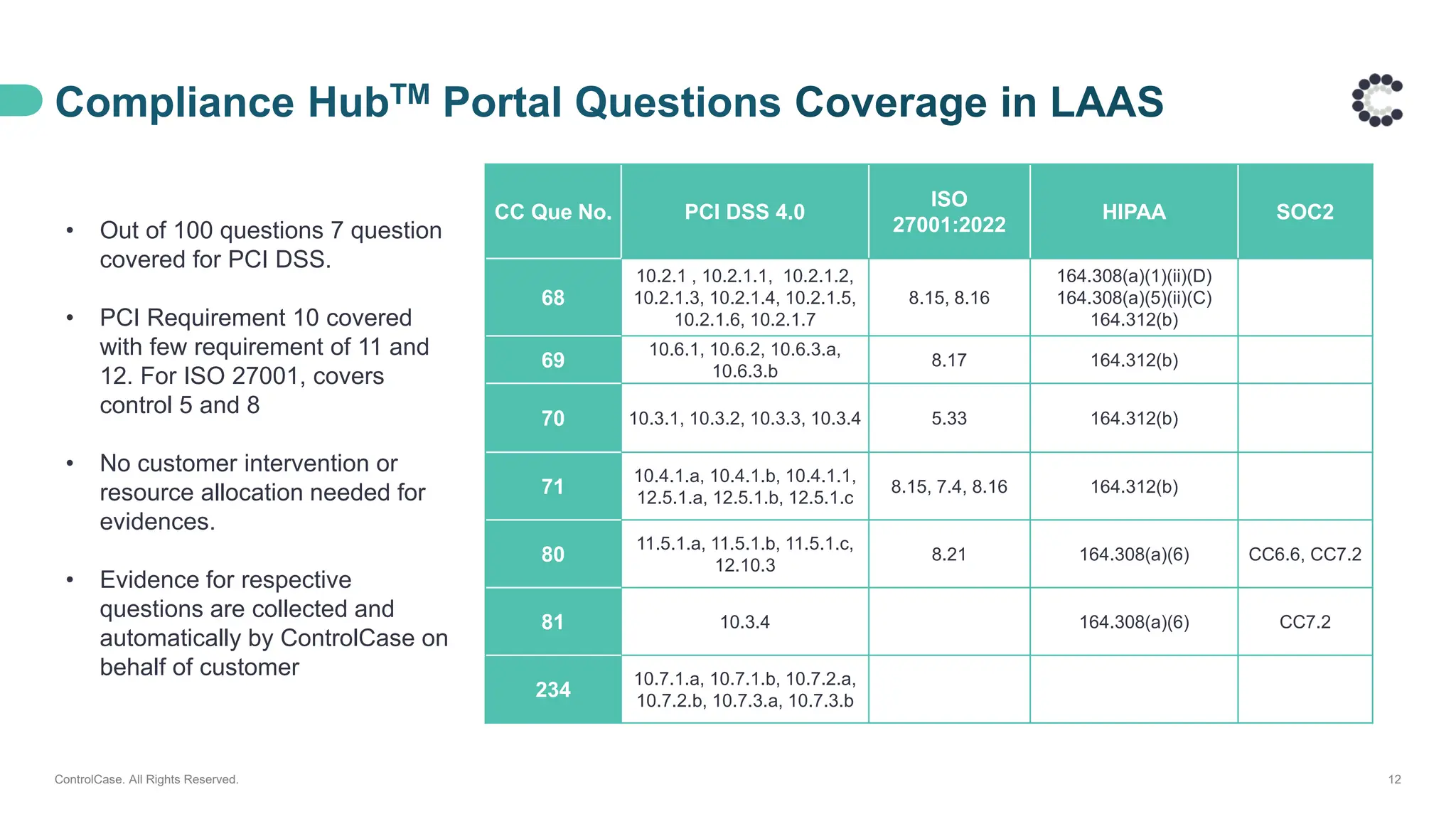
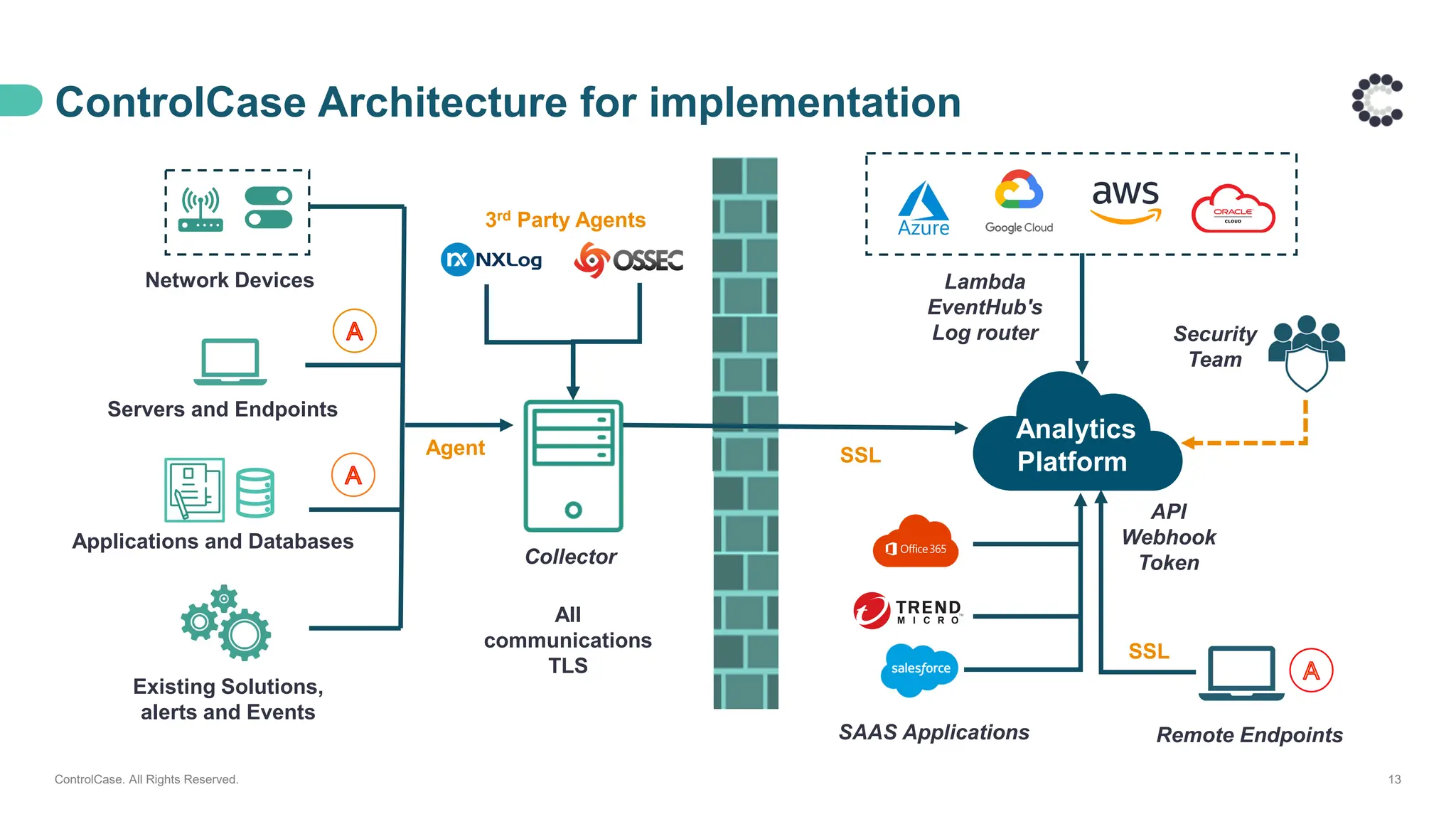
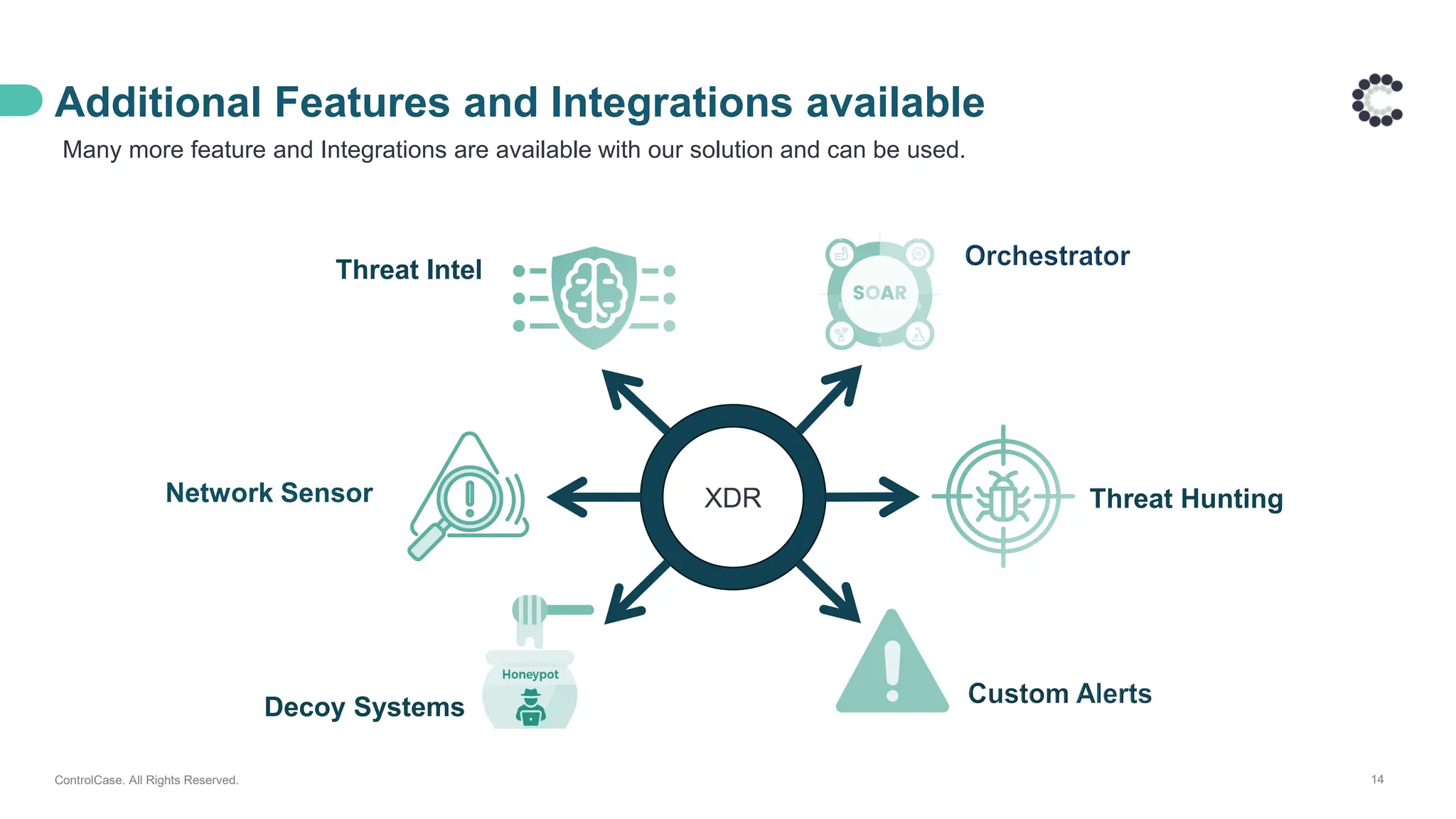
