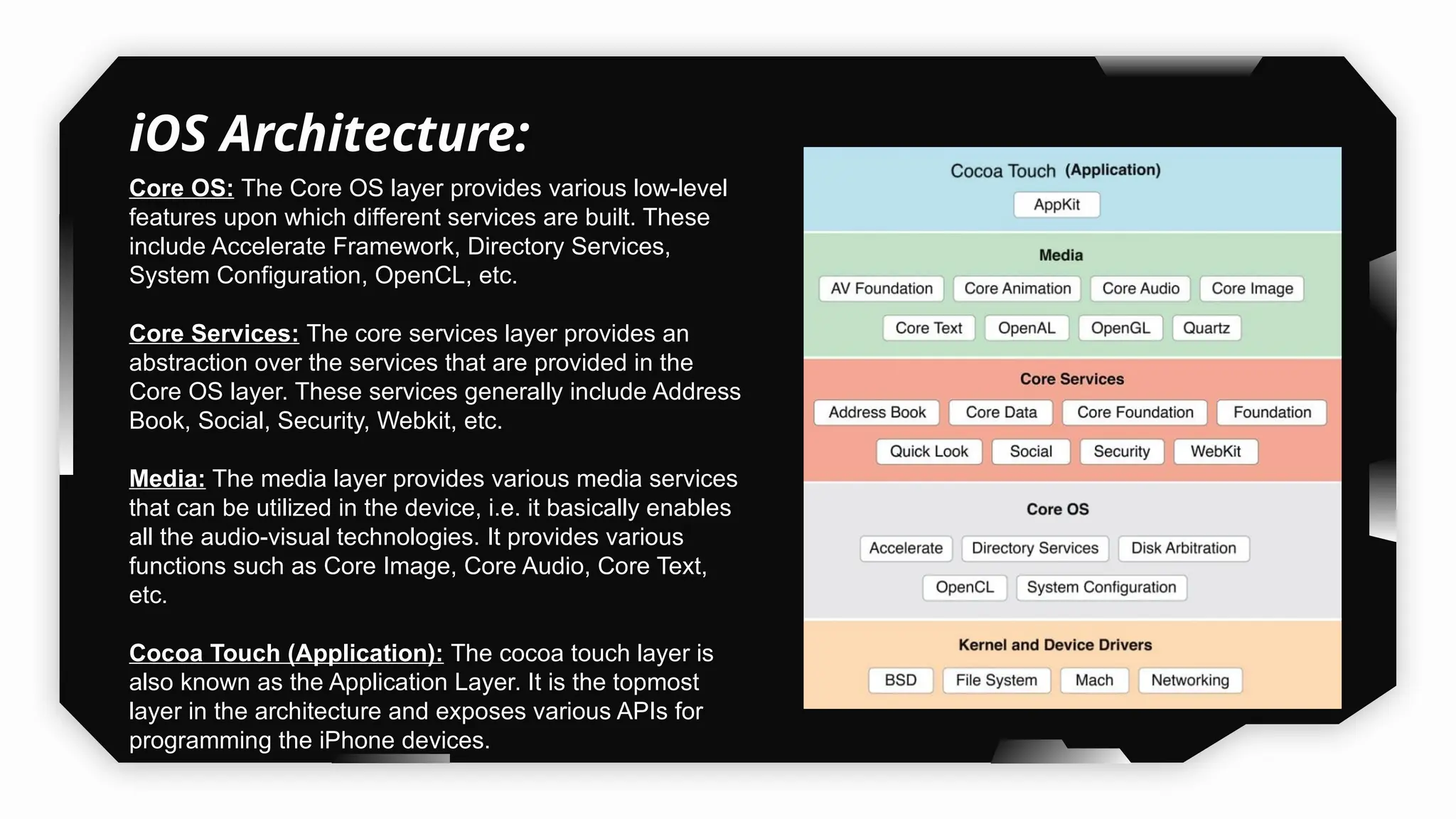
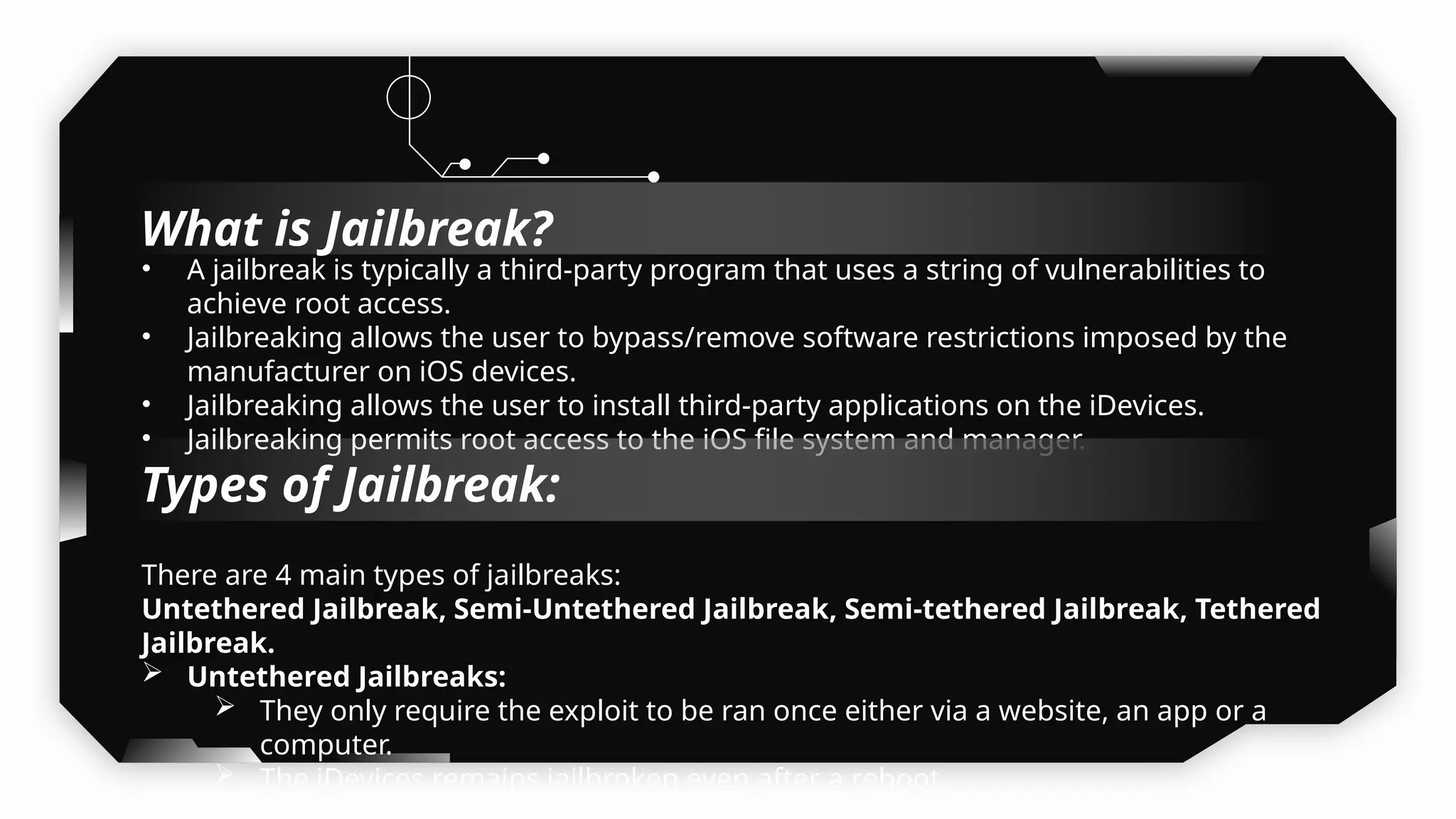
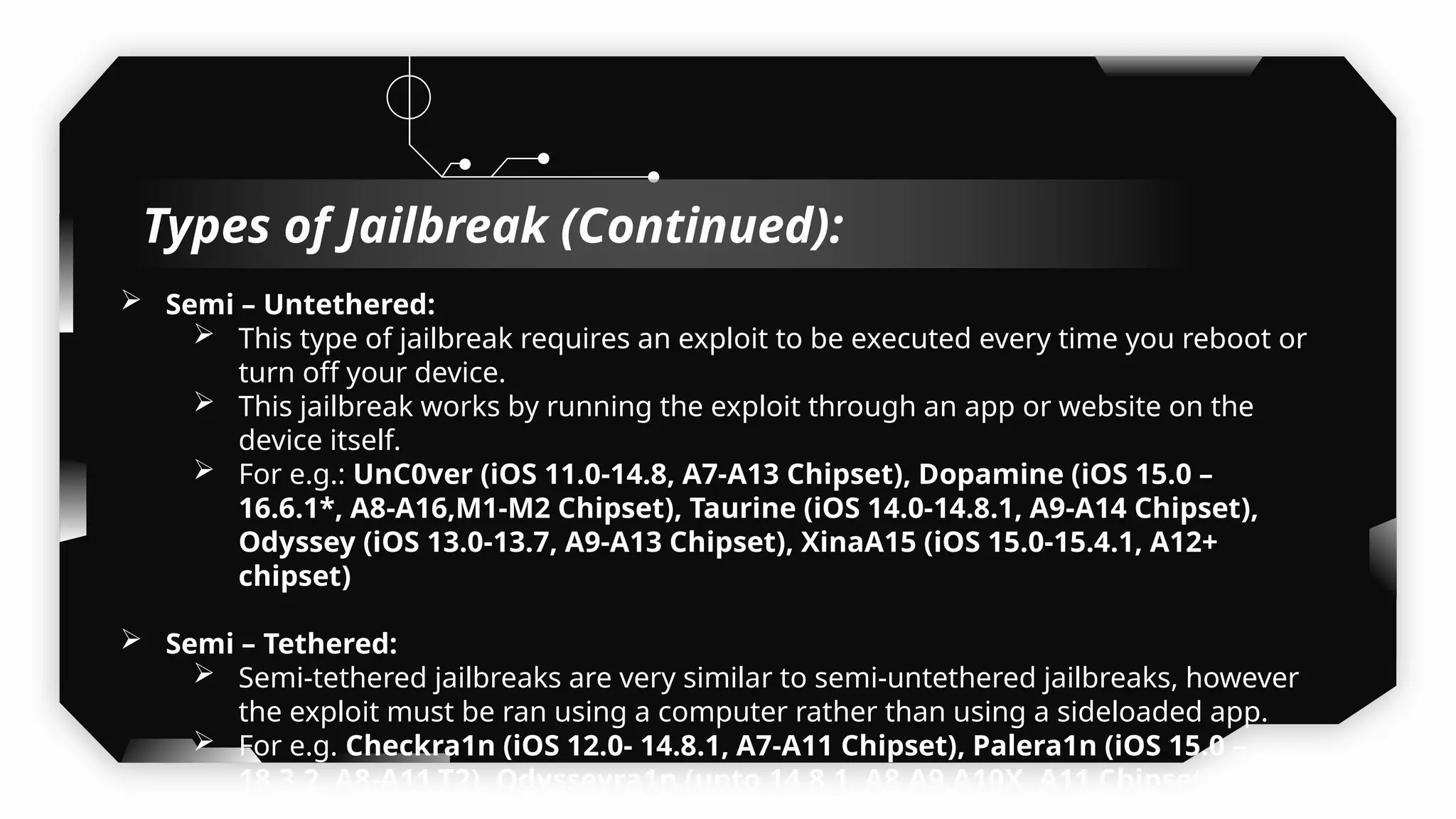
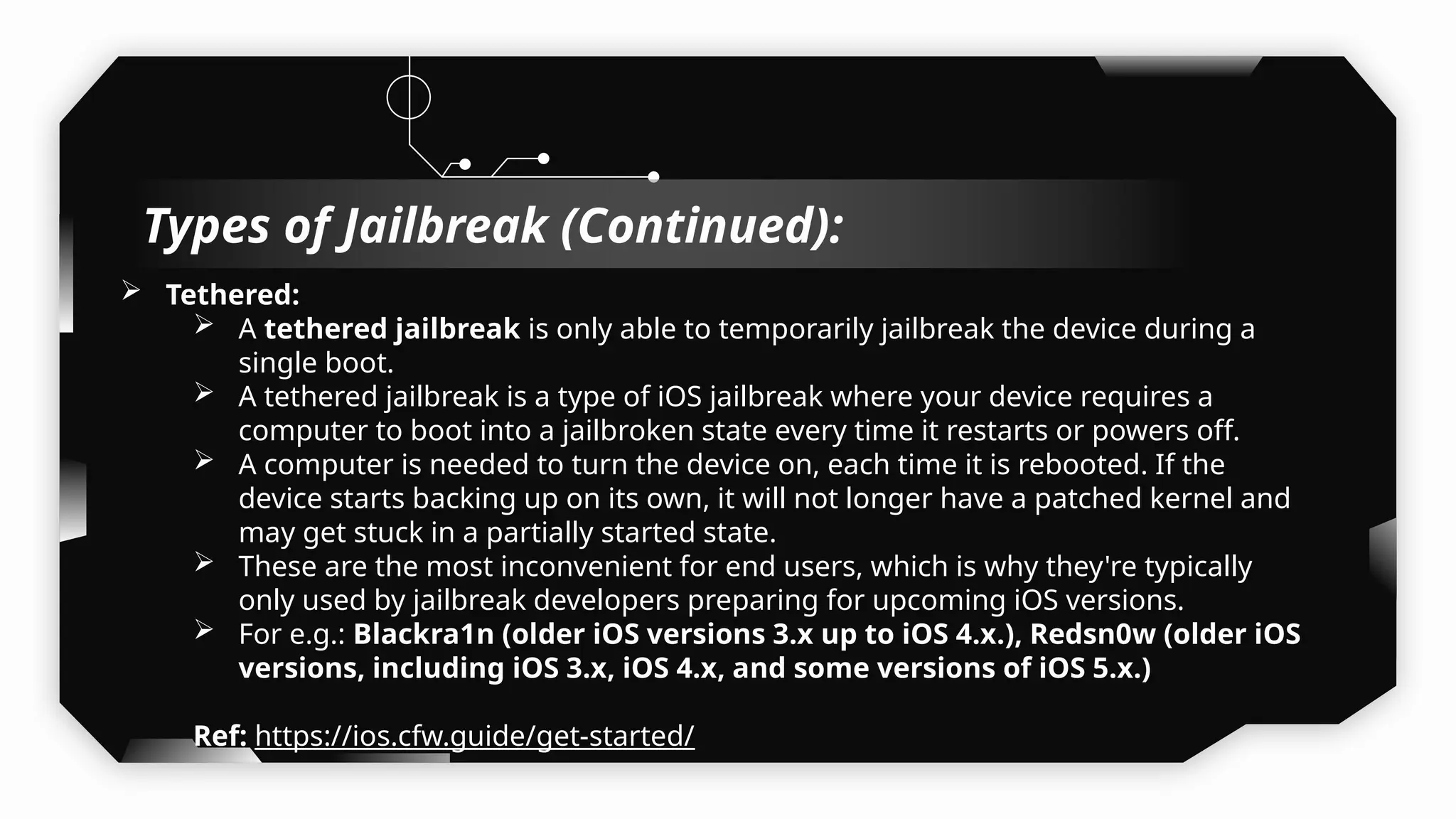
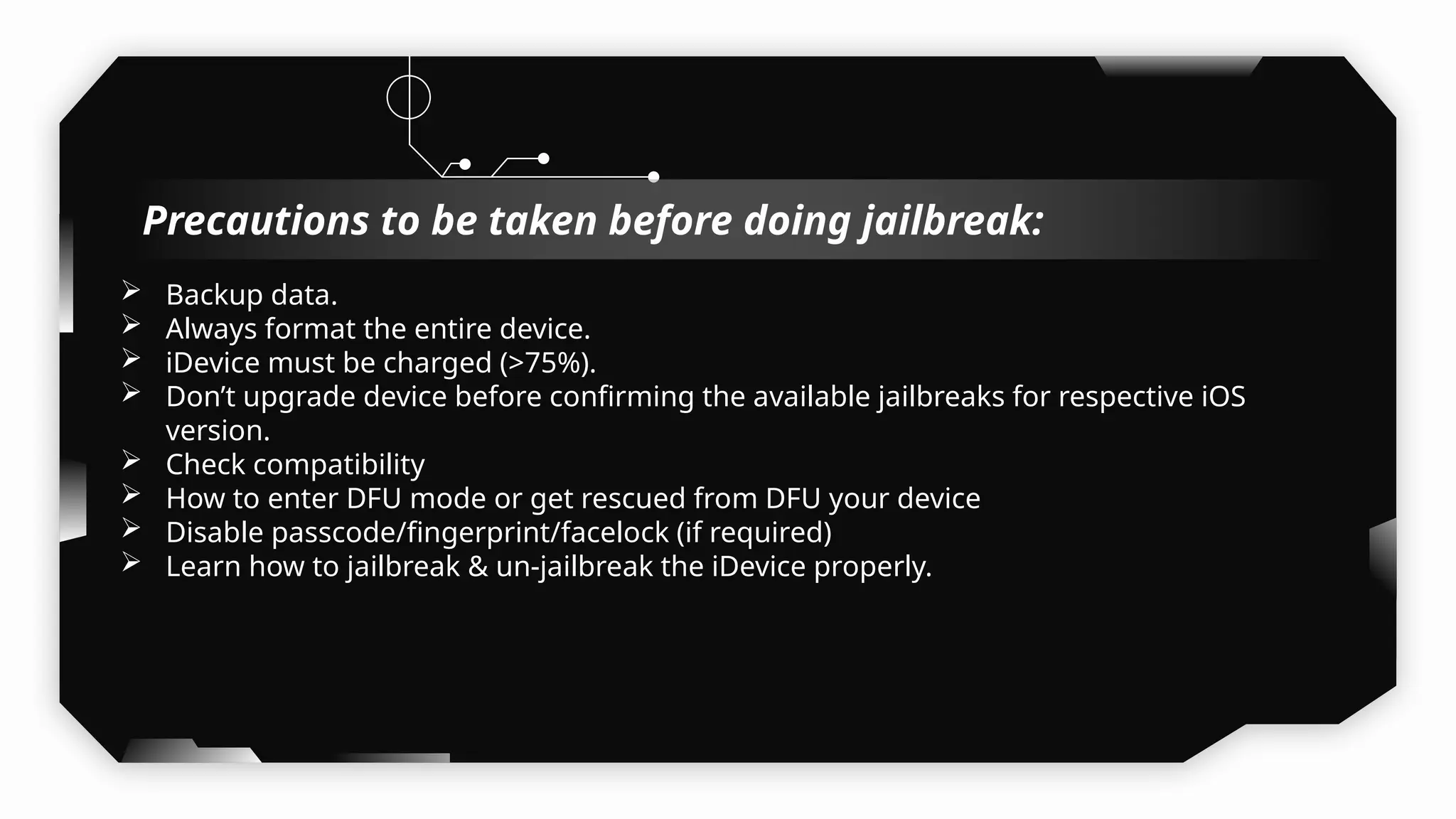
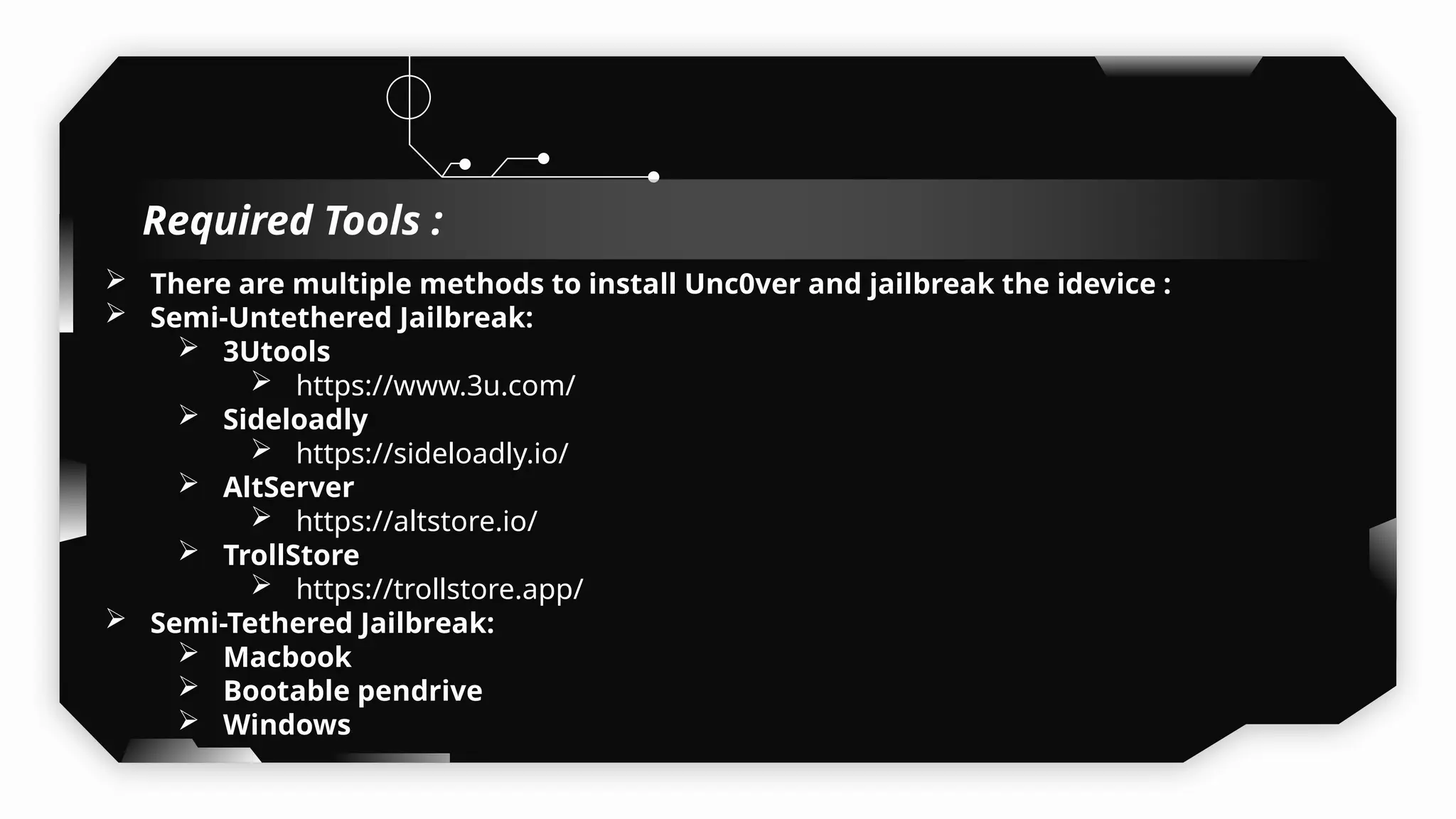
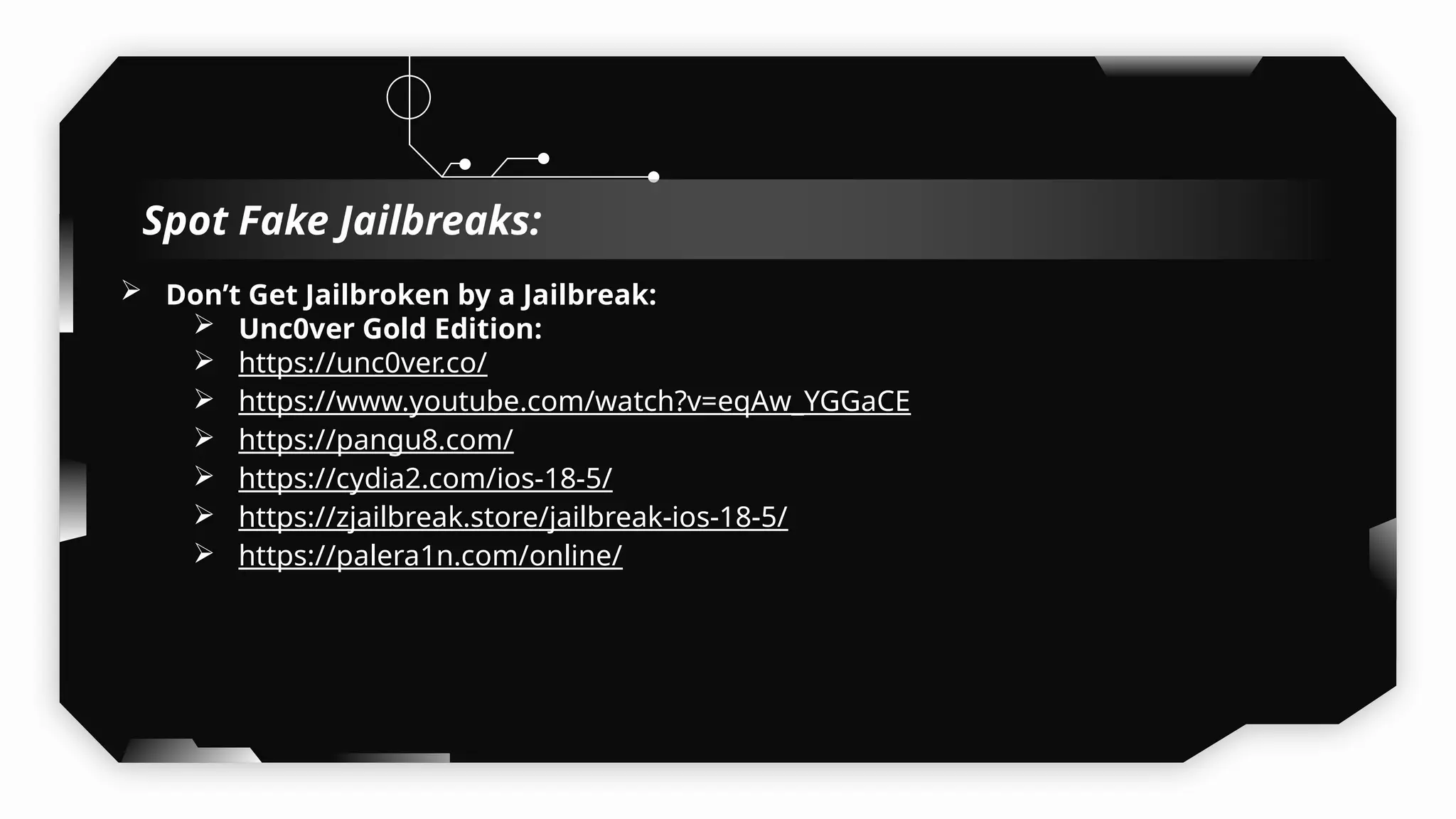
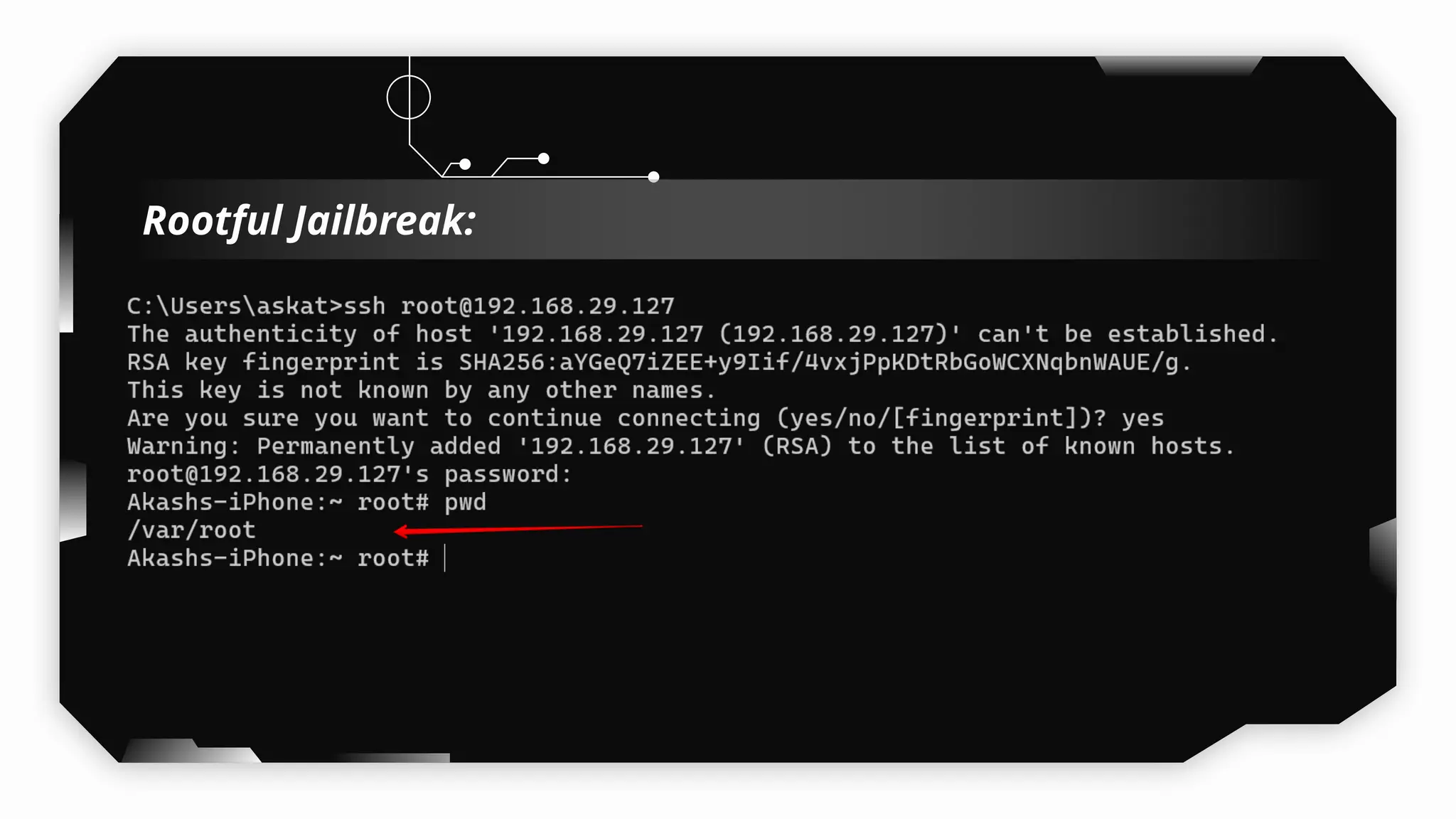
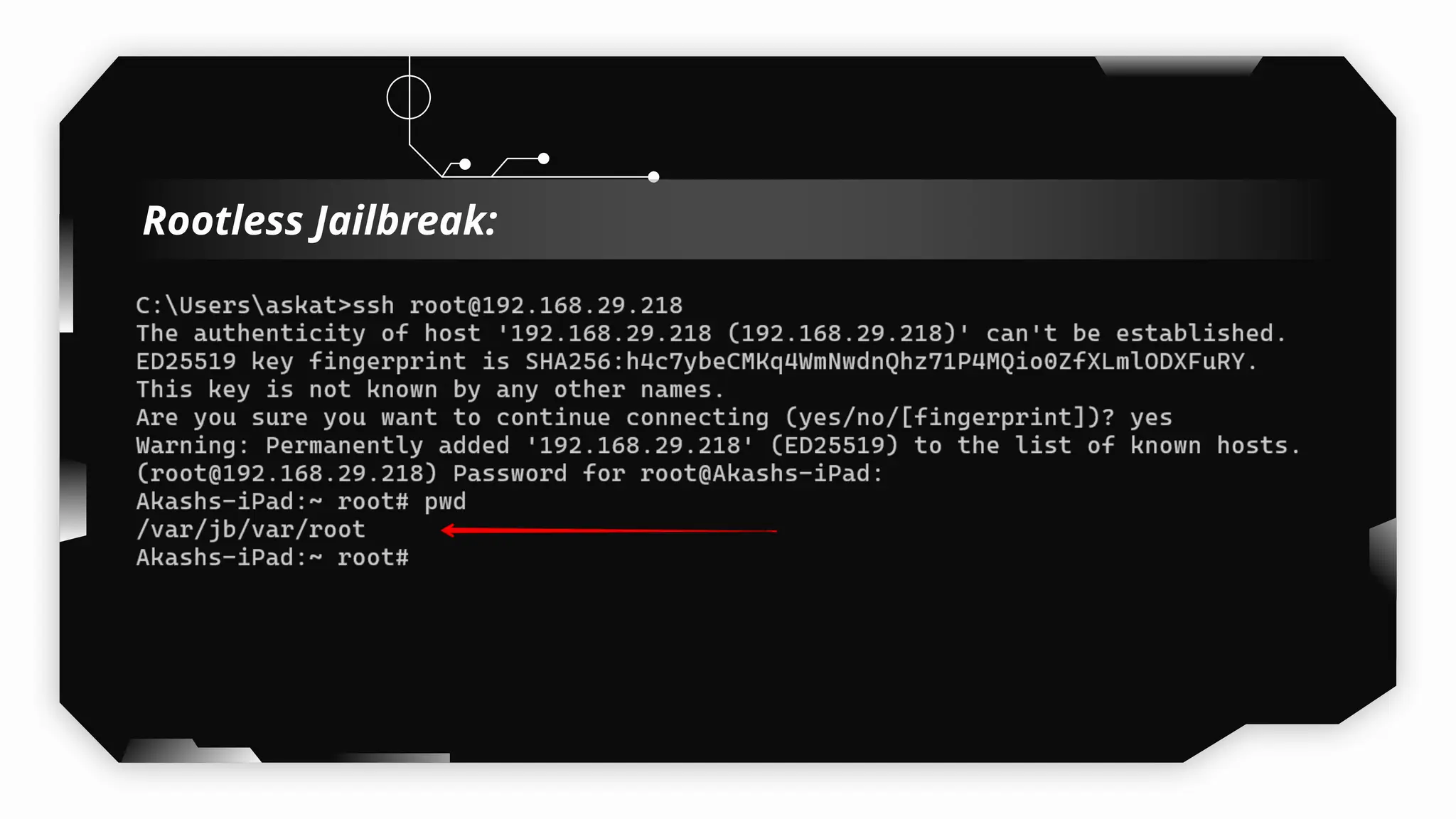
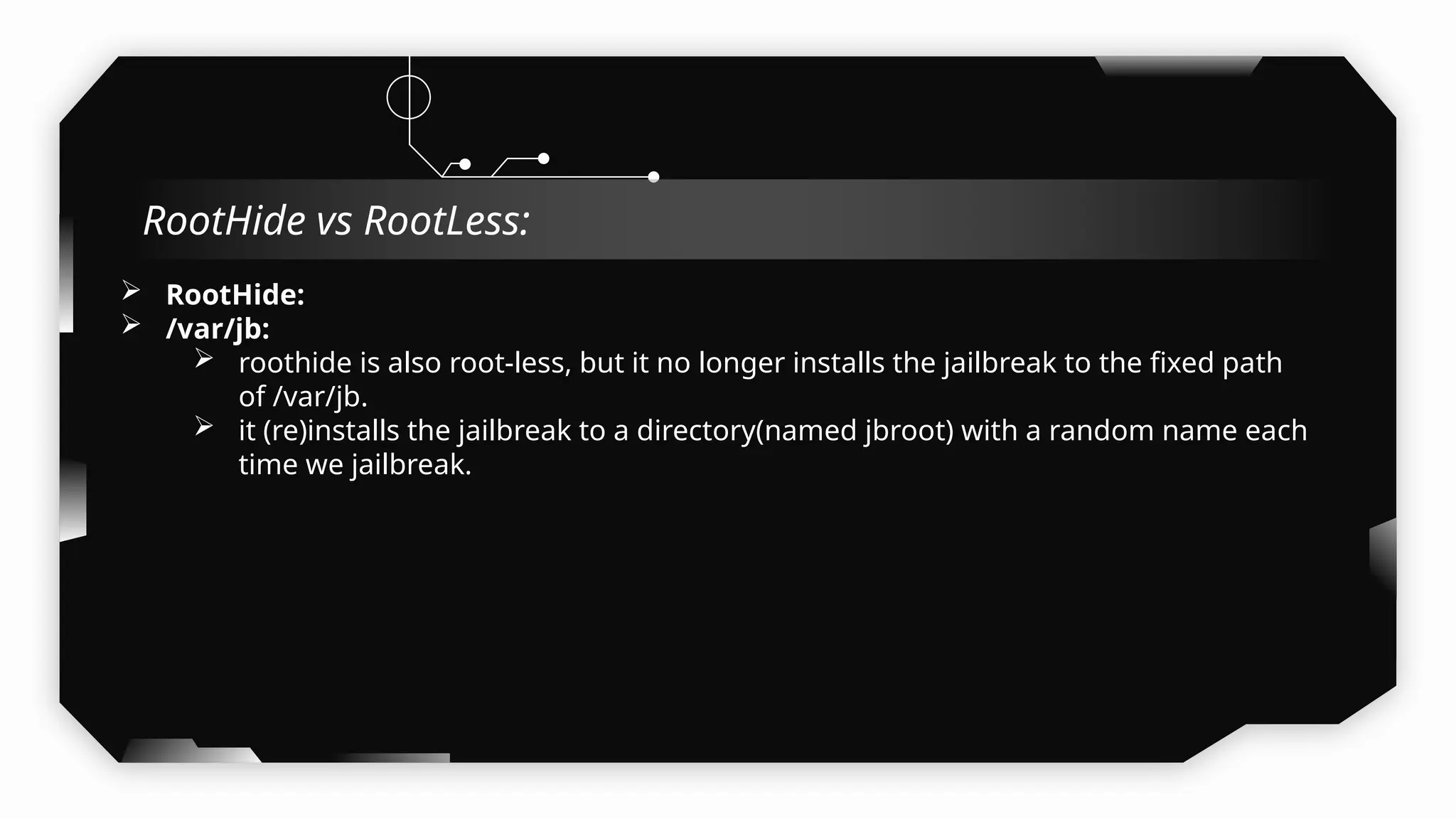
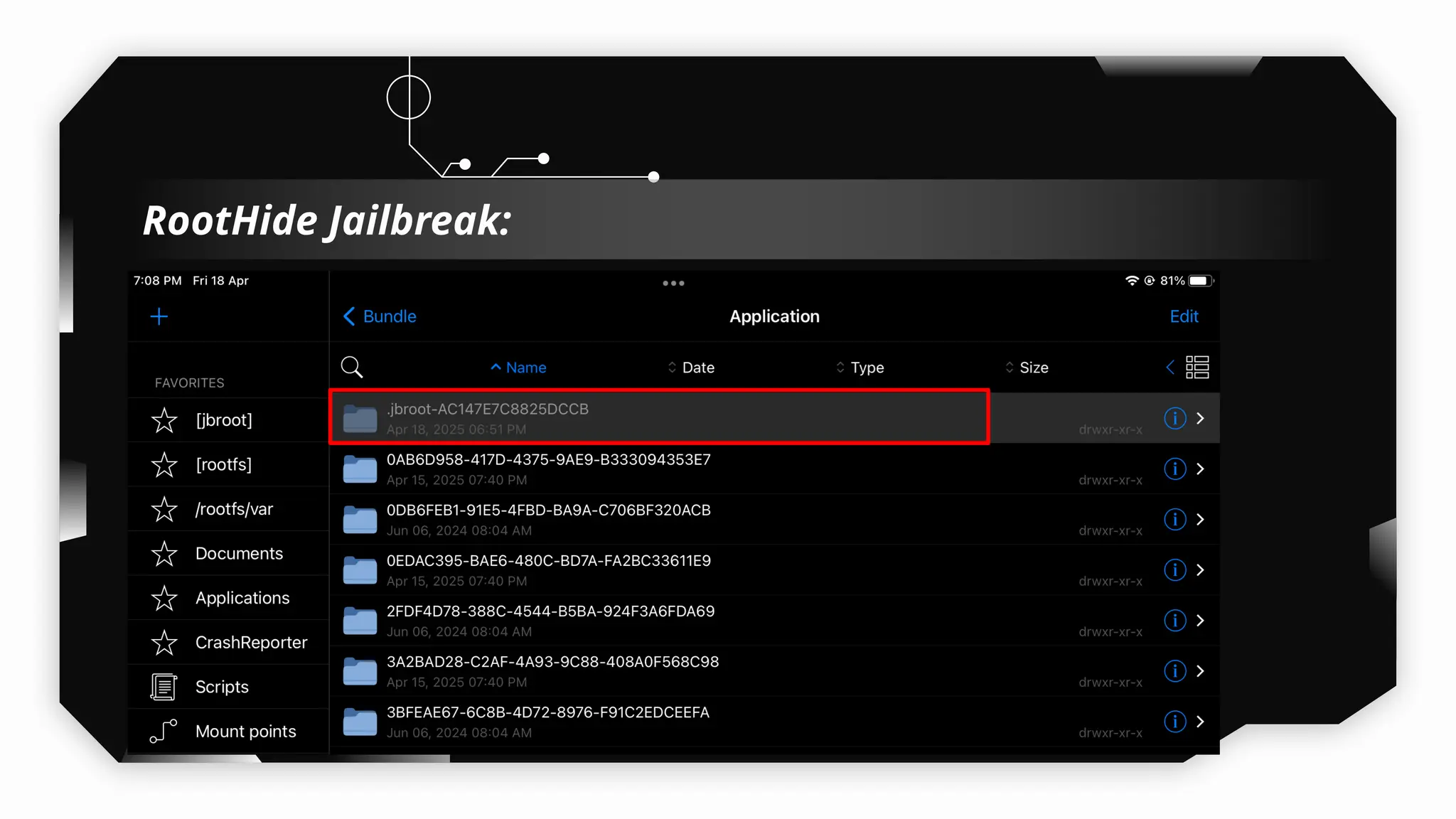
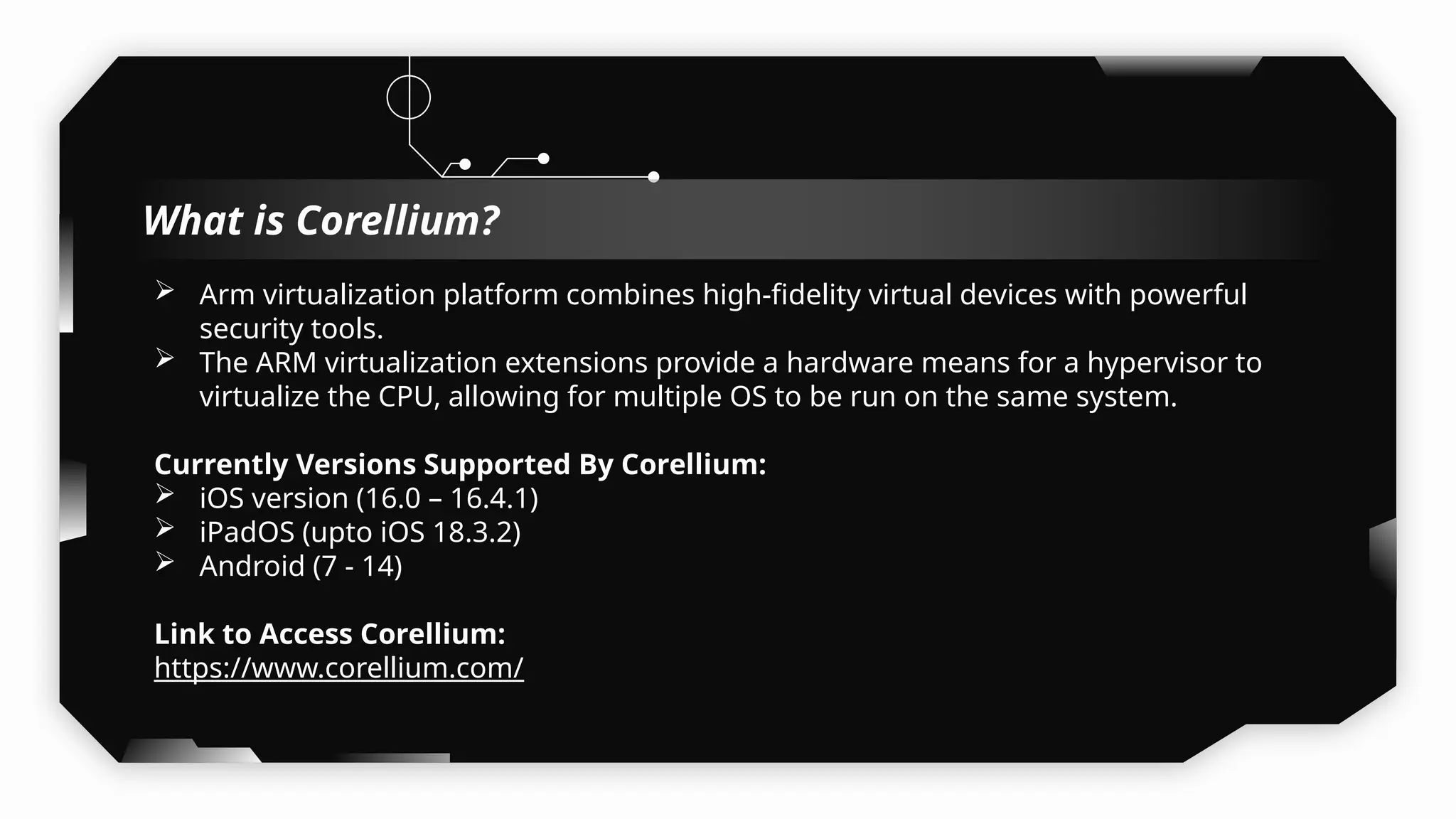
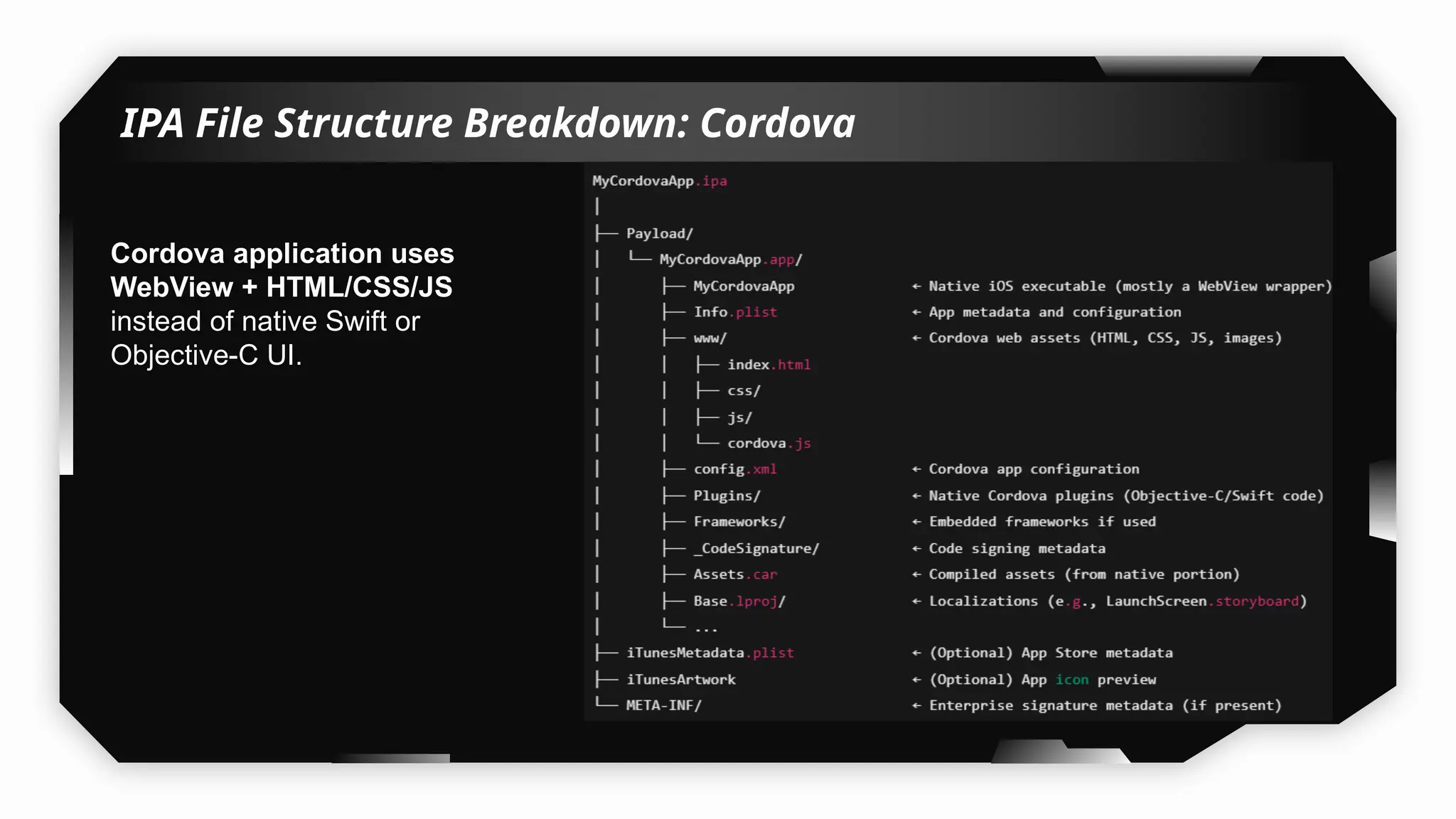
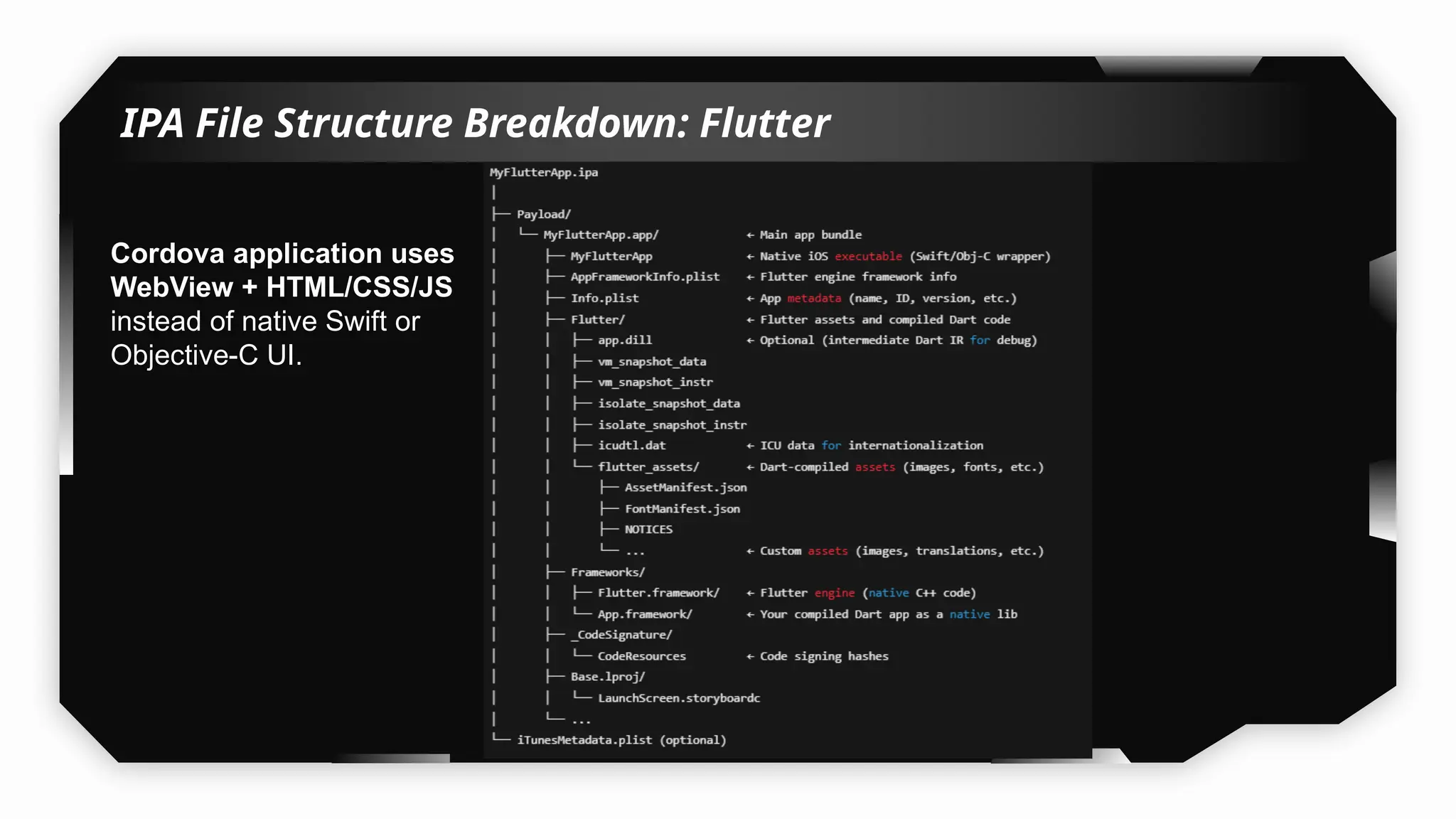
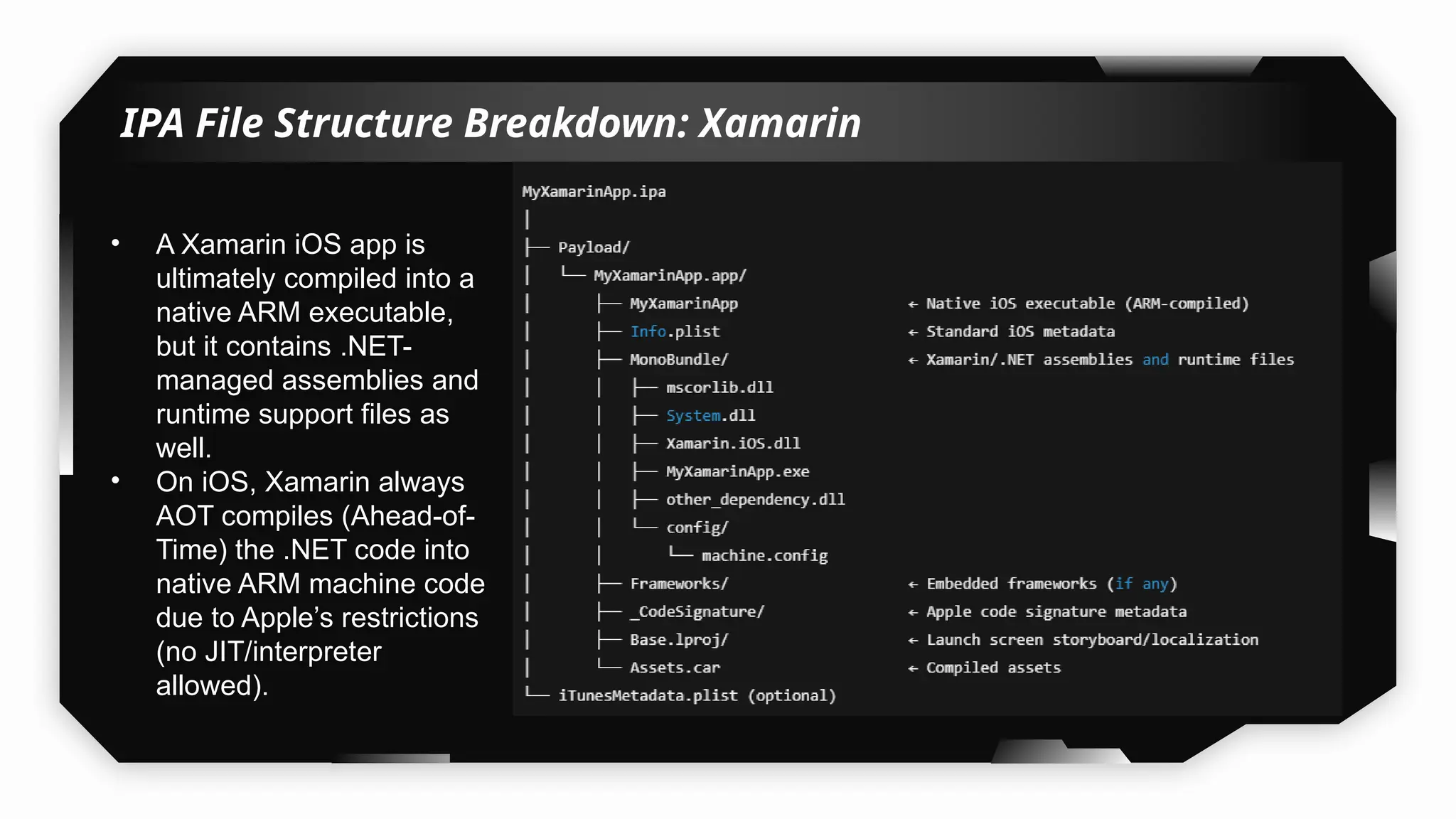
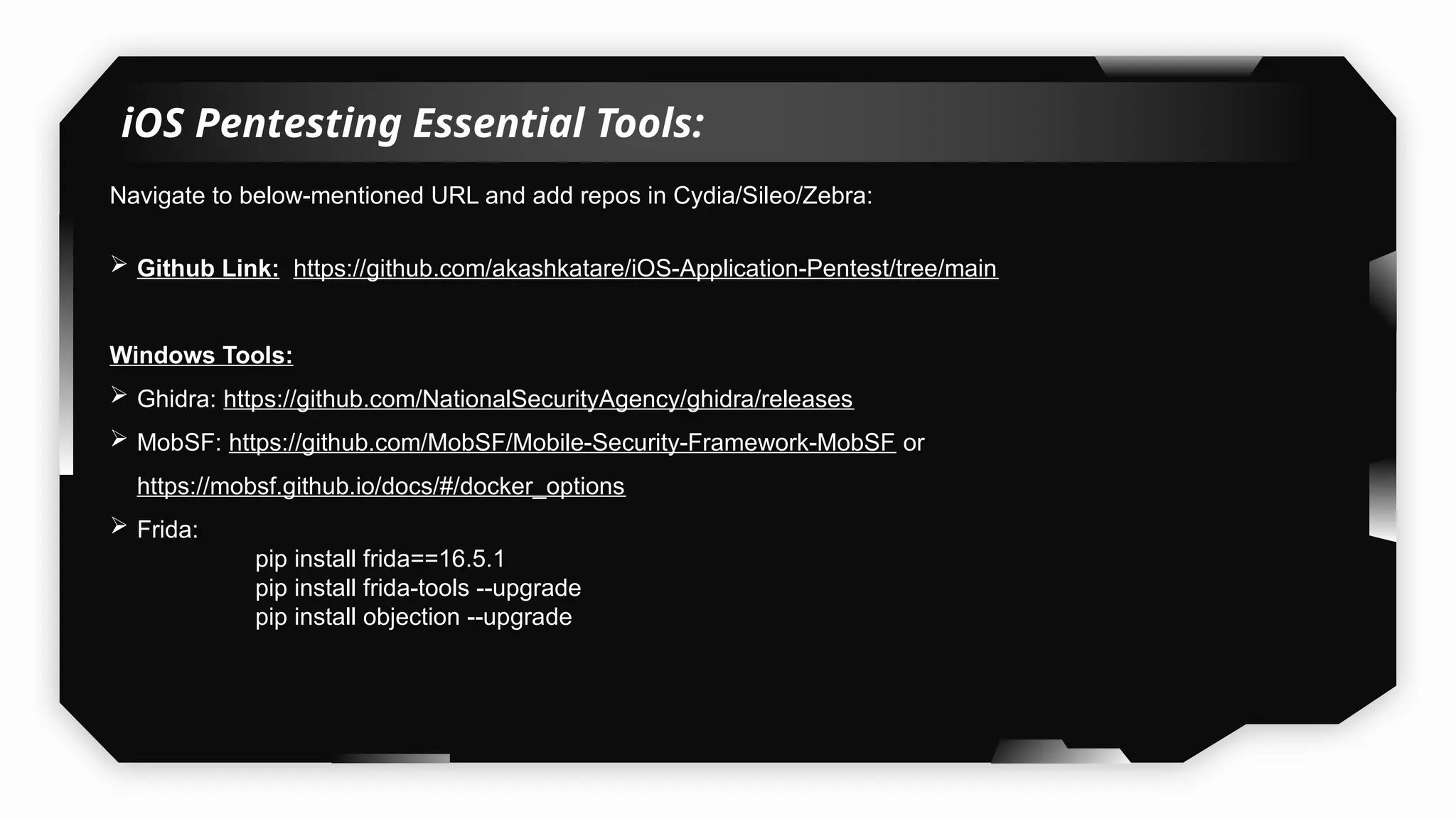
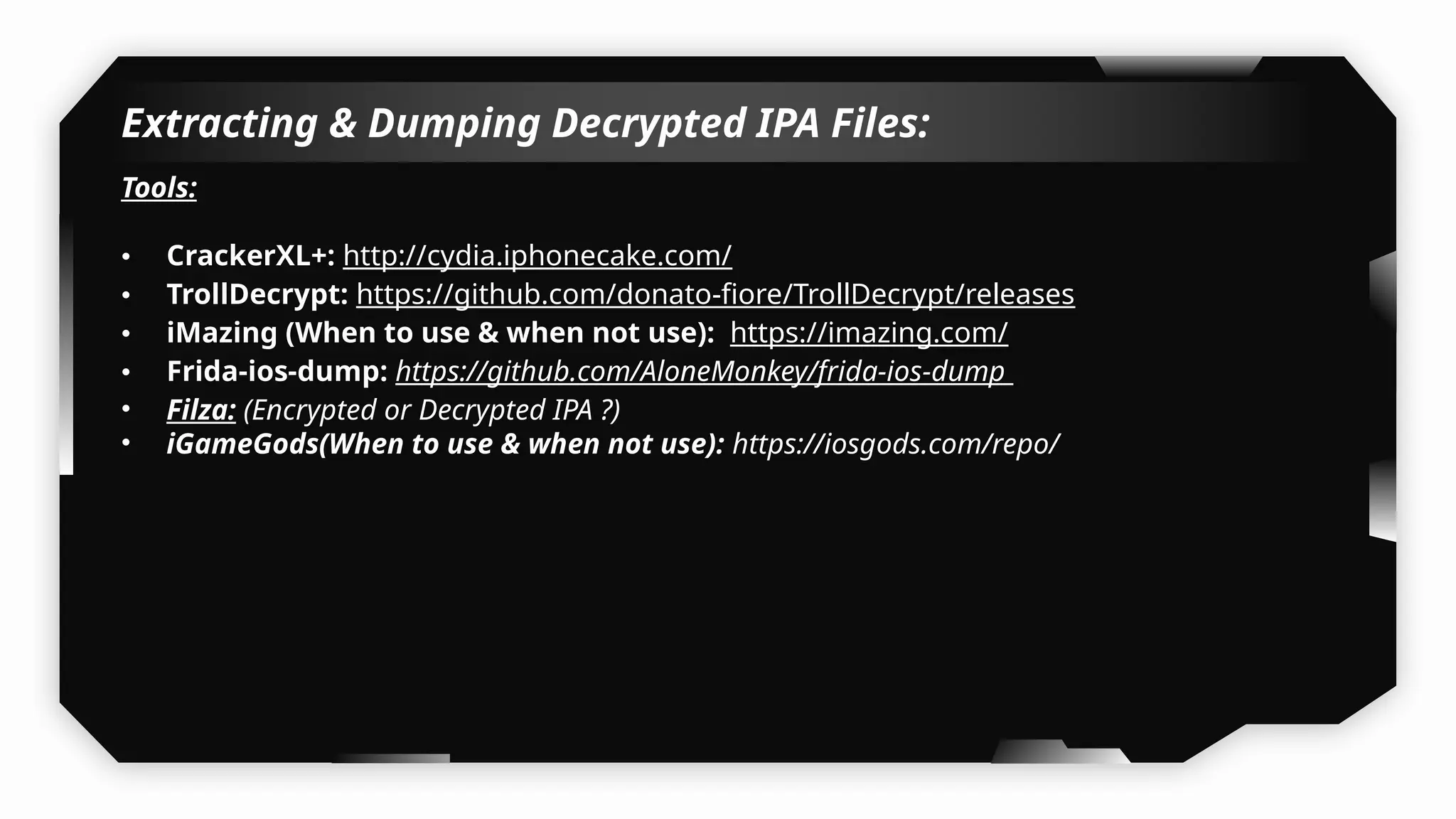
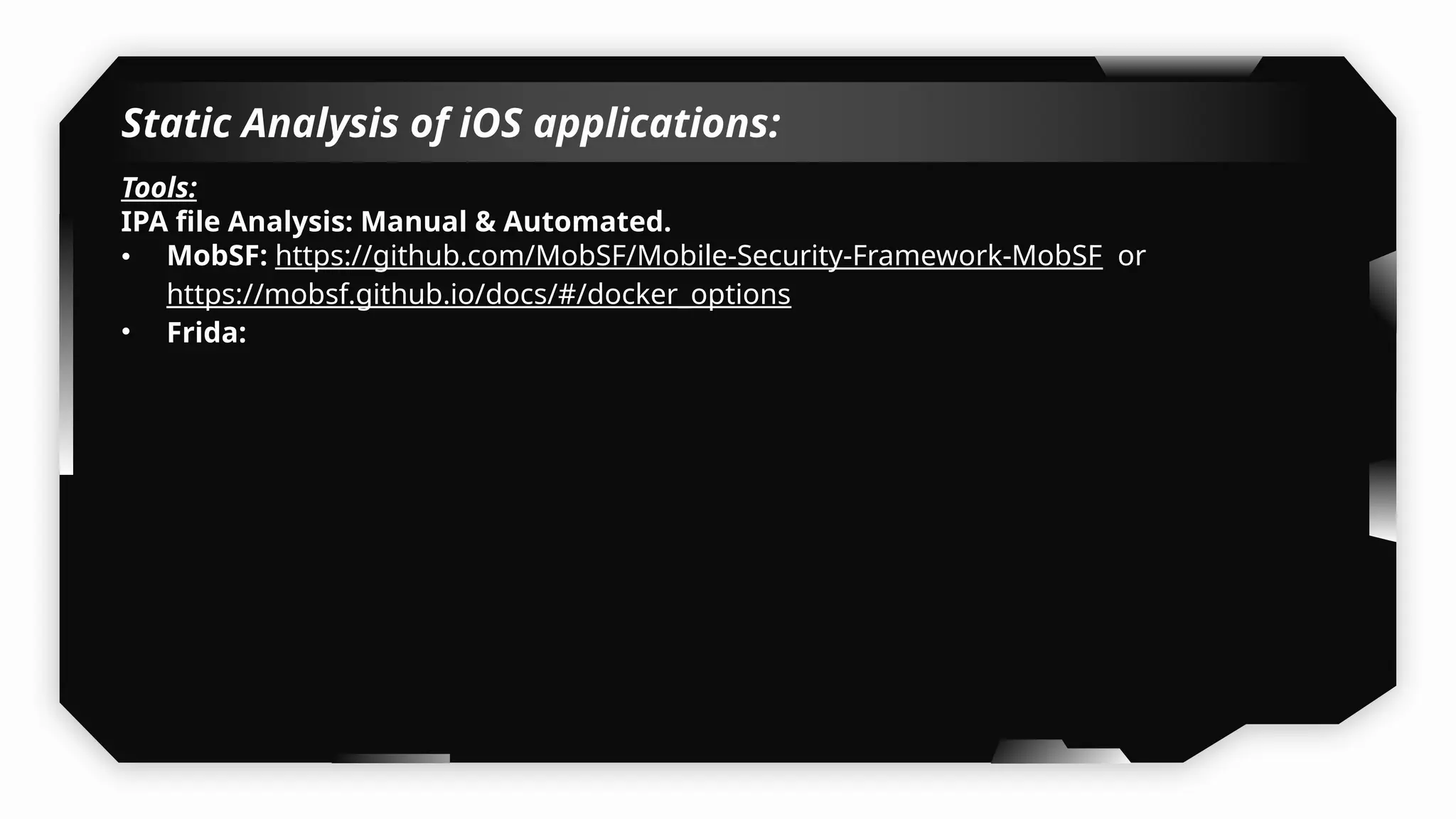
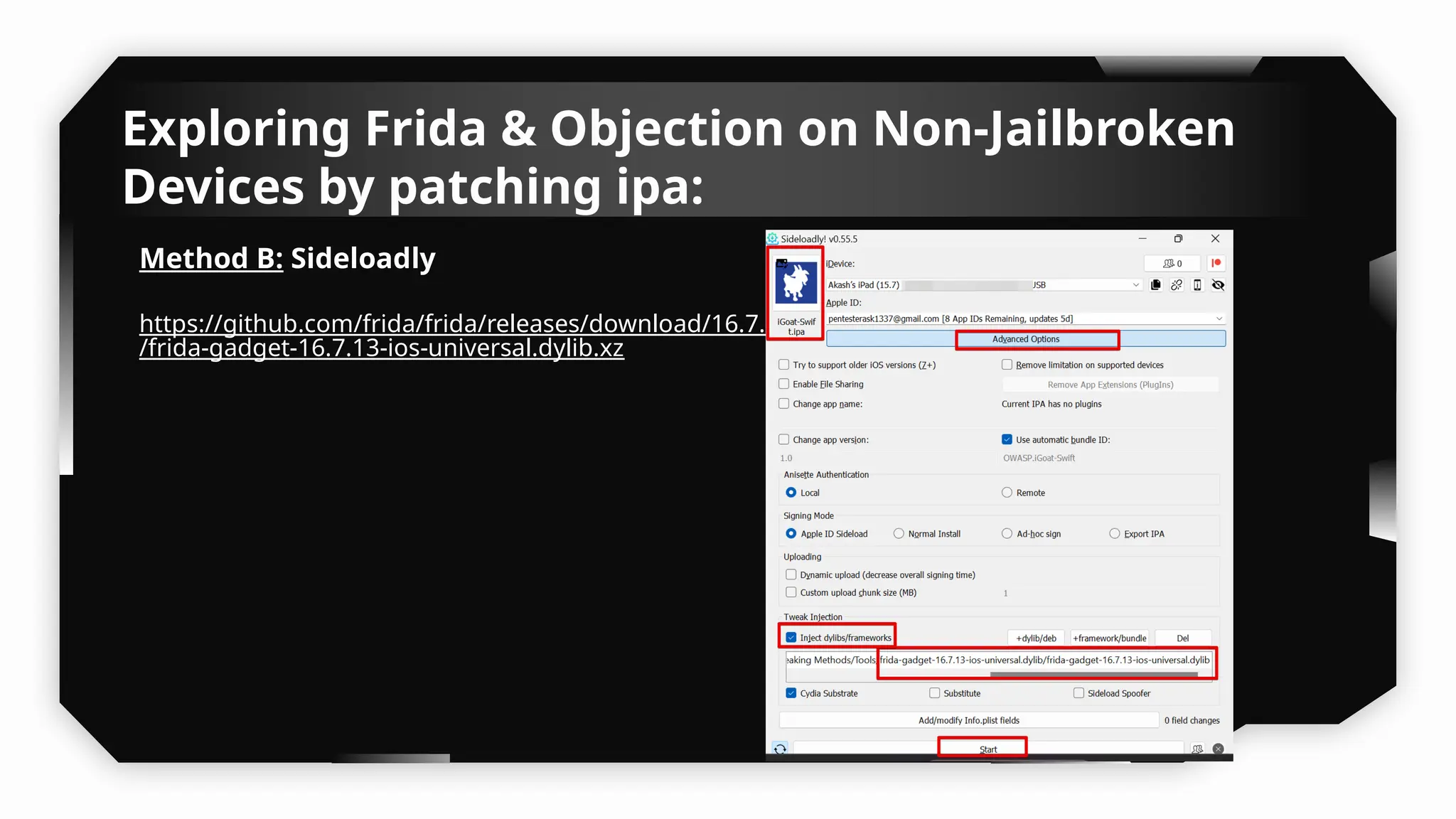
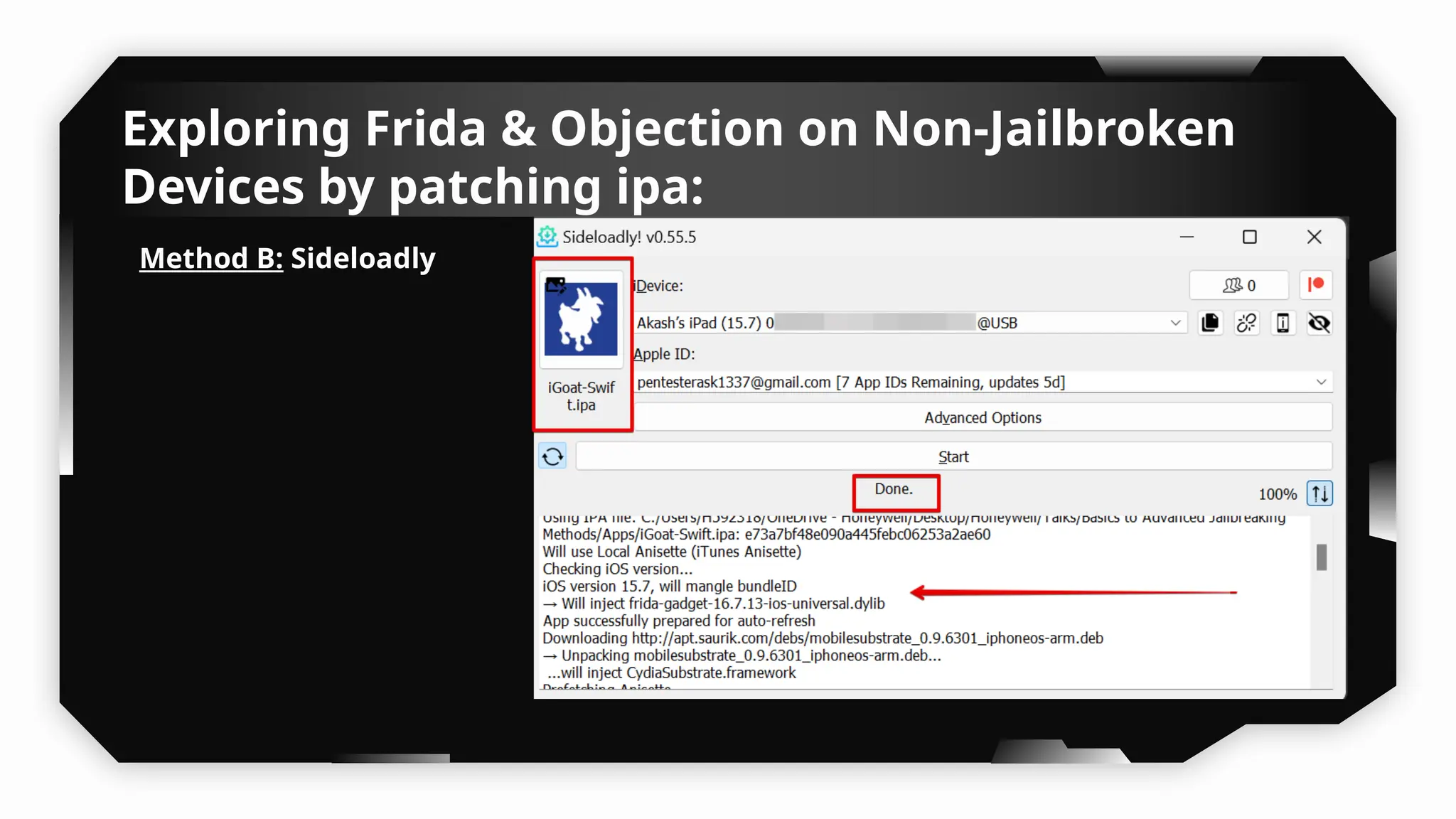
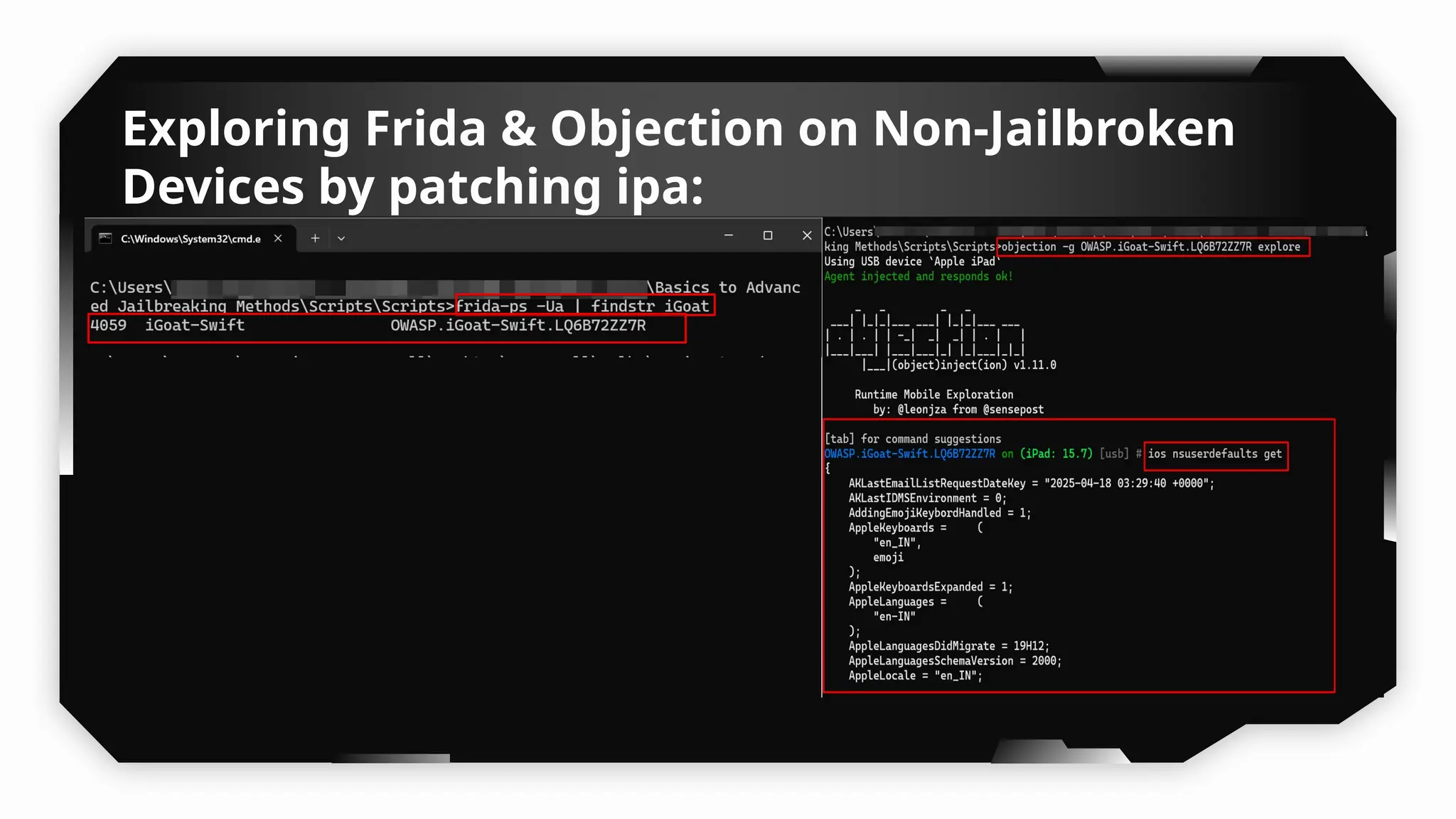
This presentation provides a comprehensive dive into iOS application security, covering everything from architecture to advanced pentesting techniques. The topics include an overview of iOS architecture, an understanding of jailbreak types (rootful vs. rootless), and methods for jailbreaking iDevices. You'll explore tools for testing iOS applications on both jailbroken and non-jailbroken devices, as well as key analysis techniques like static analysis and extracting decrypted IPA files.