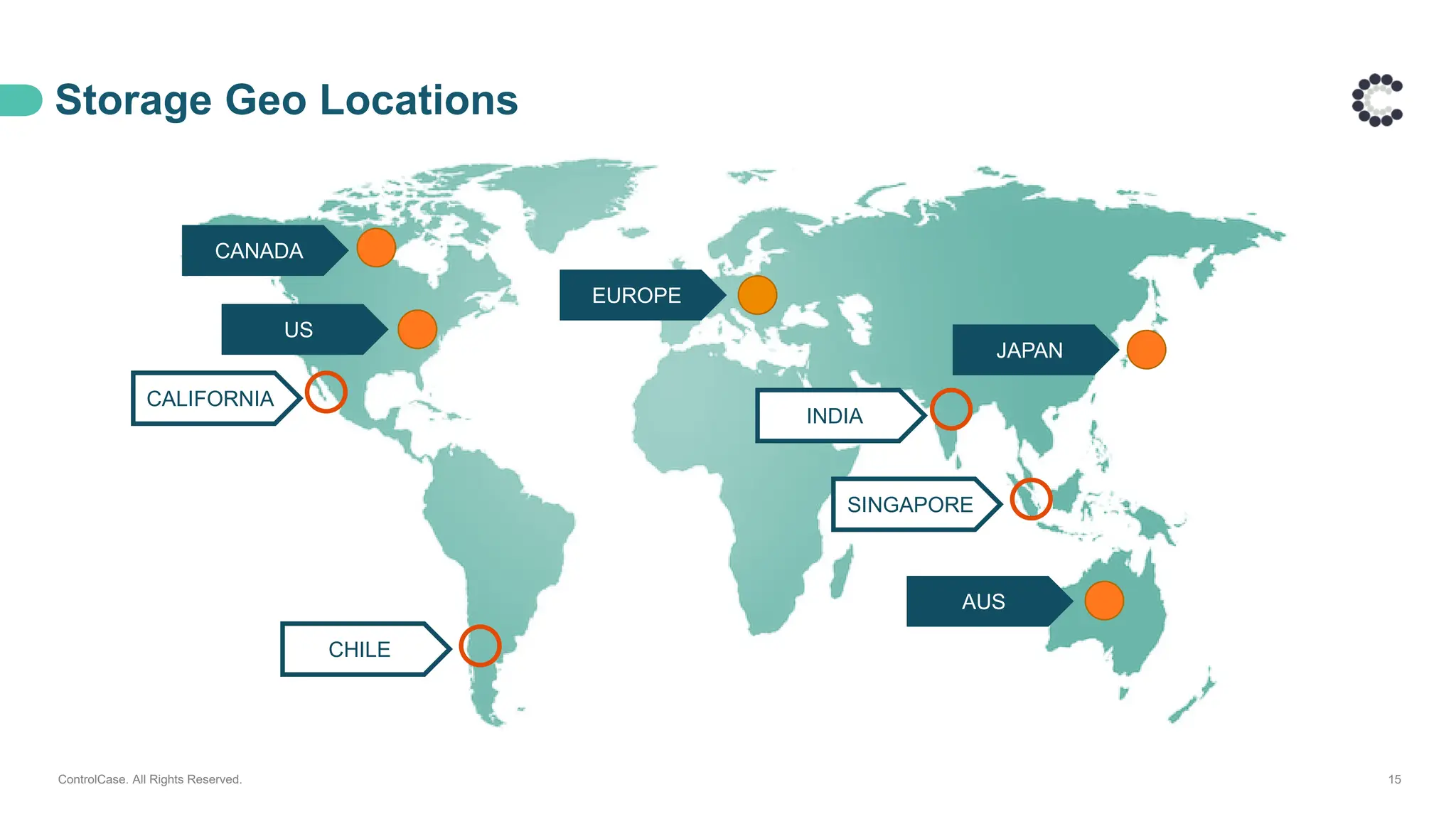
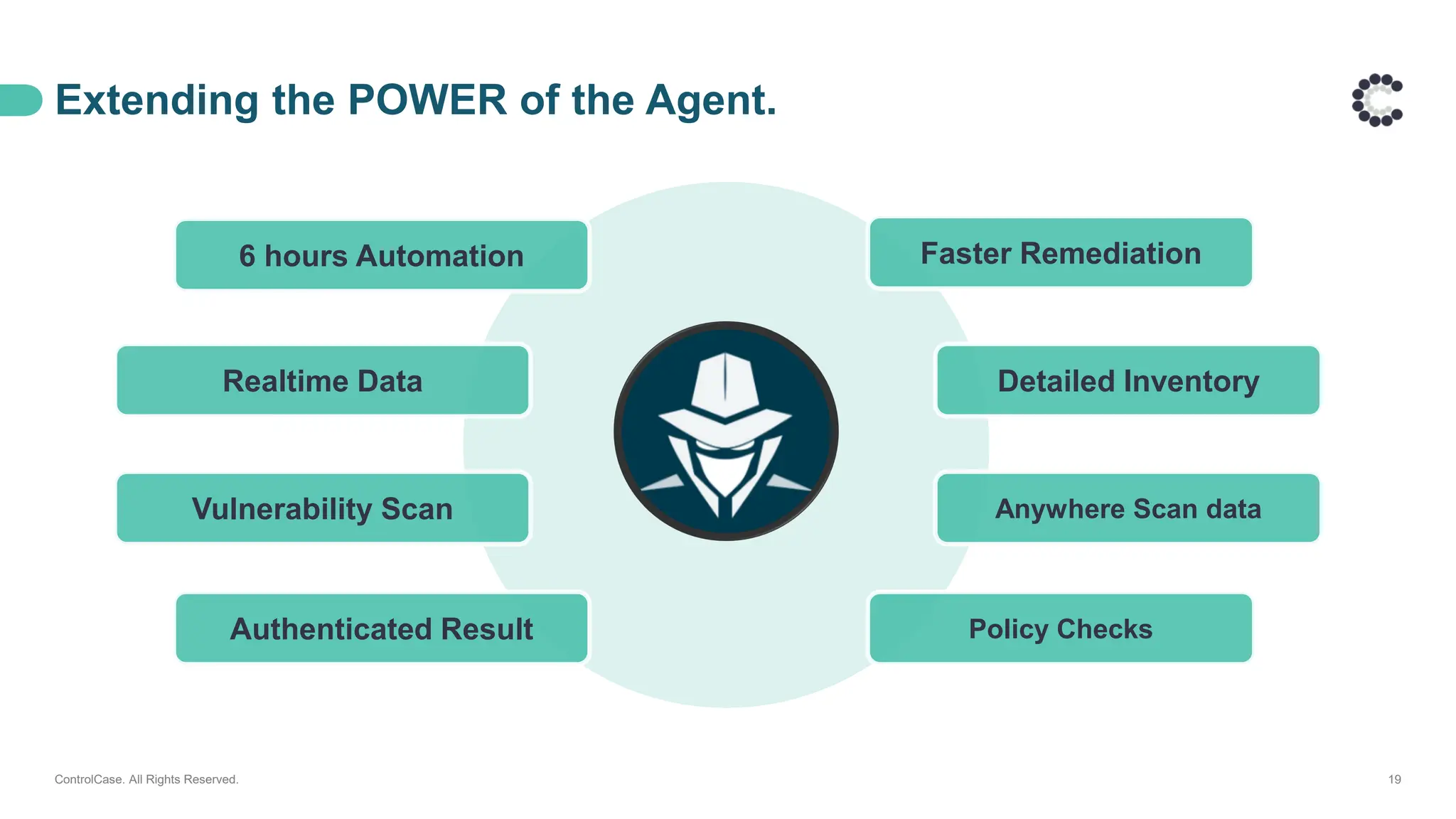