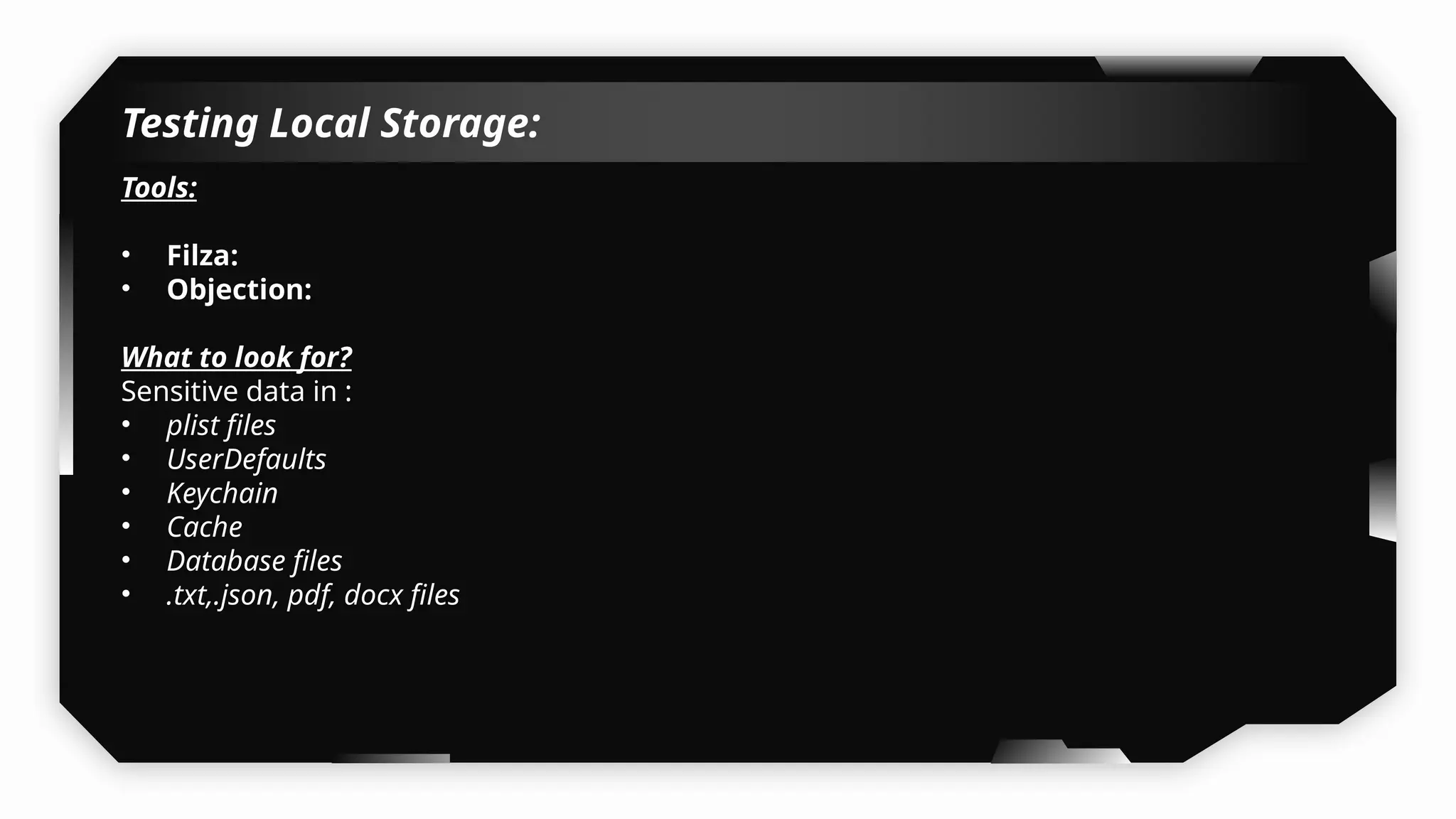
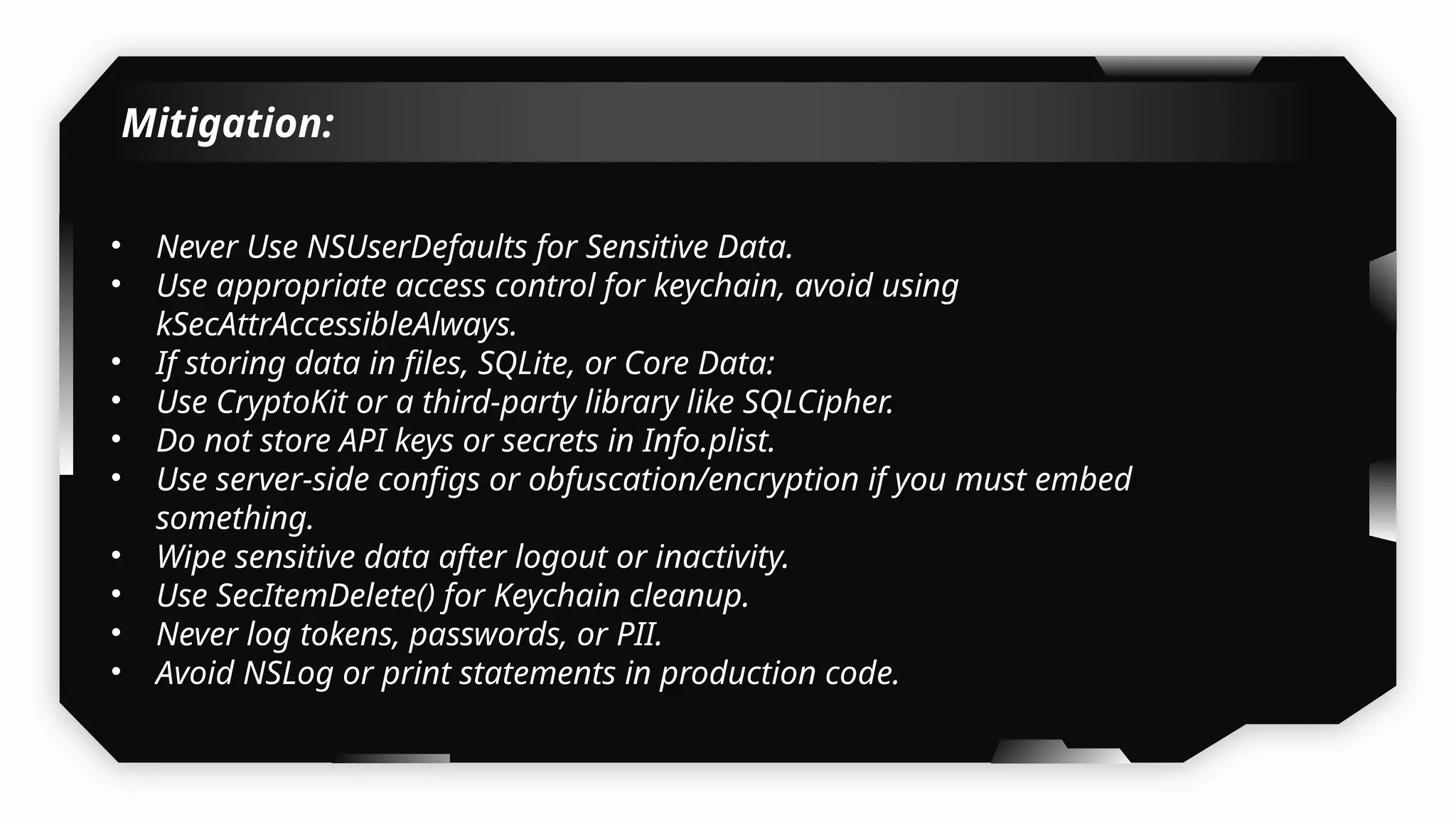
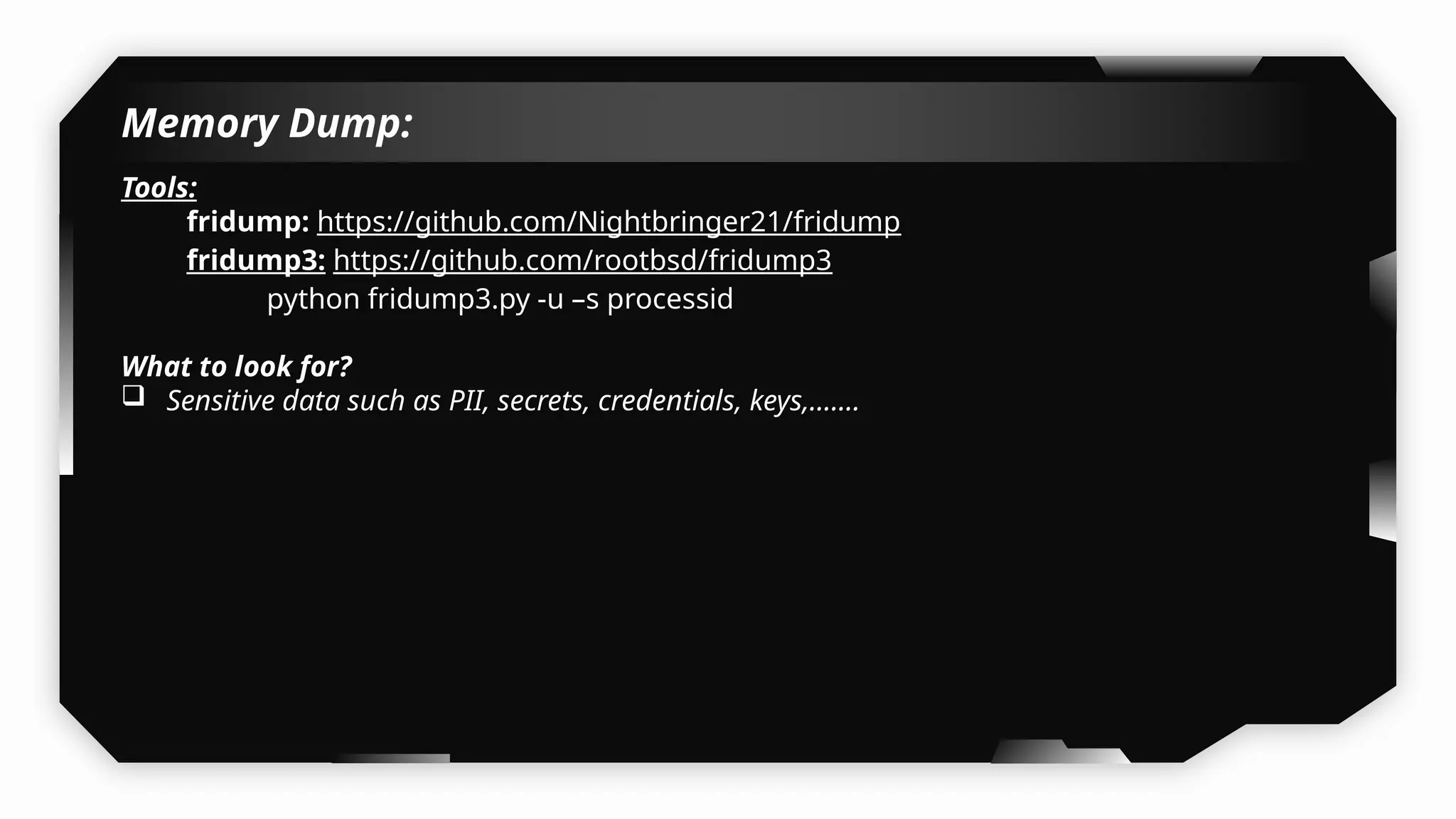
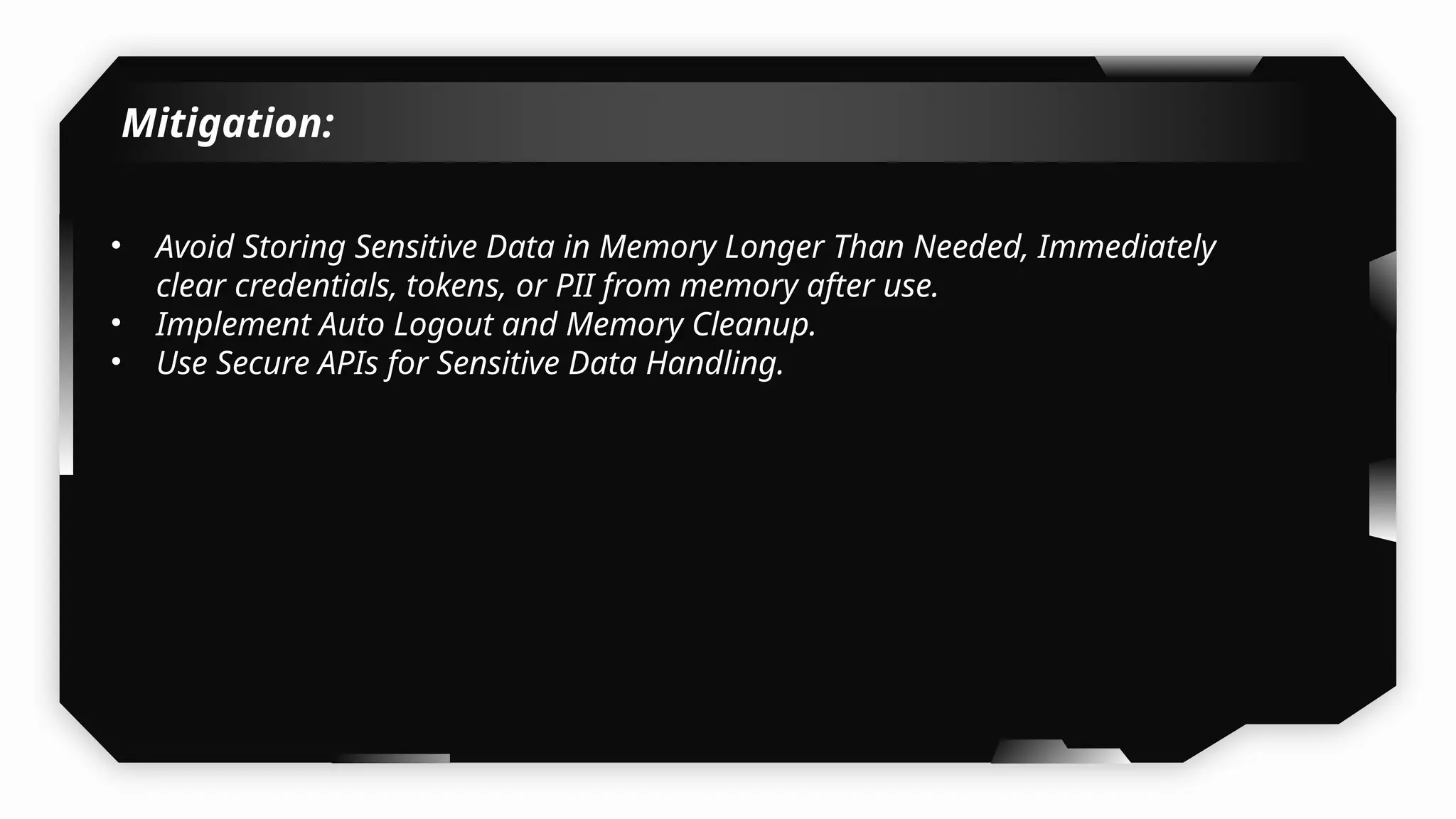
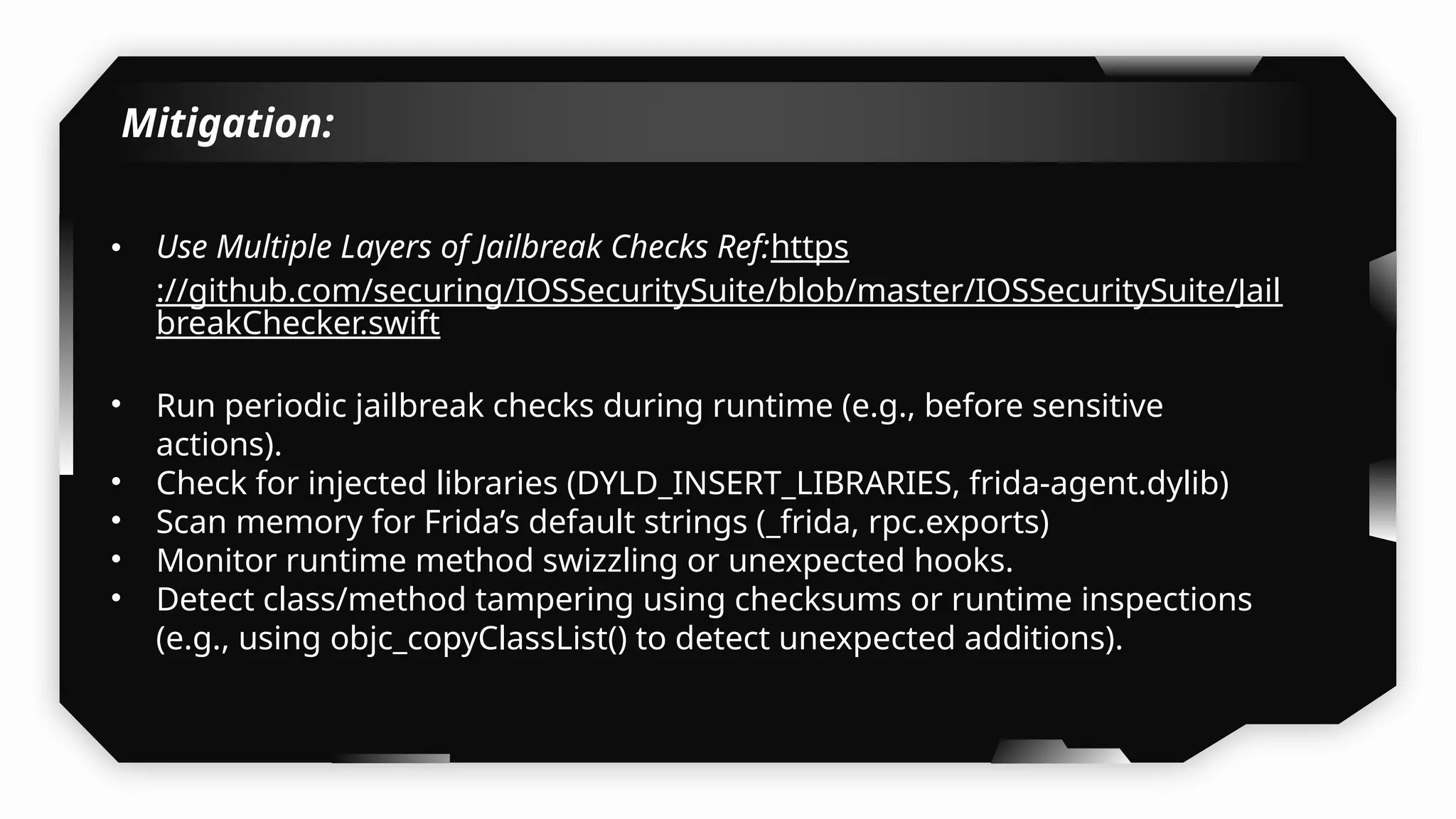
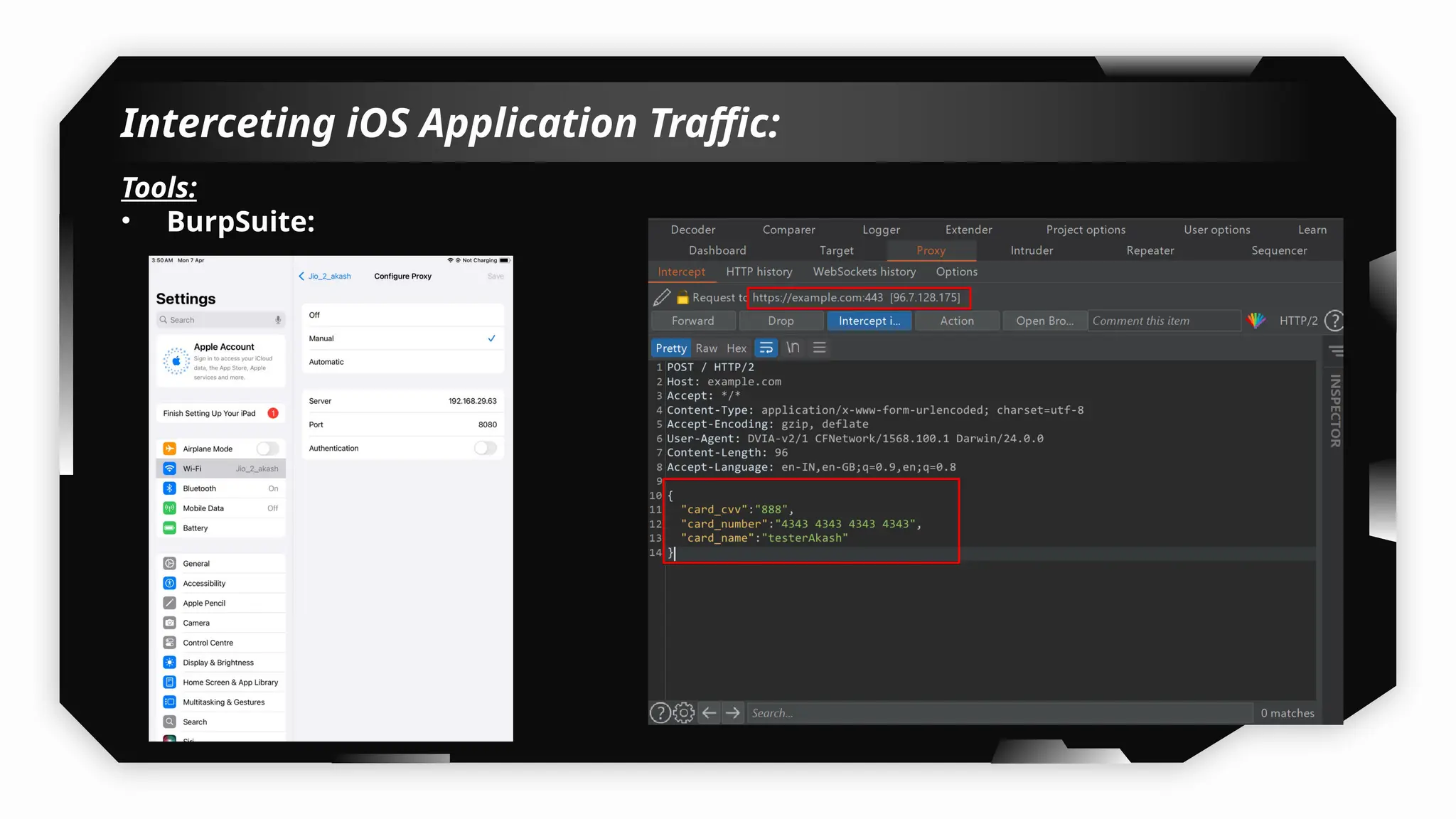
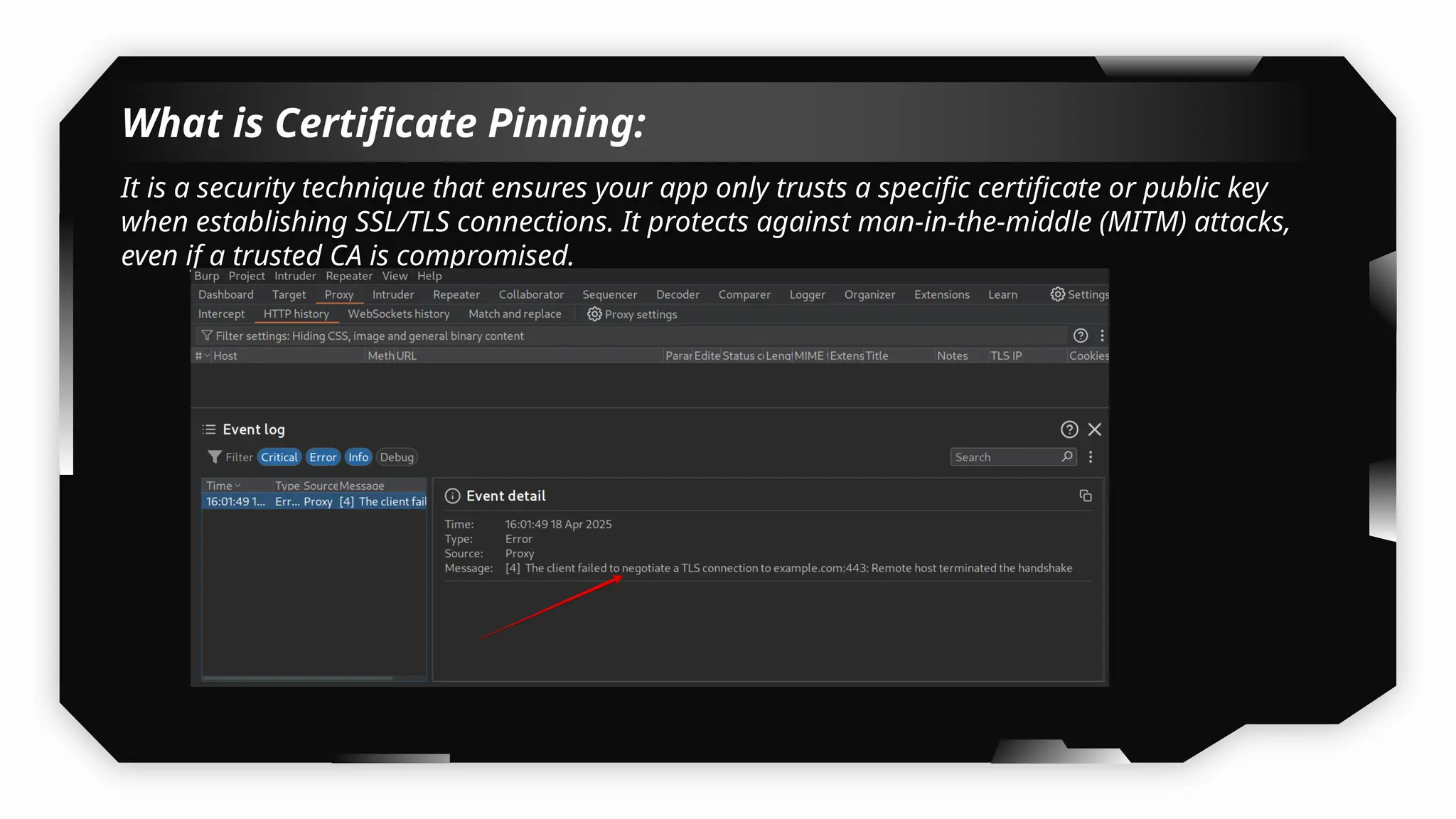
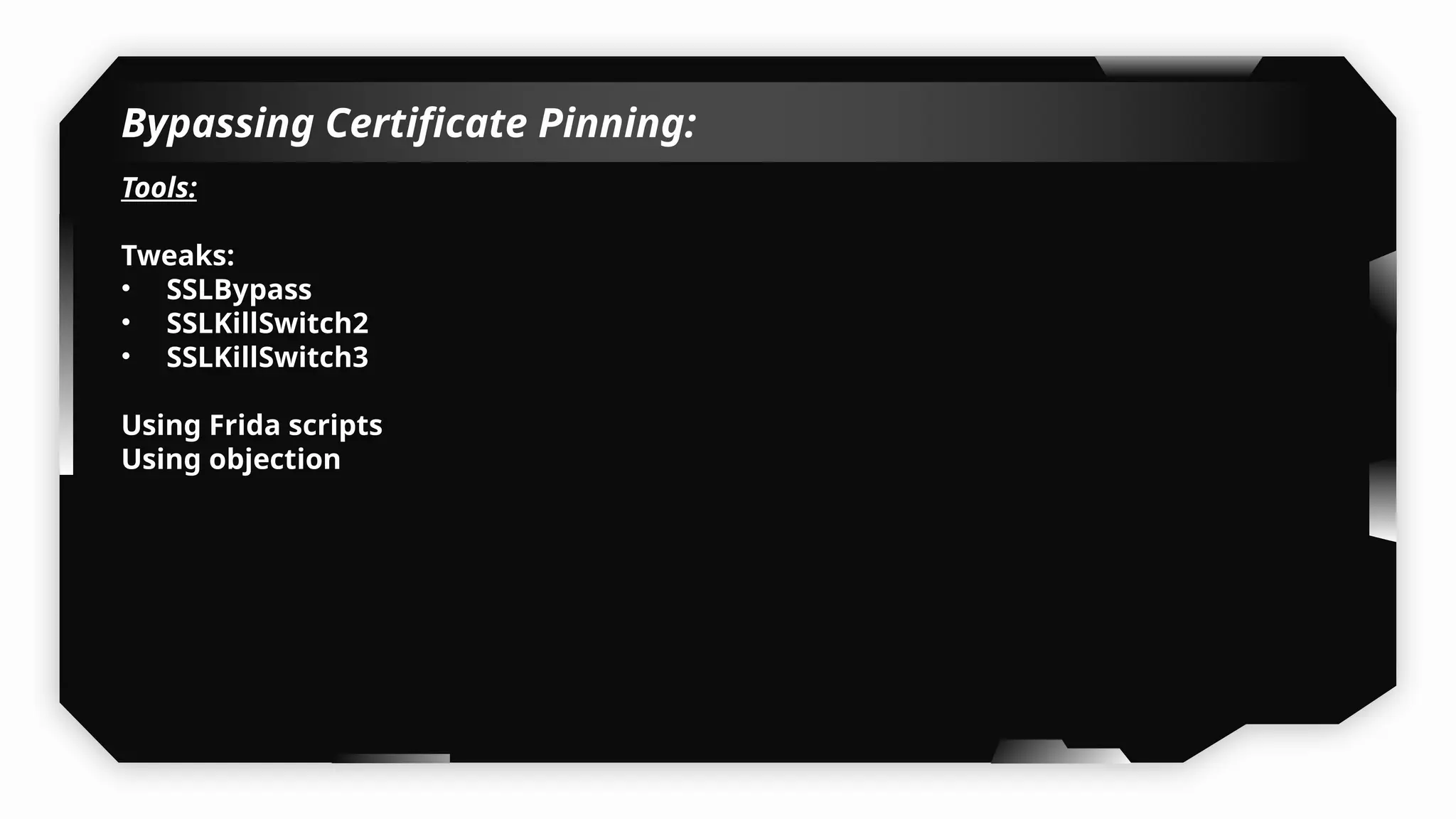
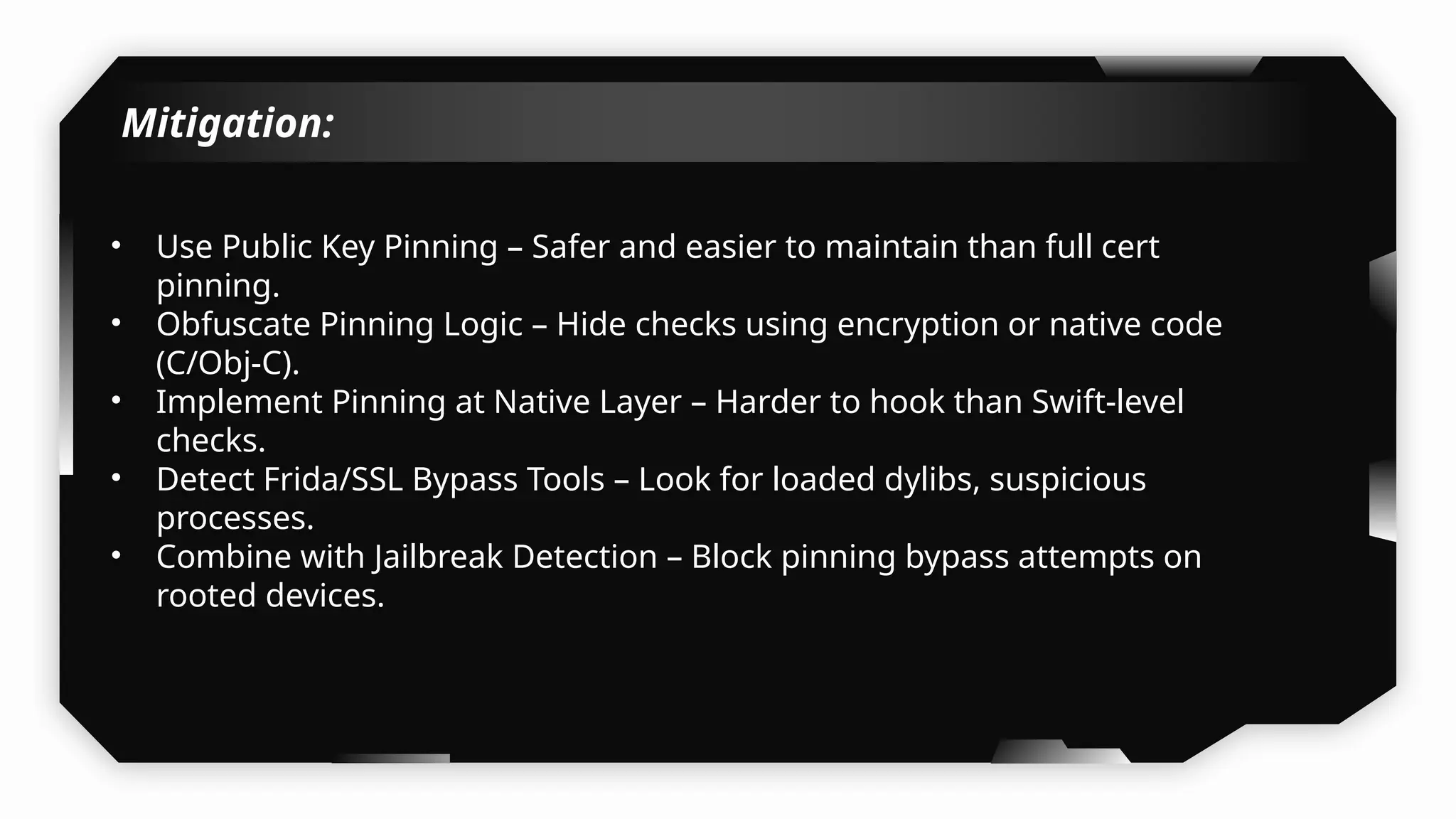
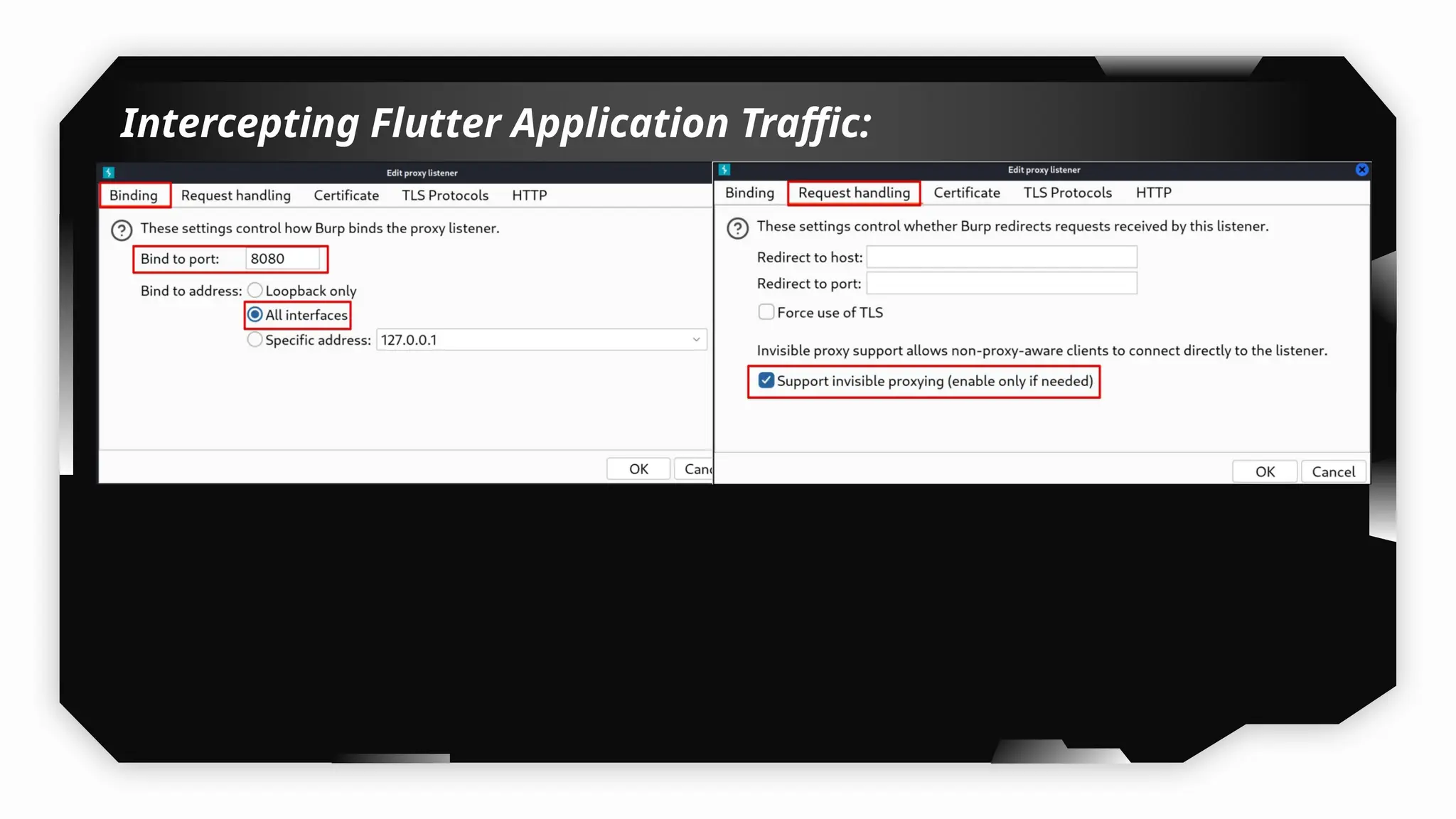
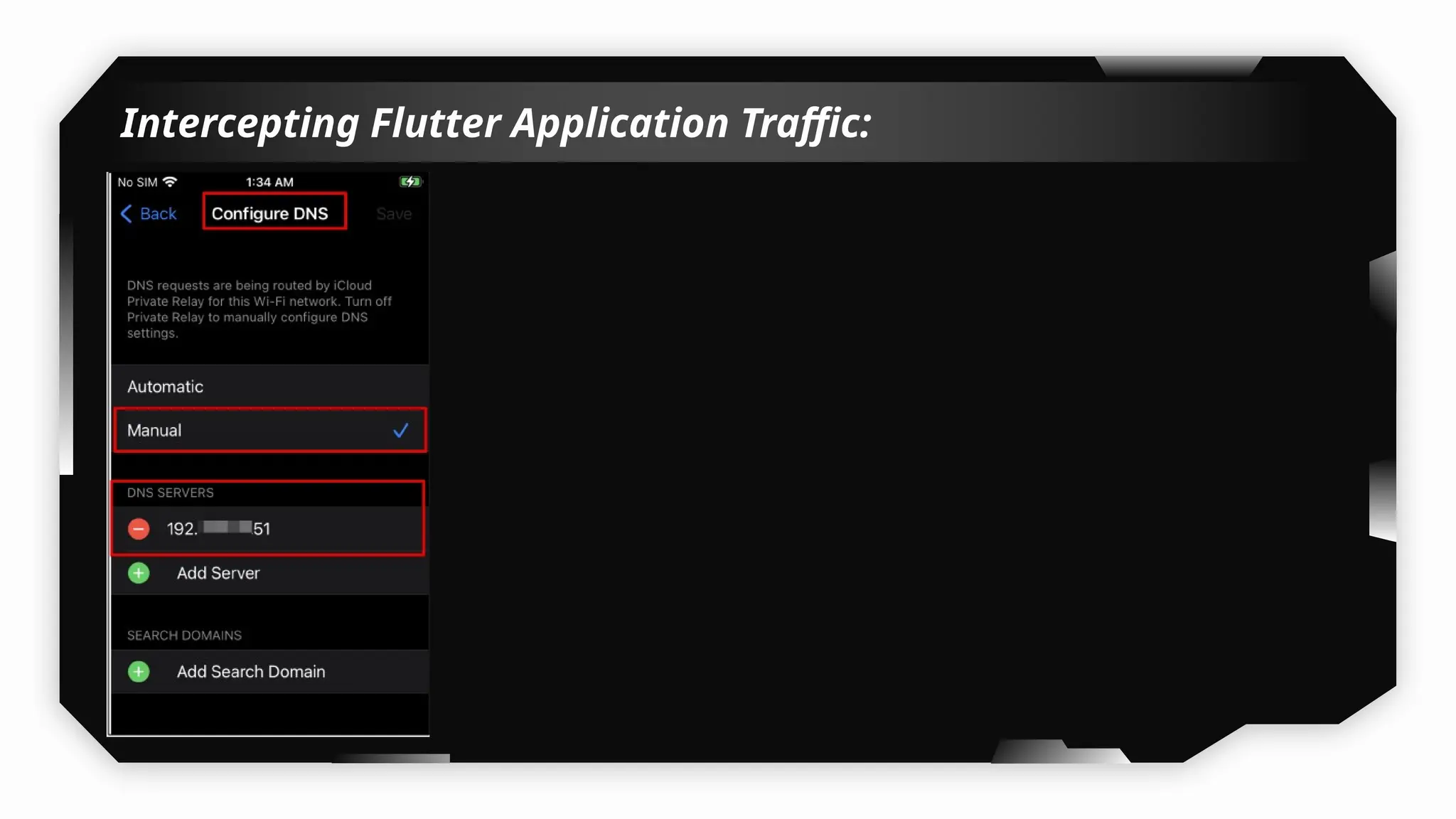
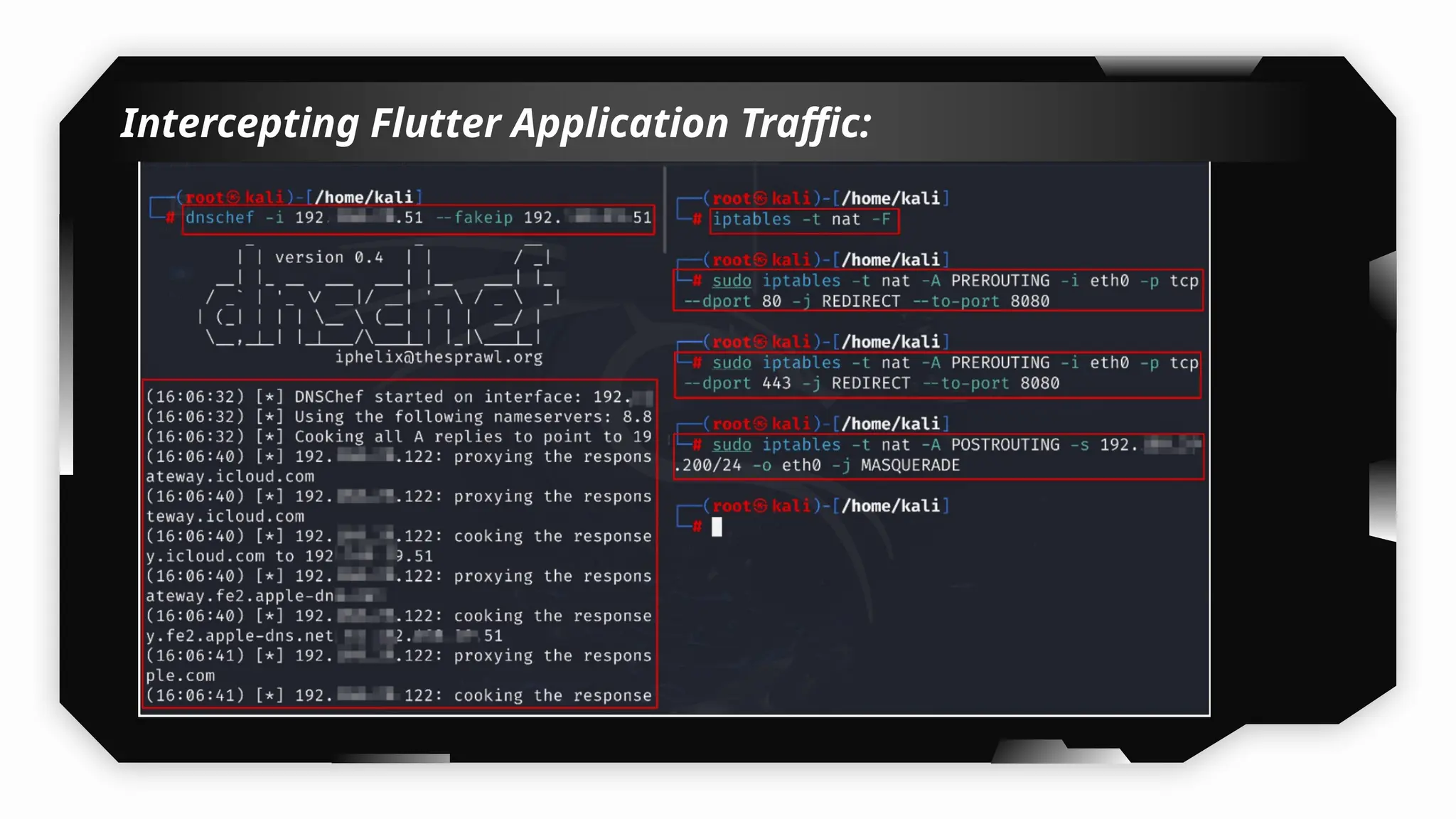
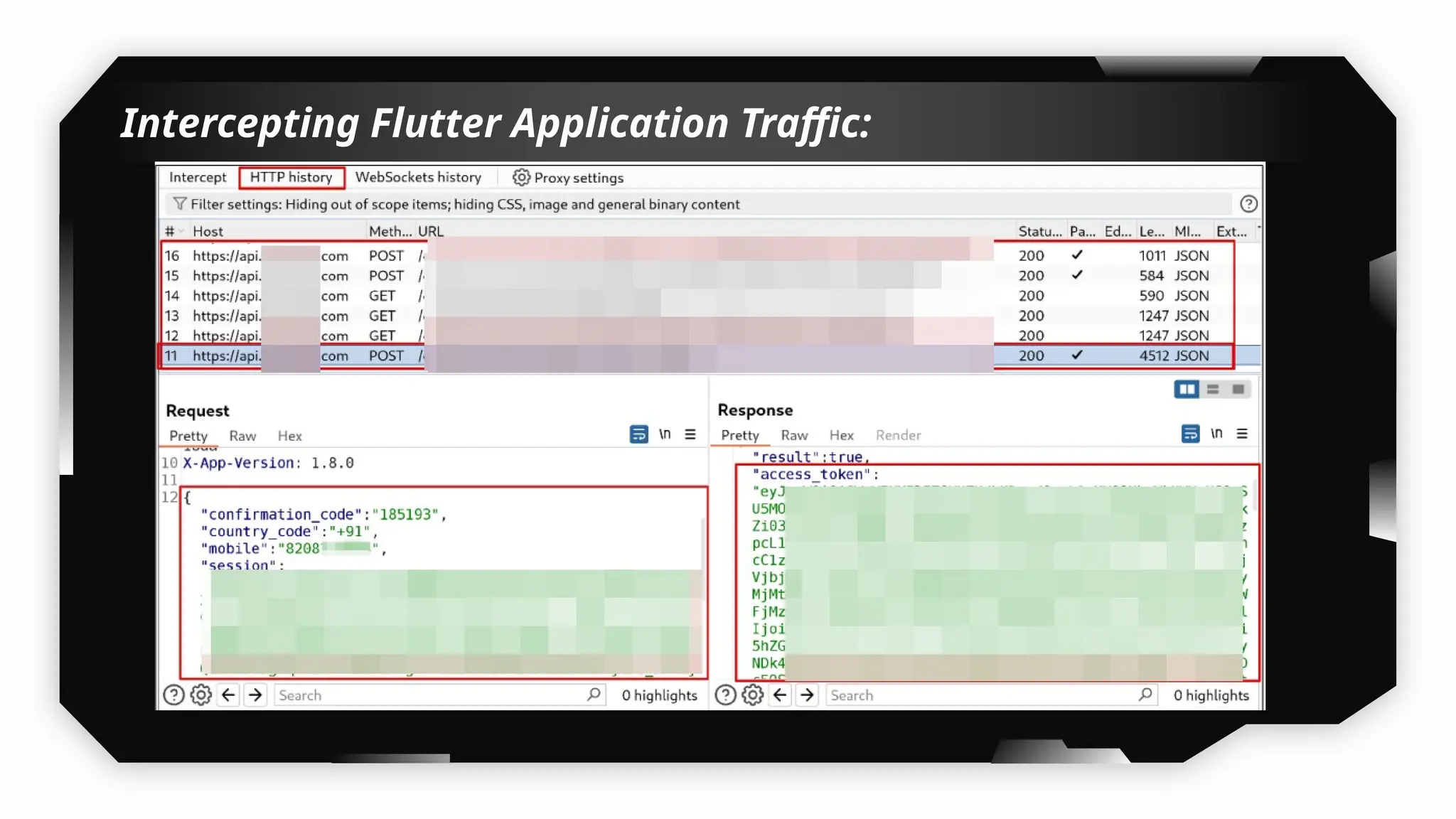
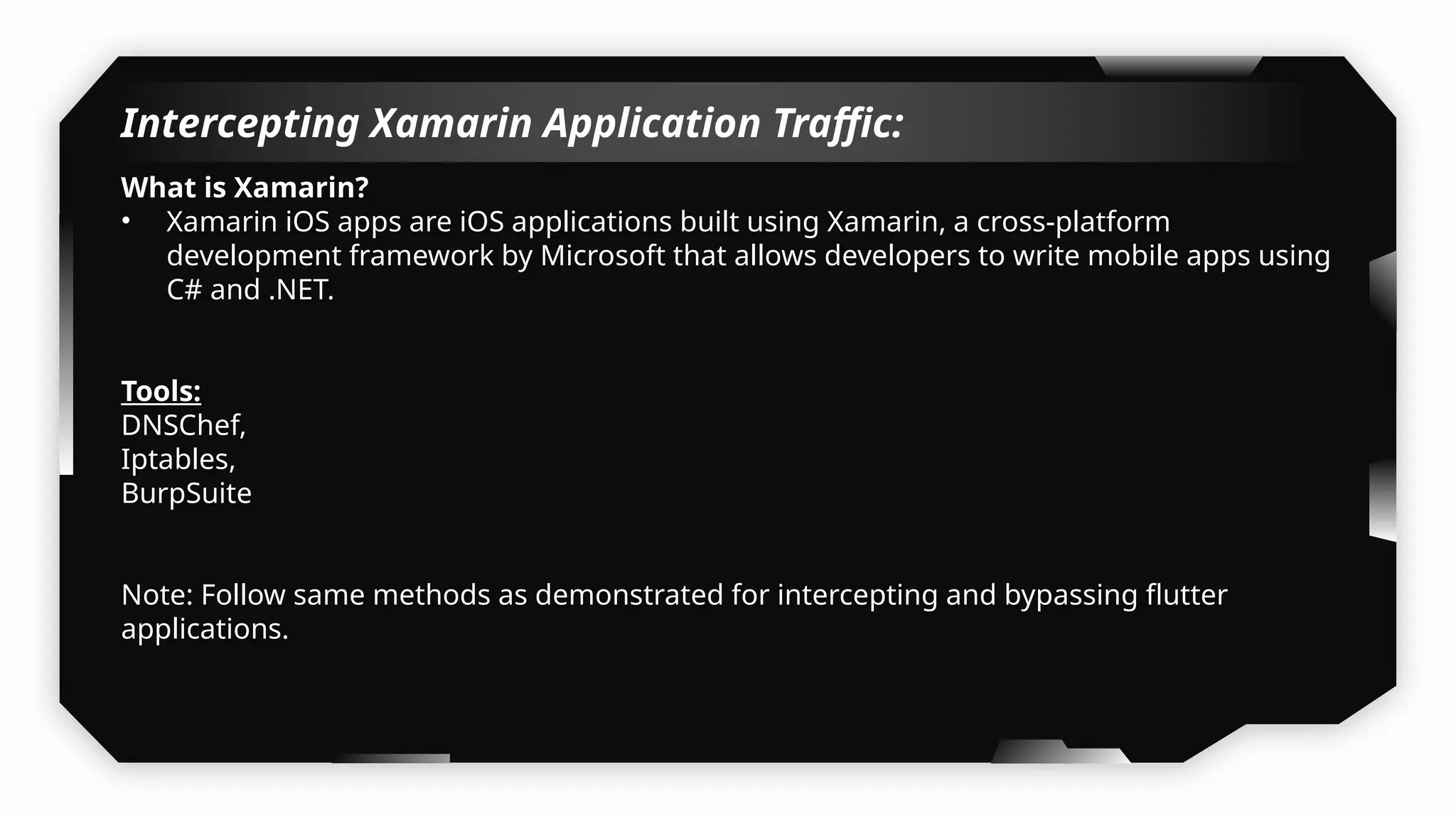
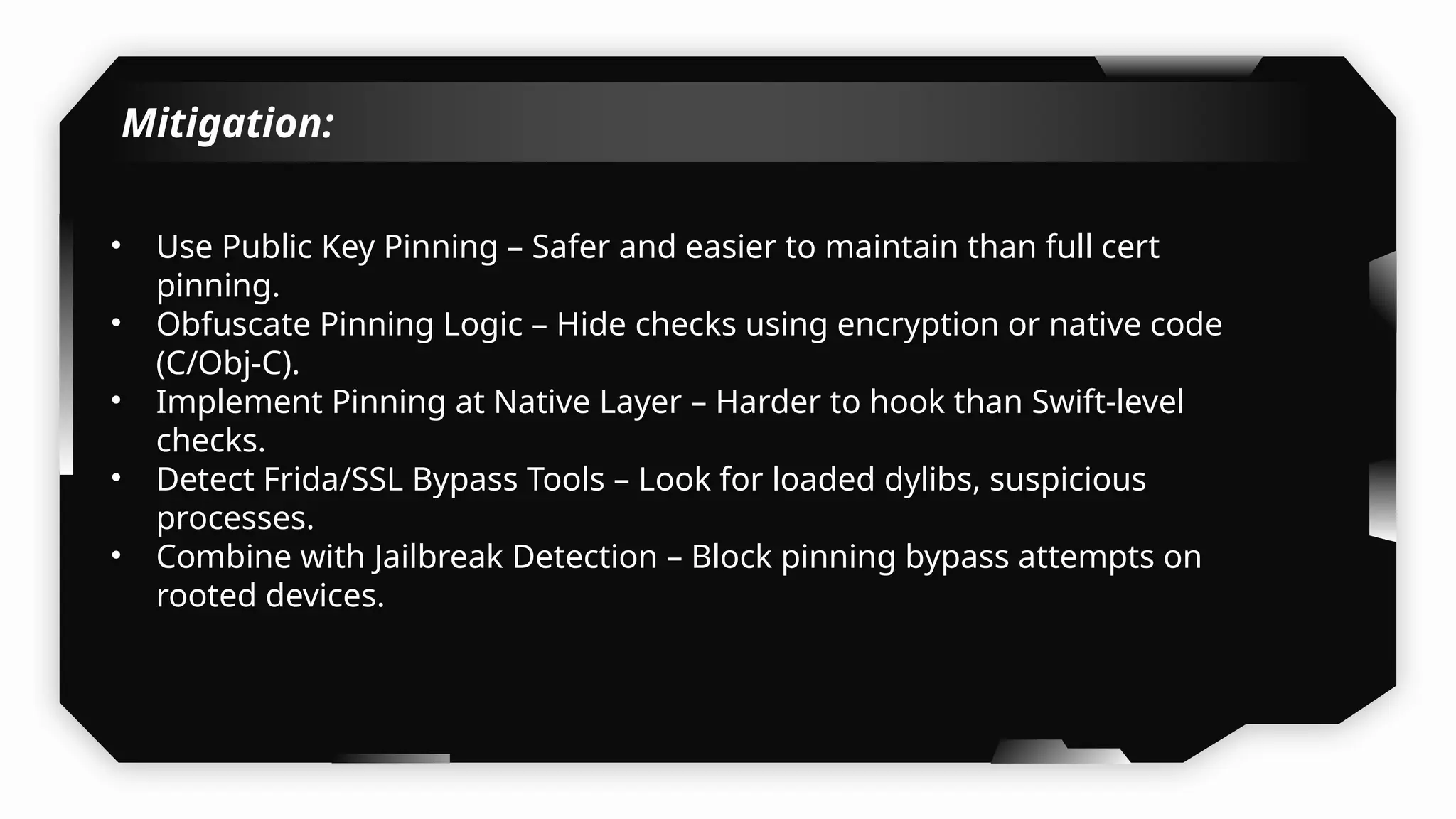
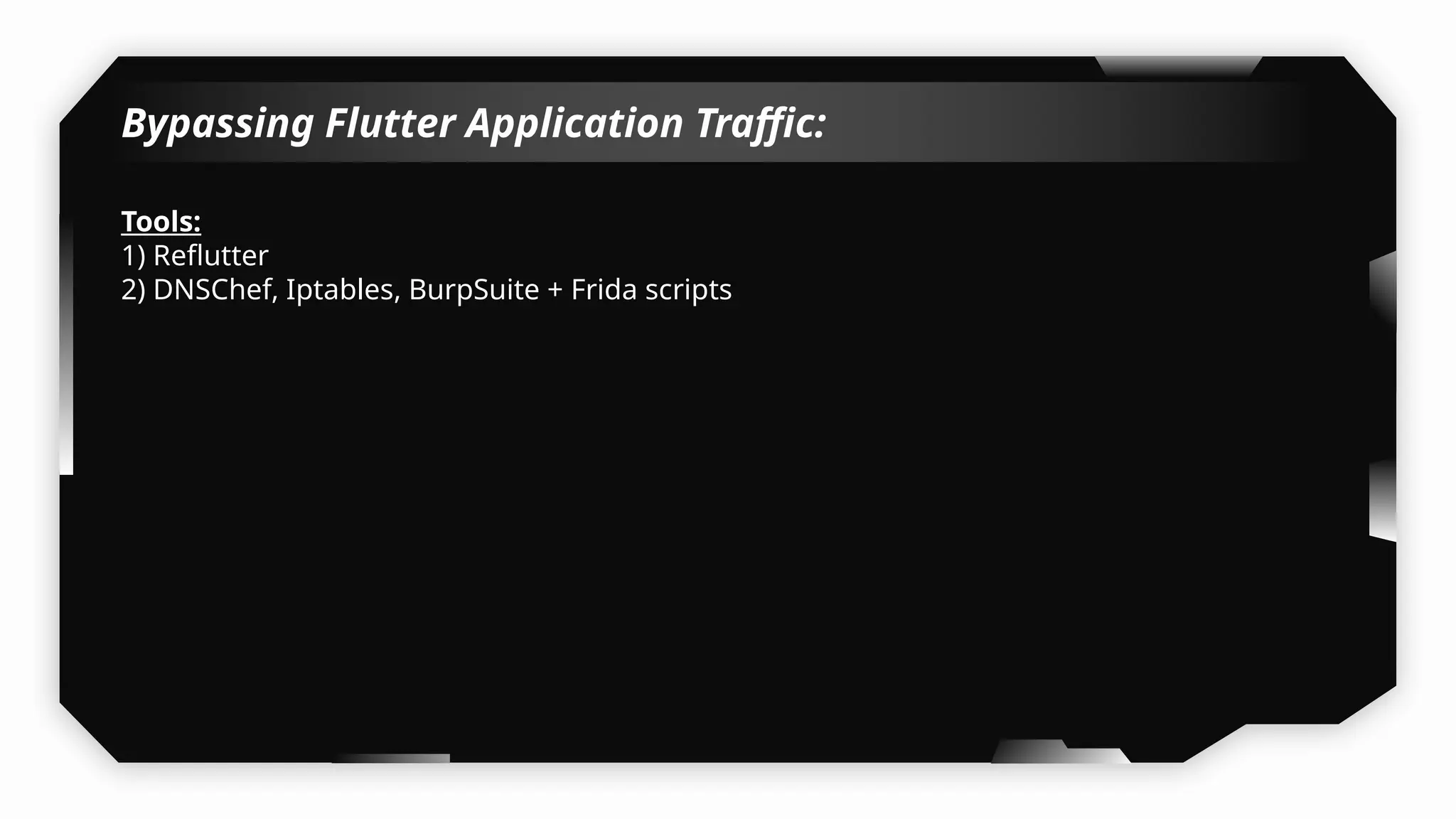
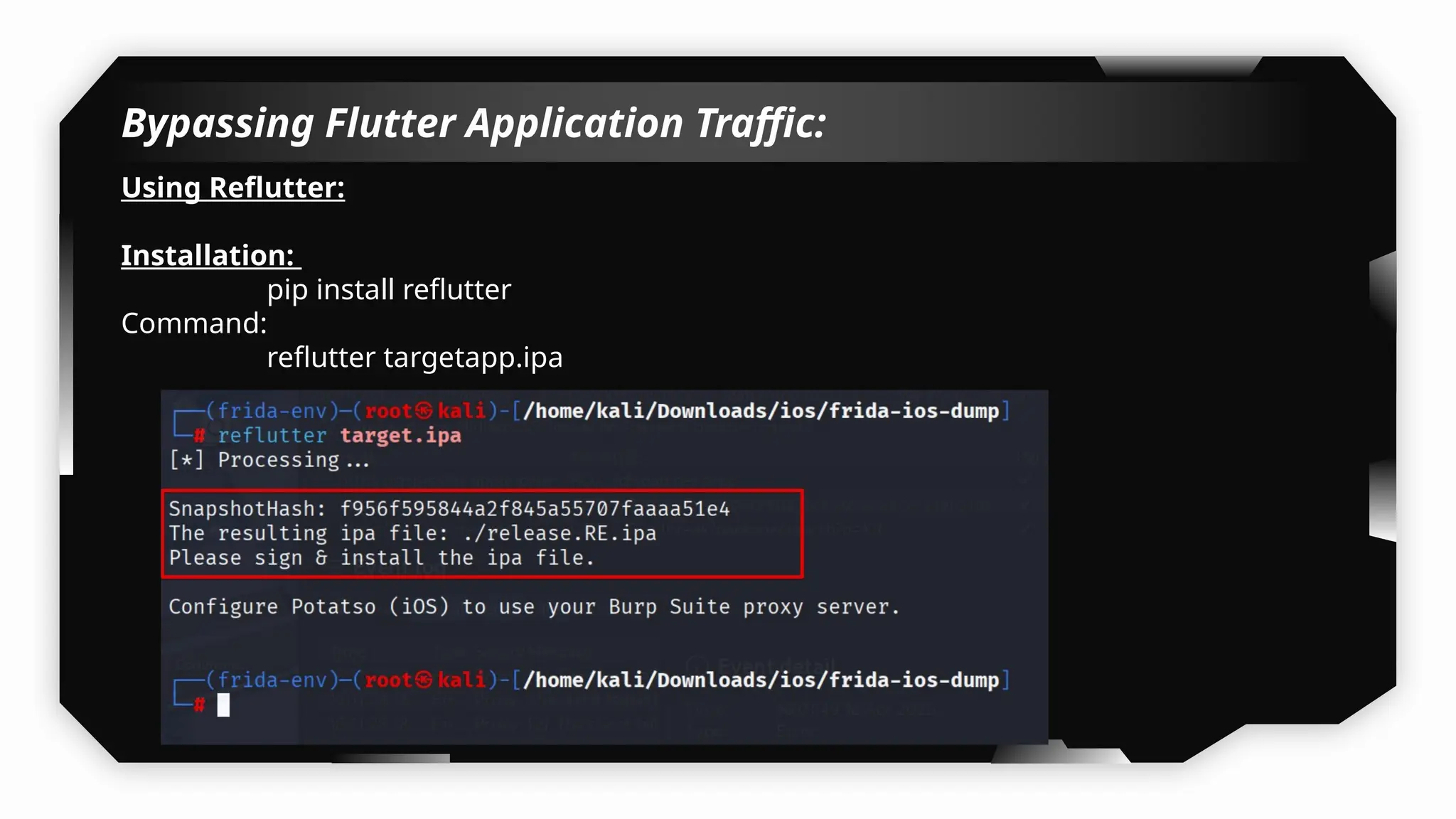
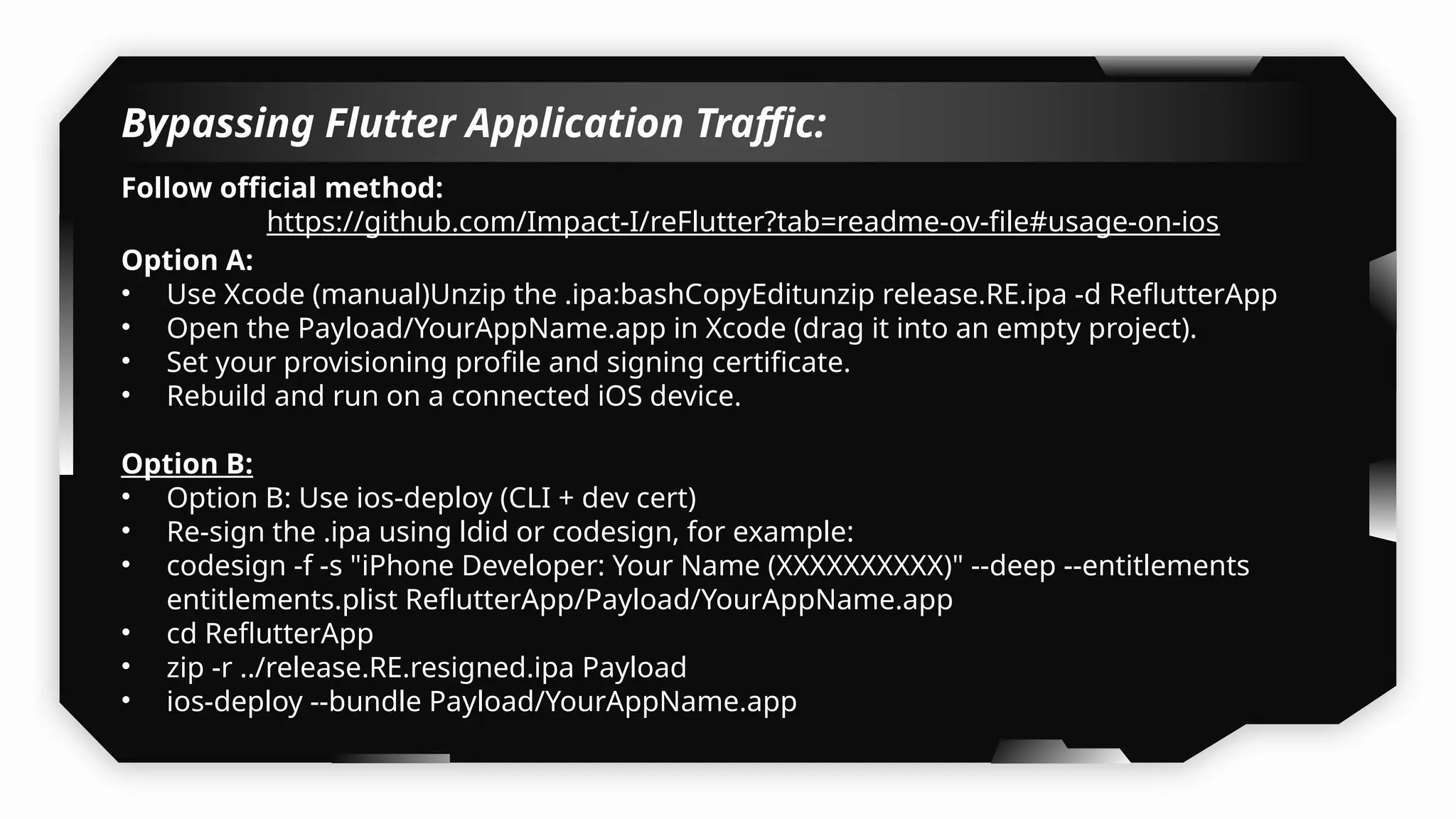
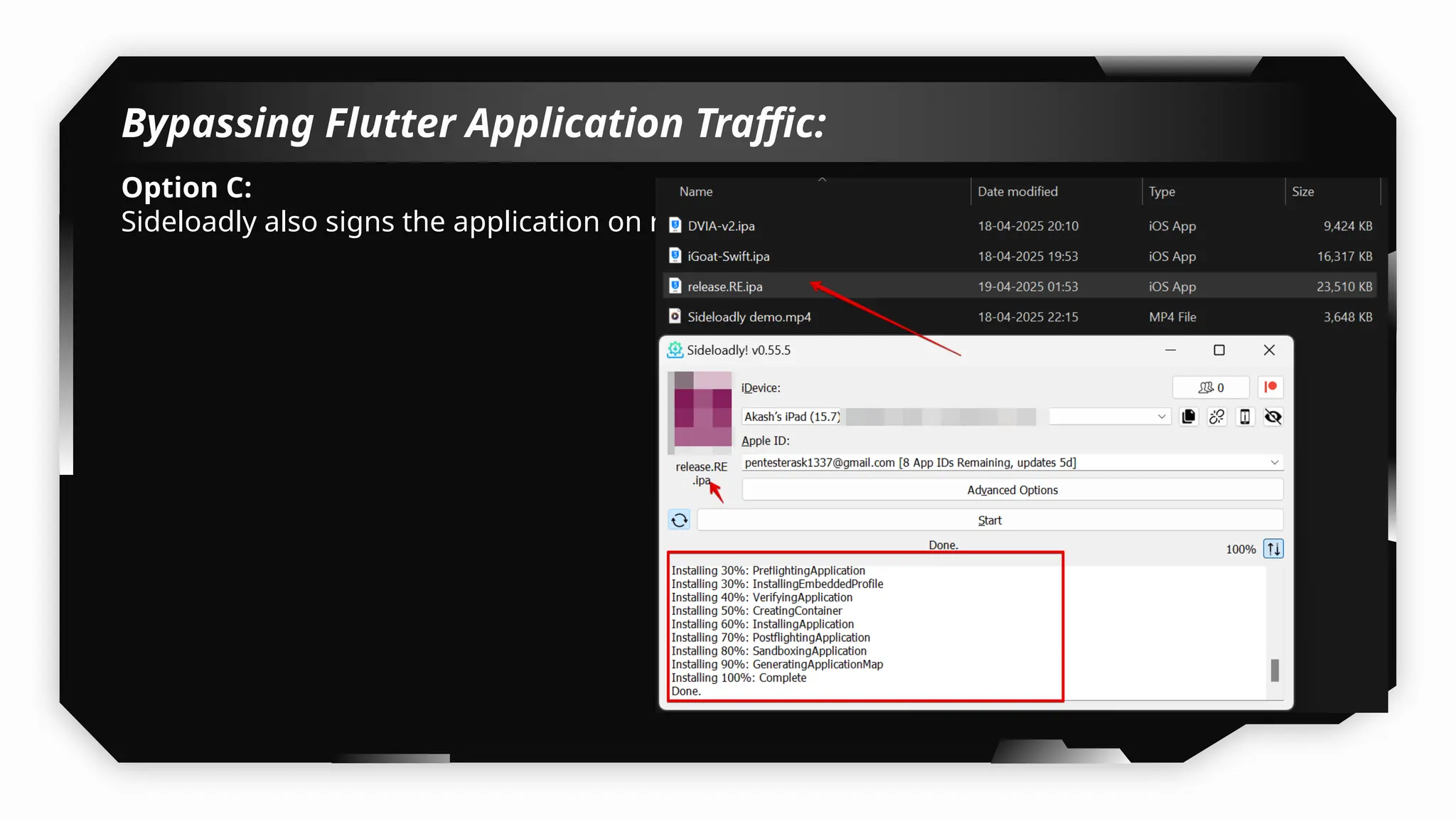
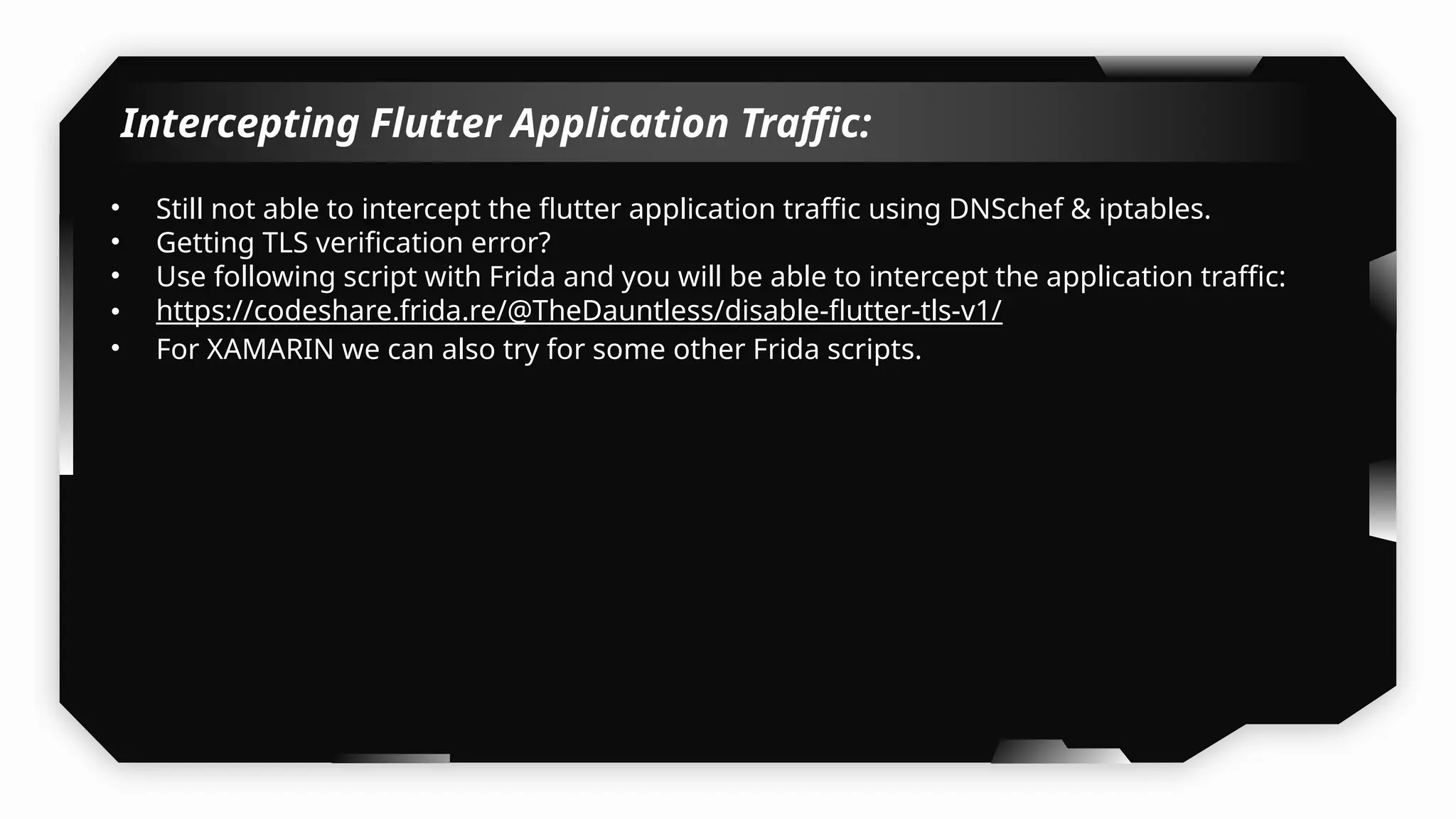
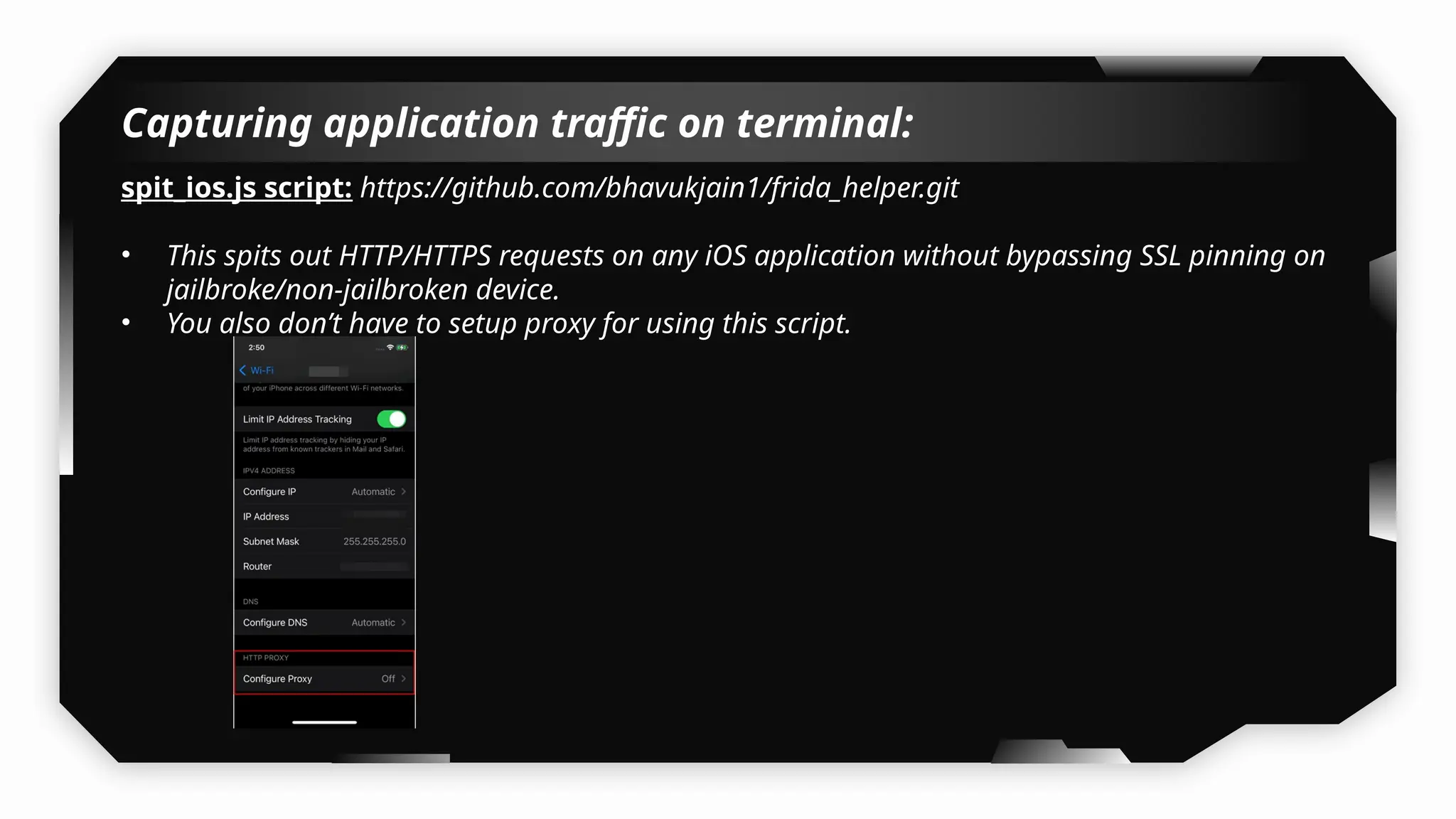