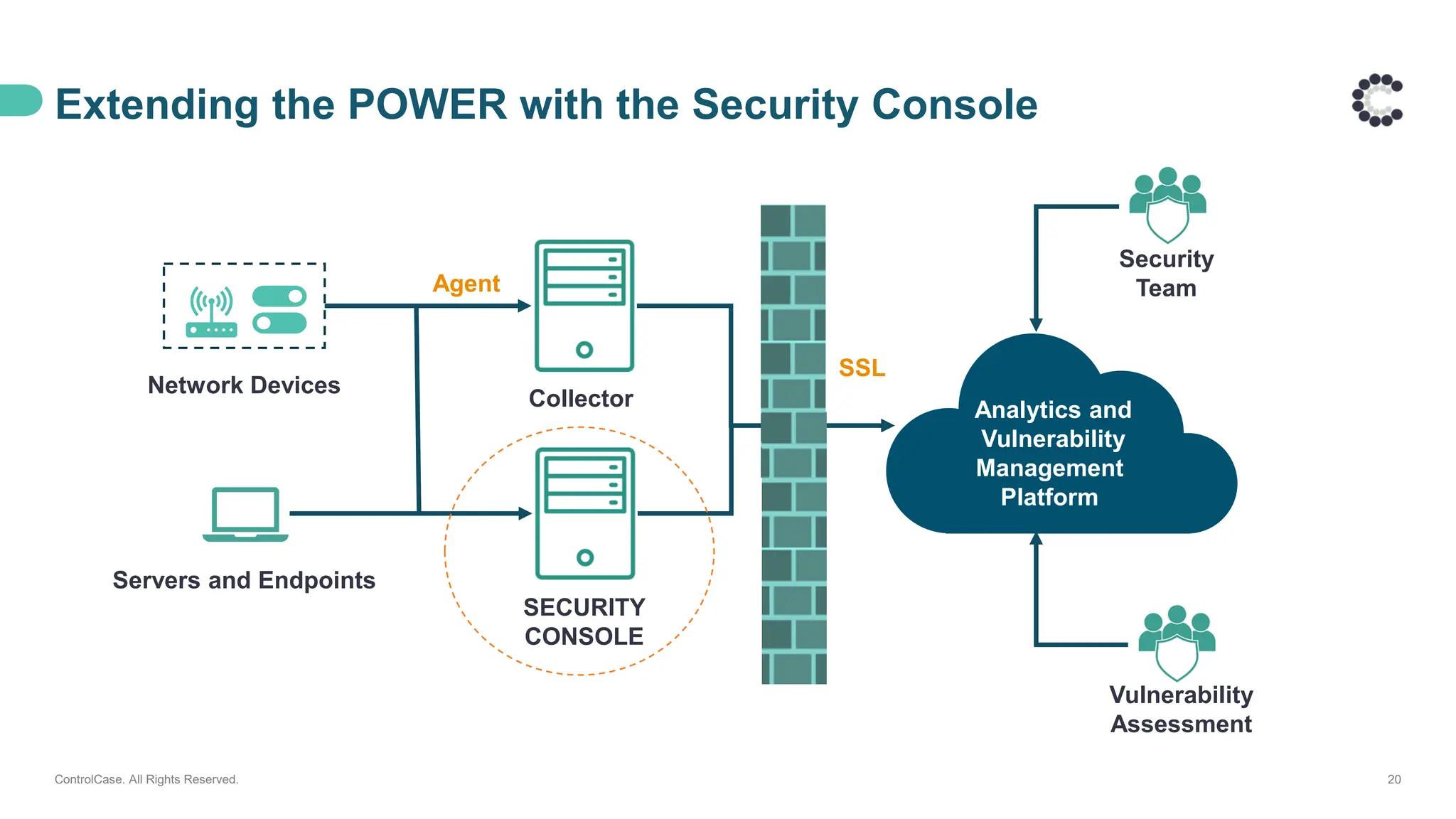
• The architecture behind our proactive LAAS solution
• Real-world results that boost productivity and performance
🎙 Hosted by our cybersecurity experts Chad Leedy and Elswick Lai.
Secure your spot today and learn how to turn compliance into a competitive advantage.
👉 [Insert Registration Link]
#Cybersecurity #Compliance #Logging #Alerting #ControlCase #CaaS #ITSecurity #Webinar