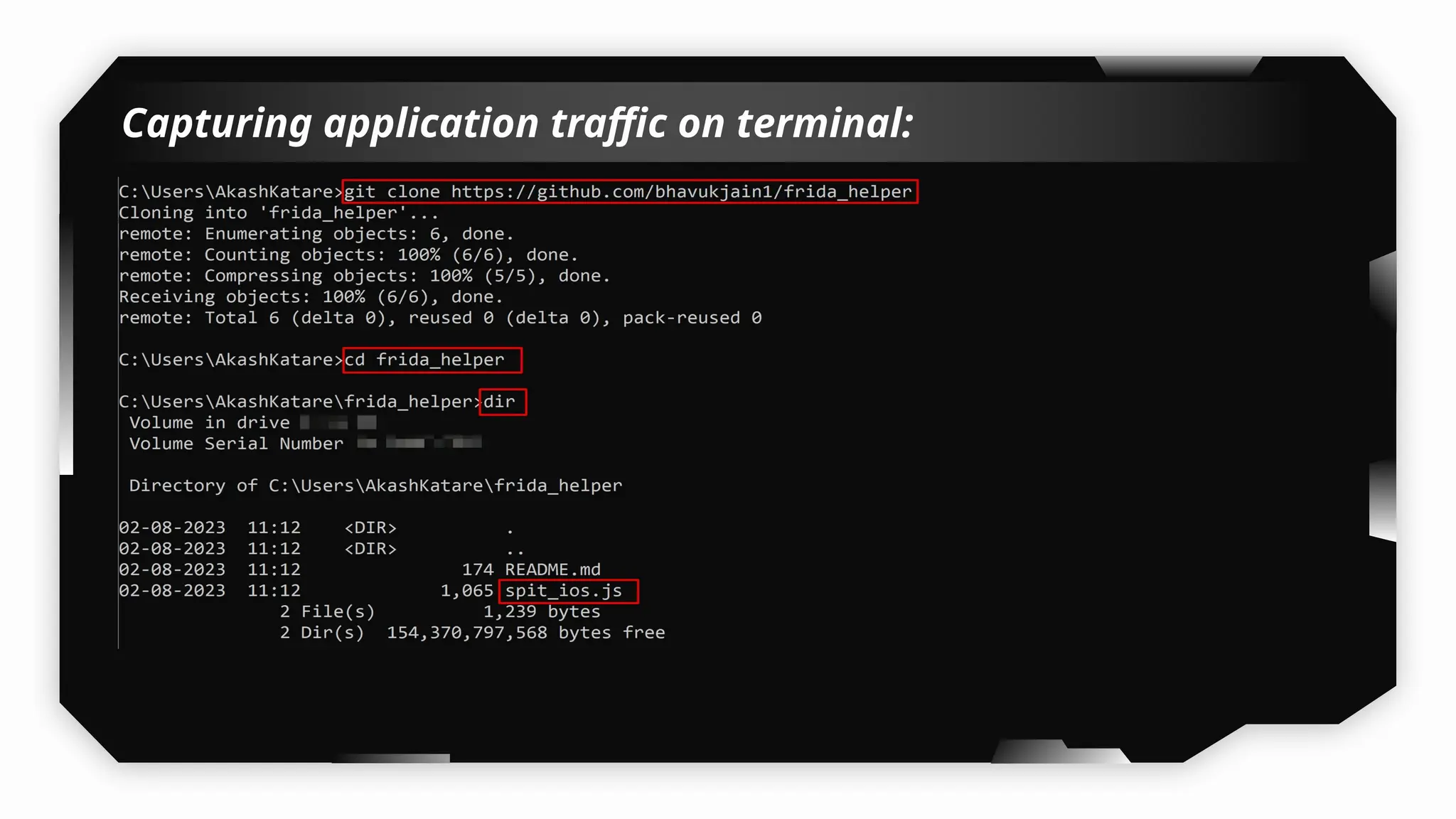
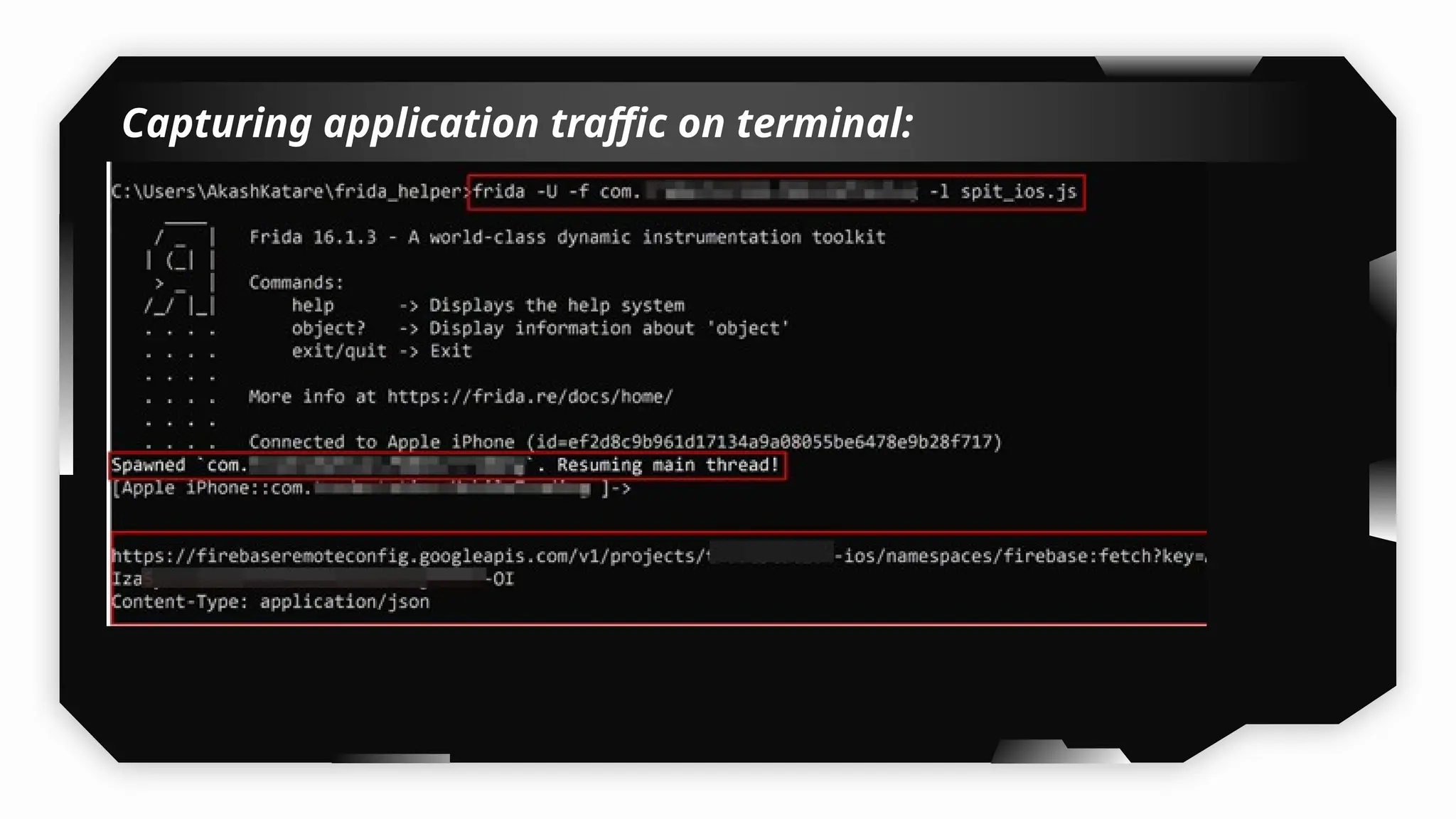
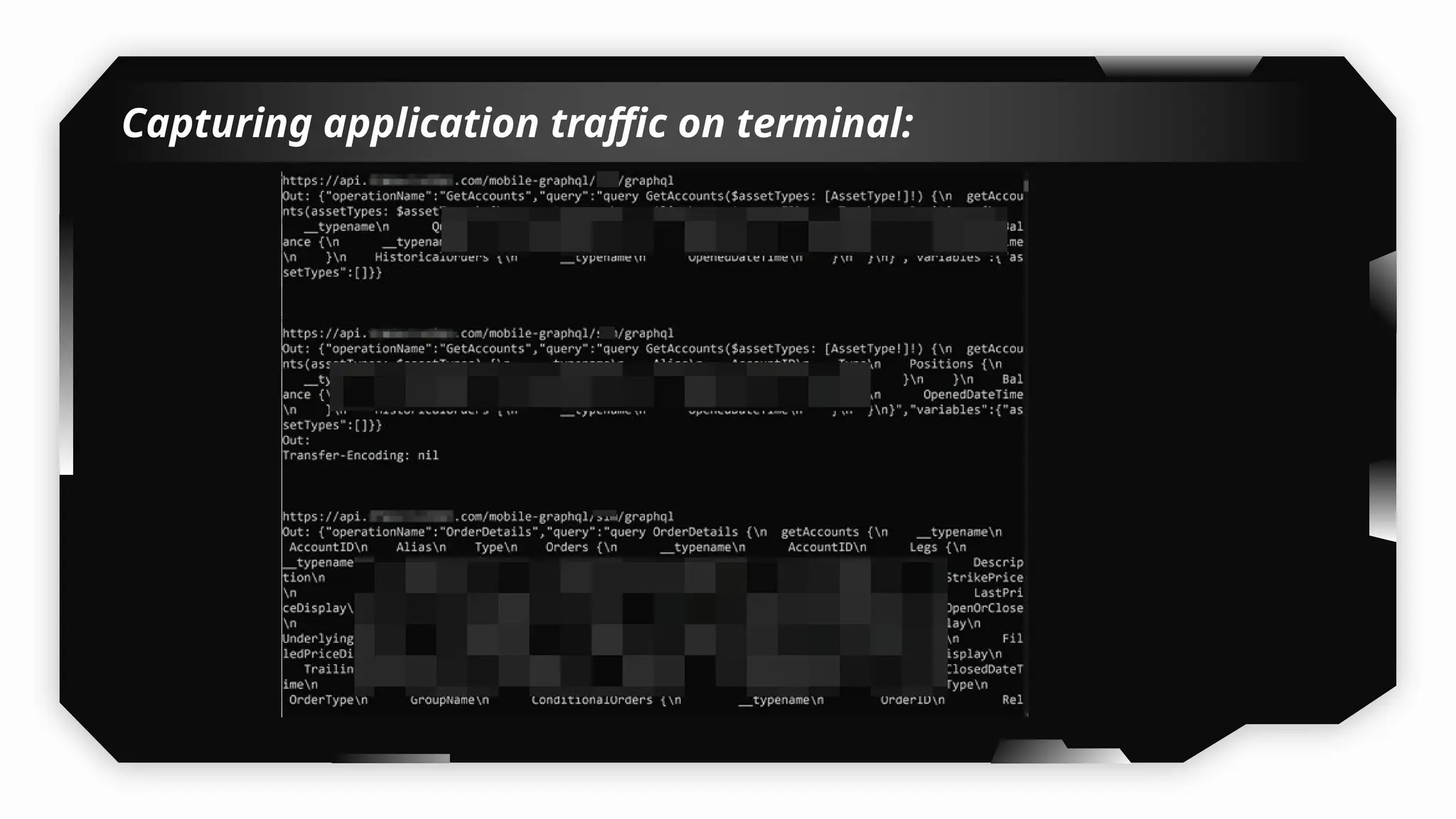
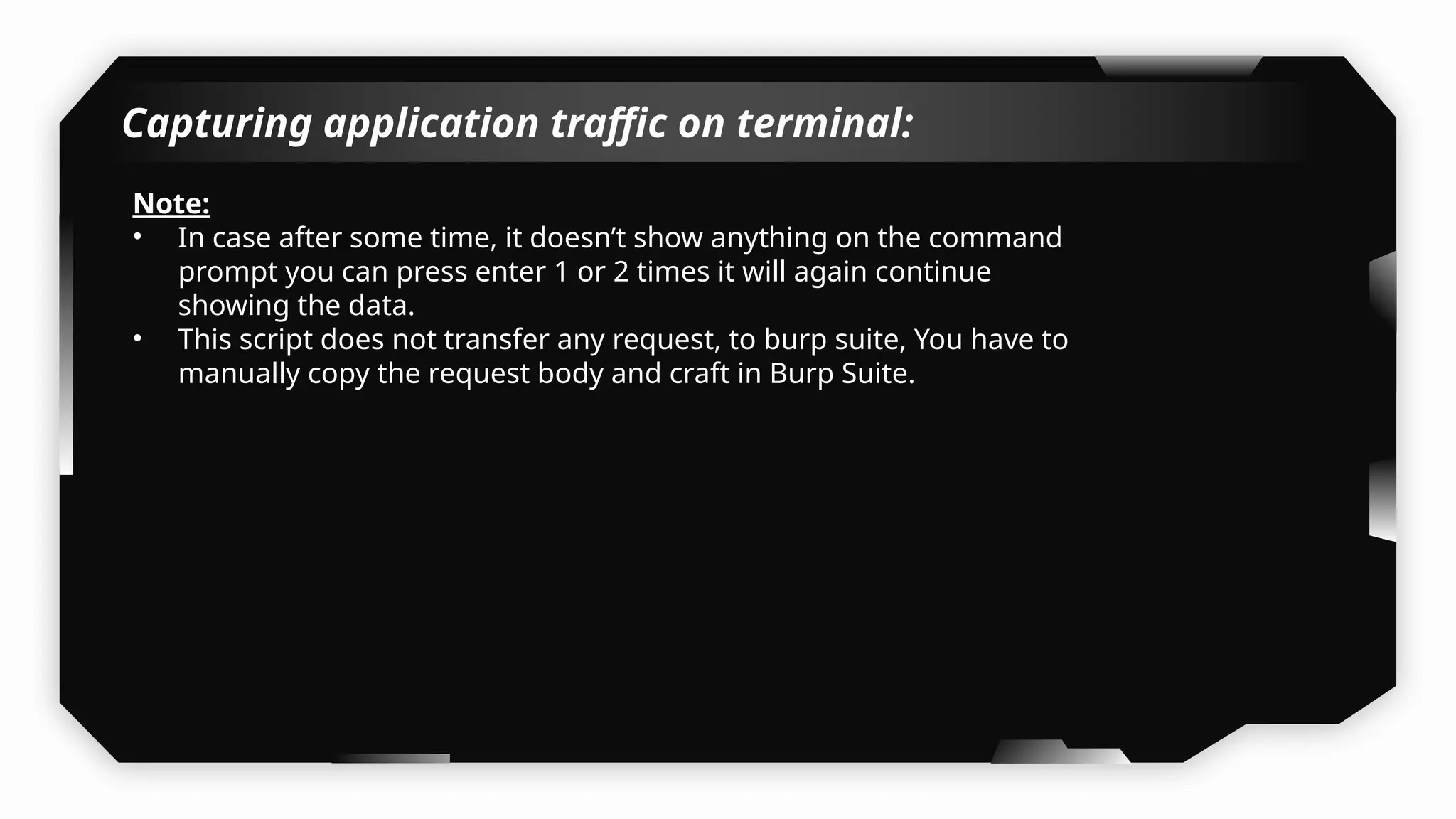
I have also covered common vulnerabilities such as local storage security, binary protection, and keychain data leaks, with practical demonstrations of tools like Filza and Objection. The advanced testing section delves into bypassing jailbreak detection, intercepting traffic, and attacking SSL/TLS certificate pinning in Swift, Flutter, and XAMARIN apps.
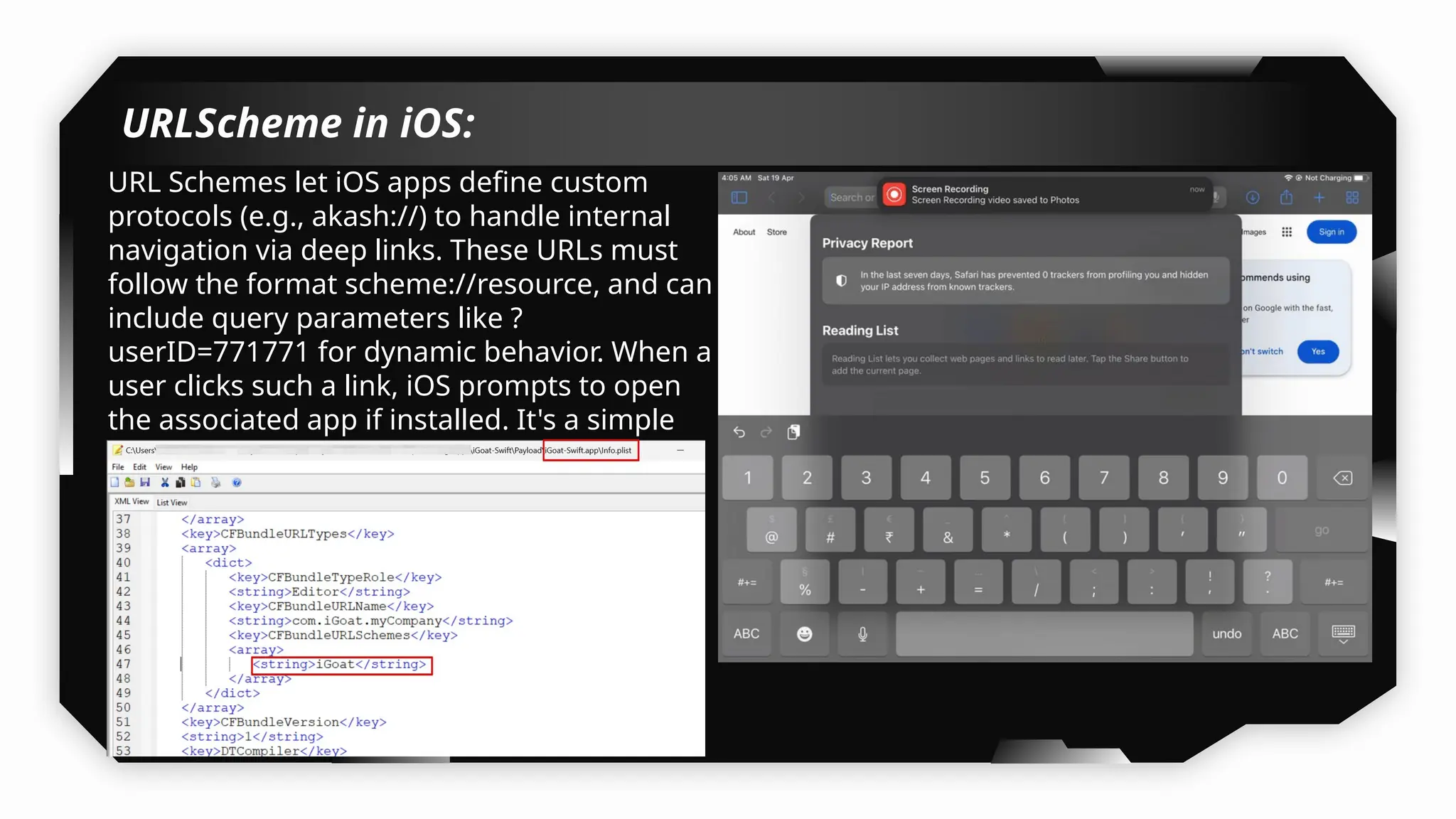
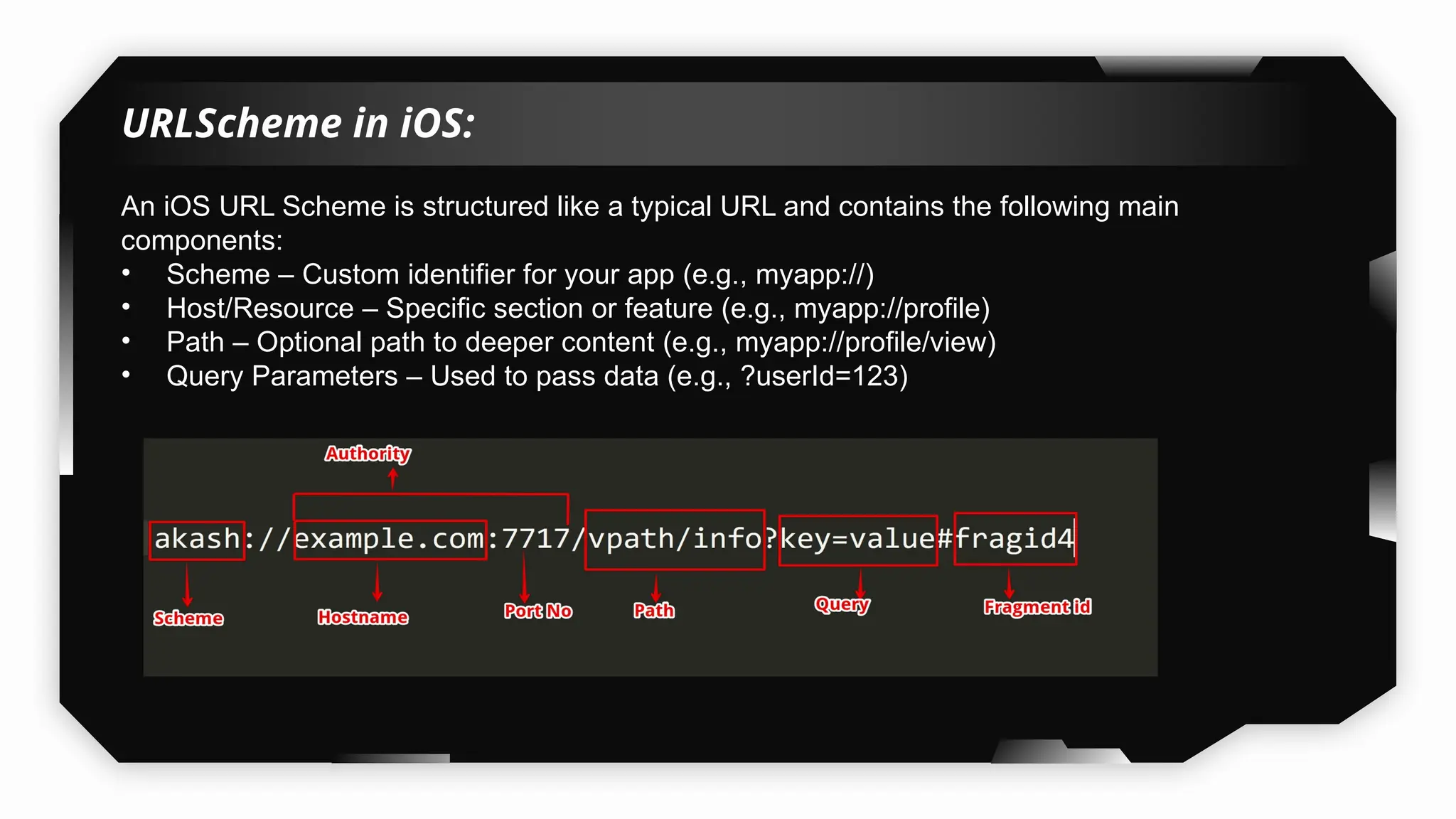
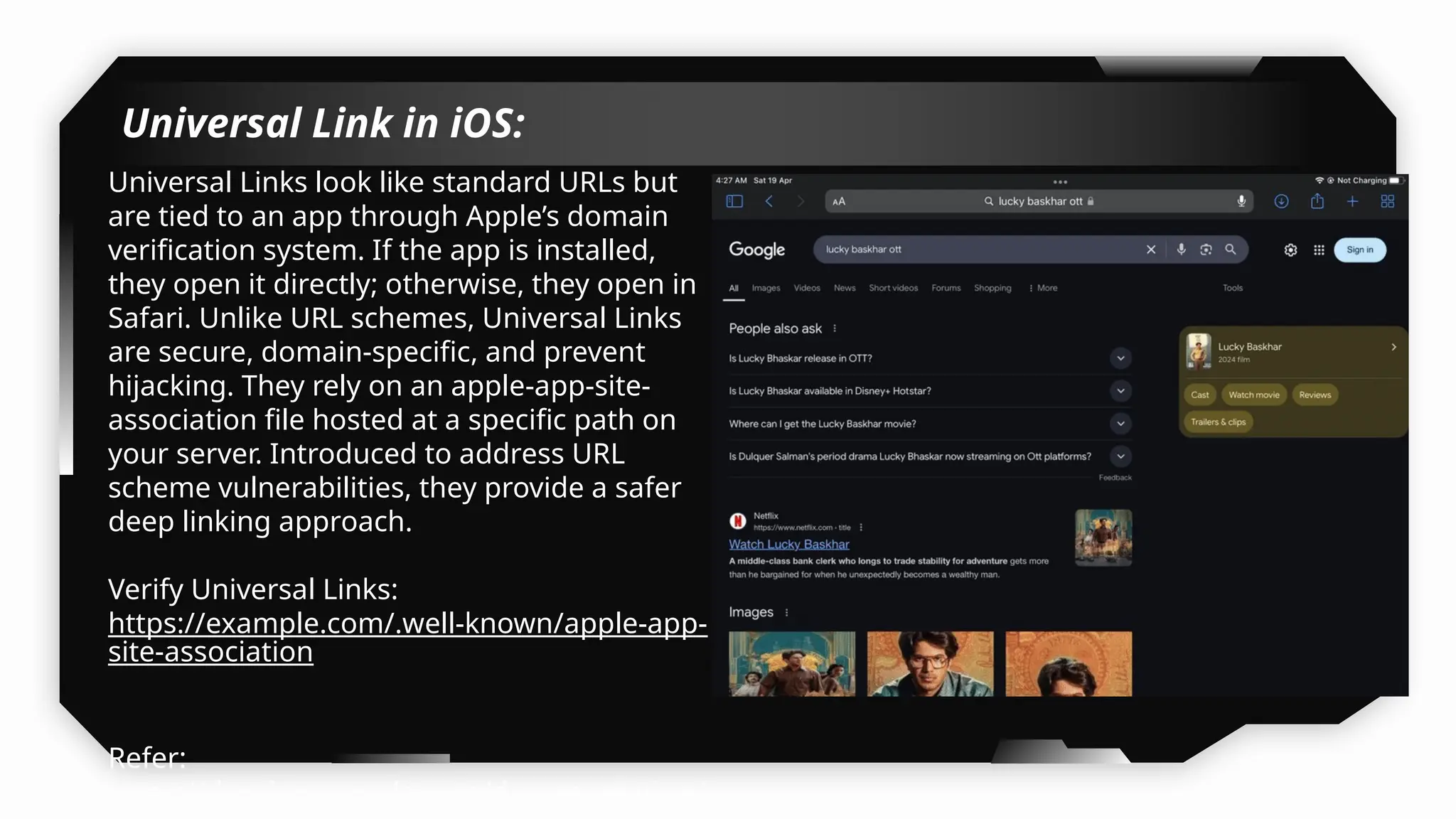
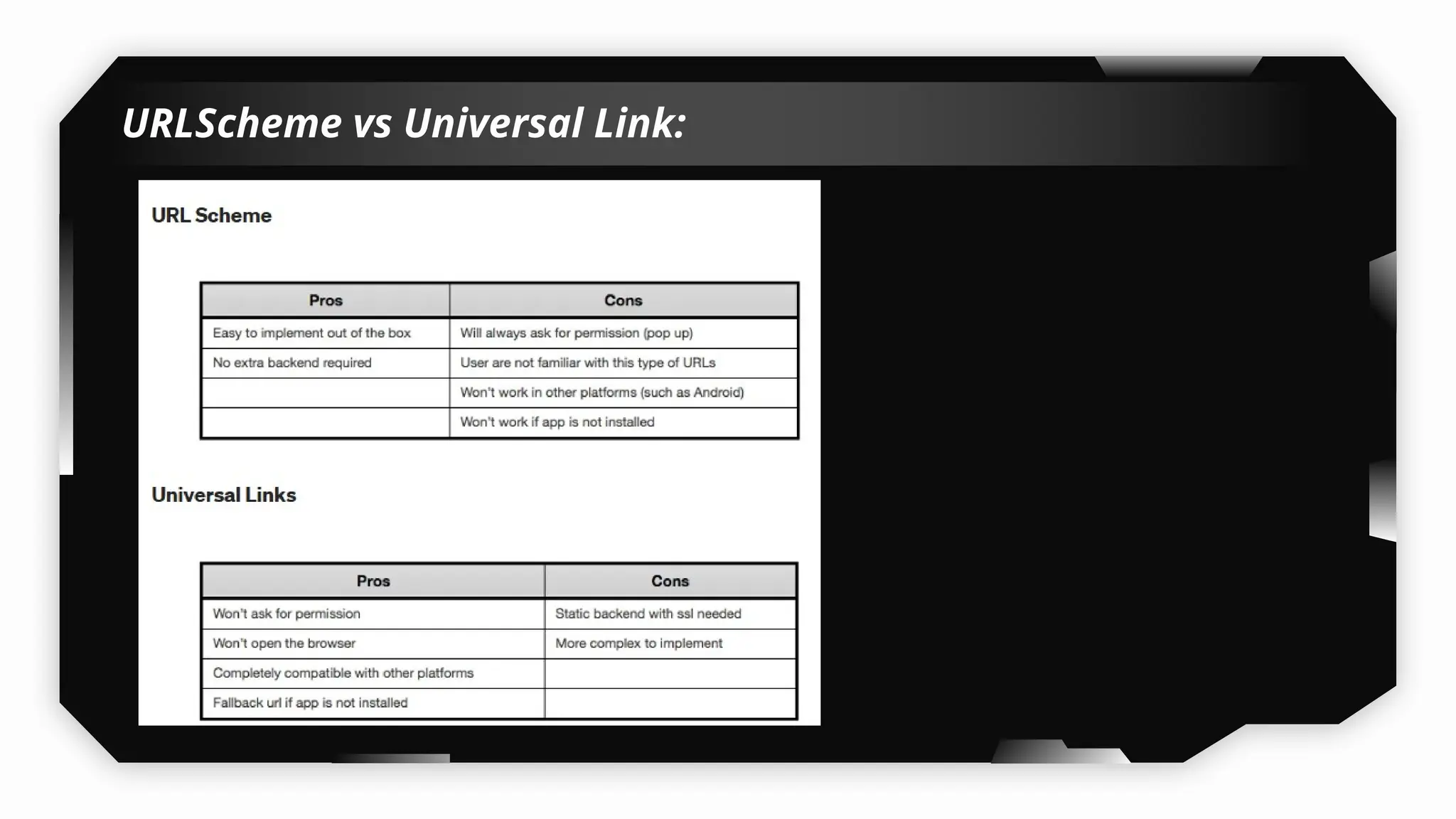
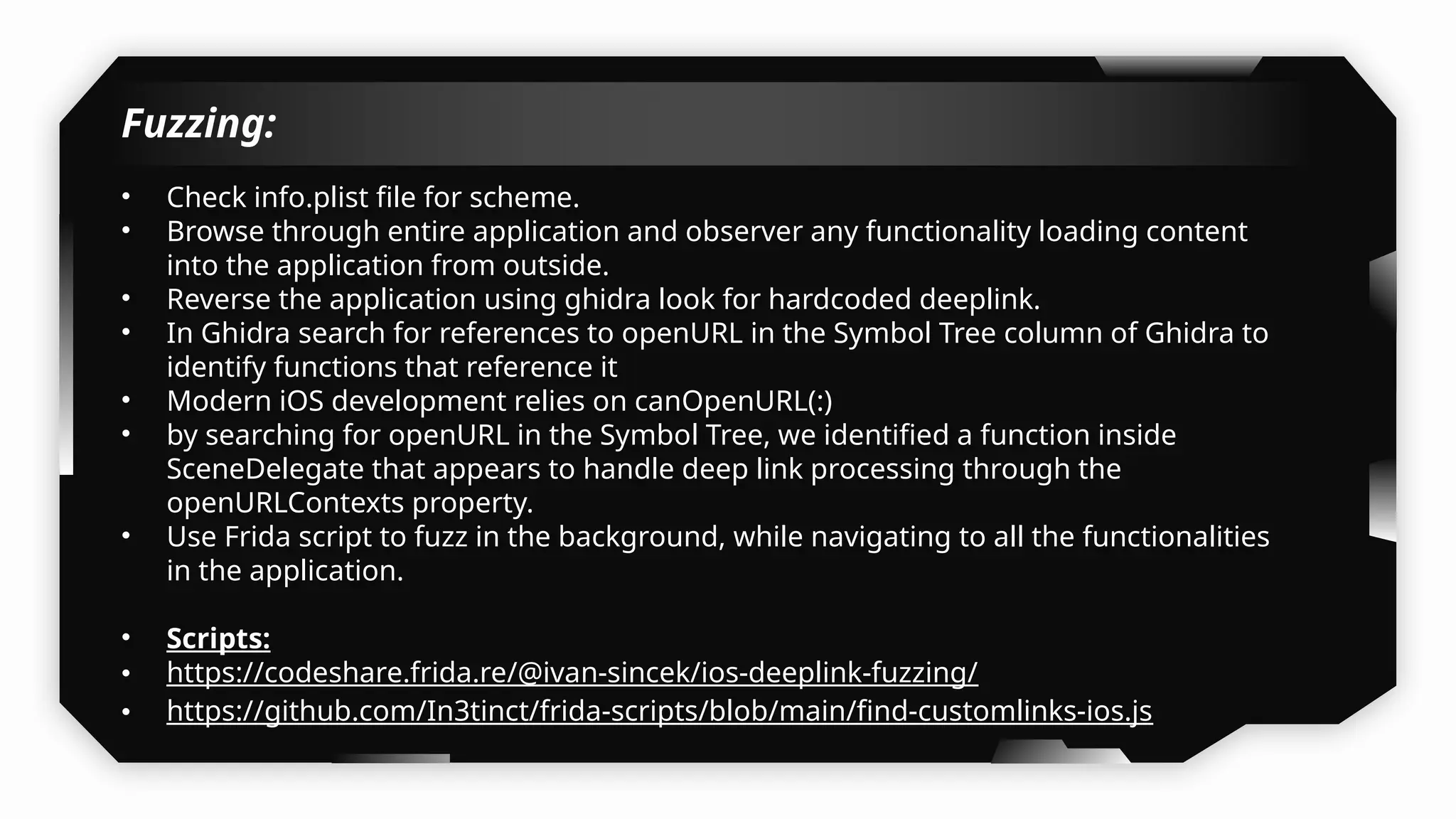
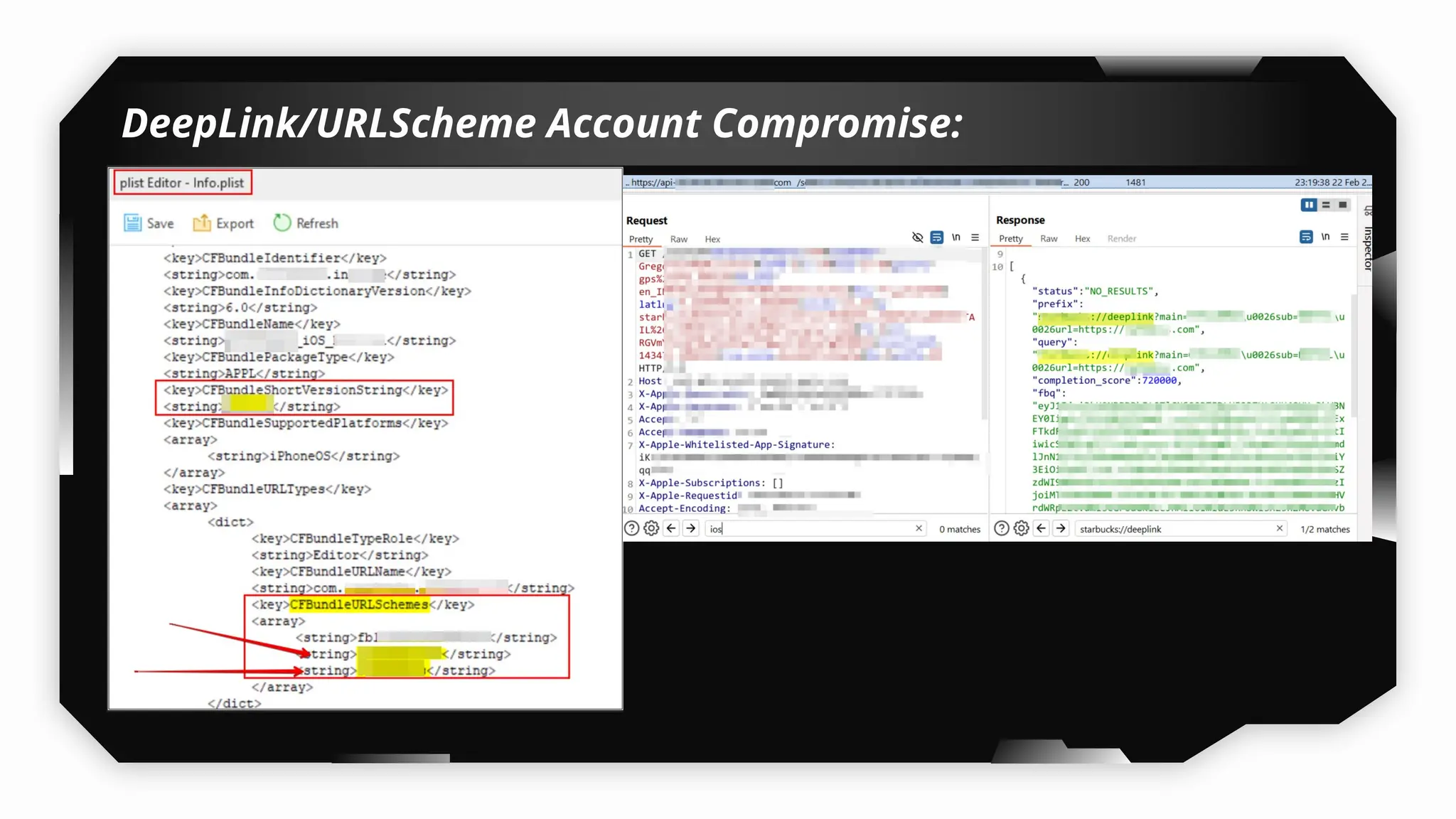
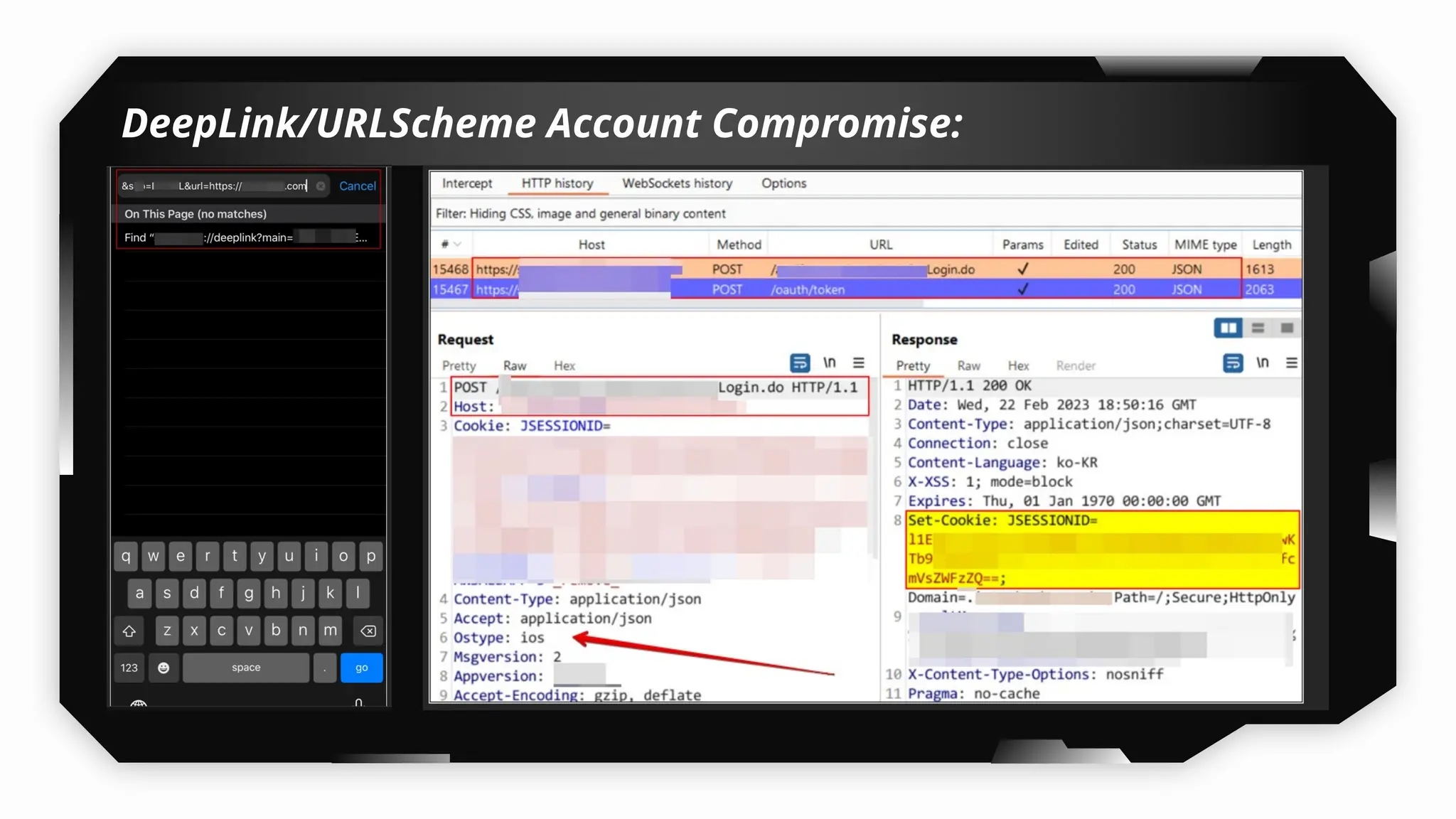
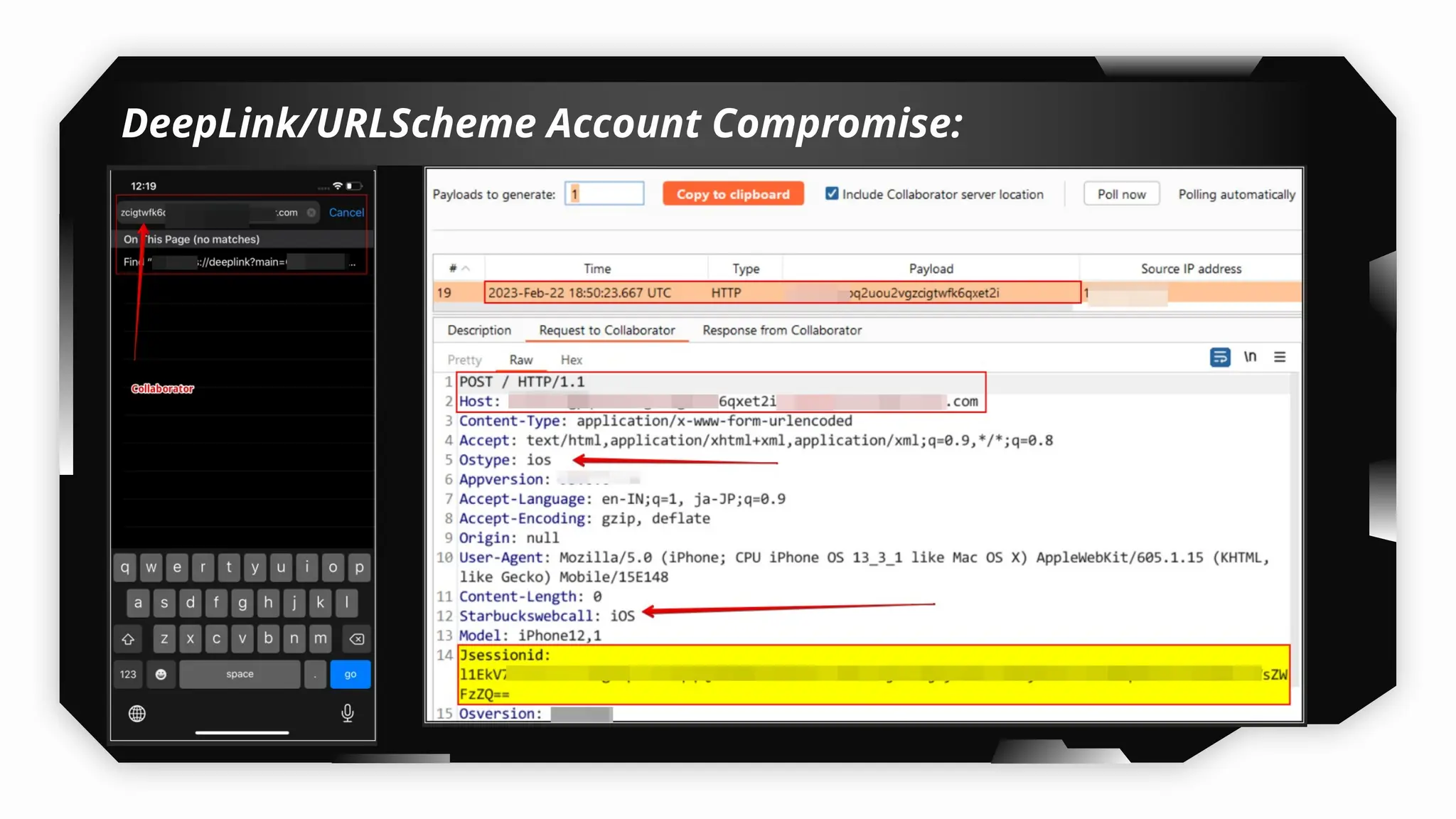
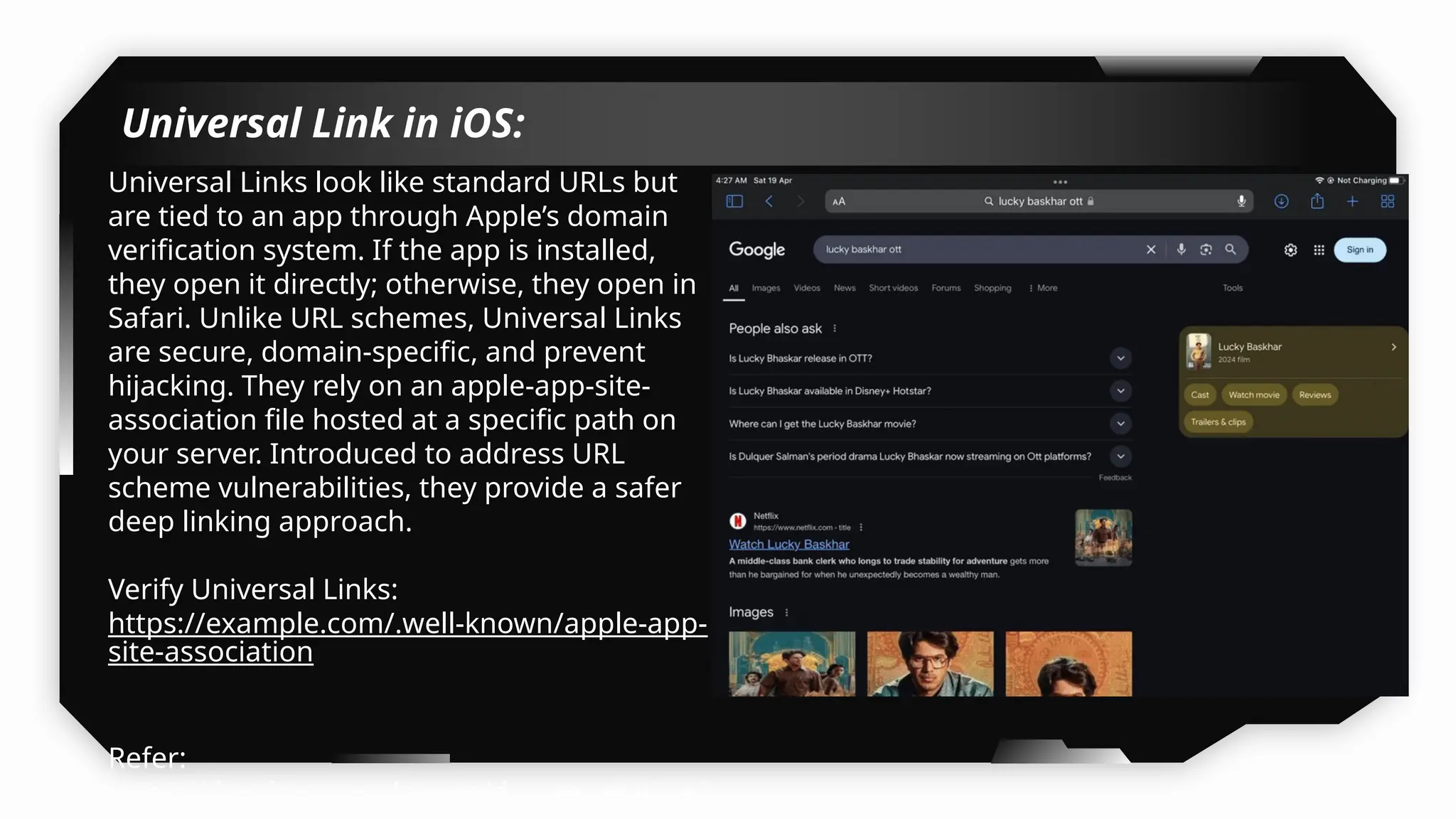
Finally, the session explores the exploitation of DeepLinking, testing URL schemes and universal links to perform account compromises and bypass host validation, demonstrating real-world attacks on iOS applications through traffic interception and custom script creation. This session is essential for anyone looking to master iOS application pentesting and vulnerability assessment.