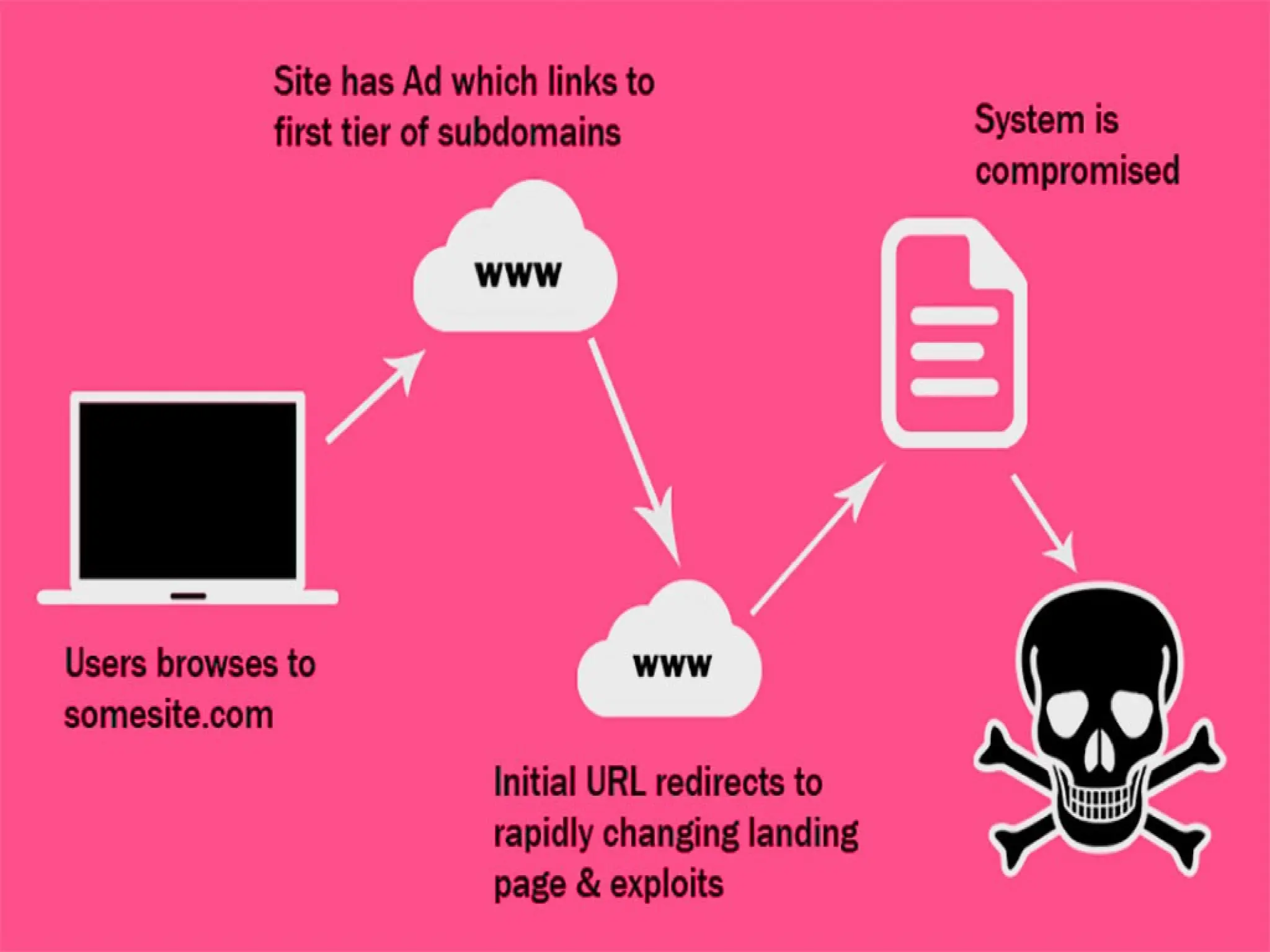
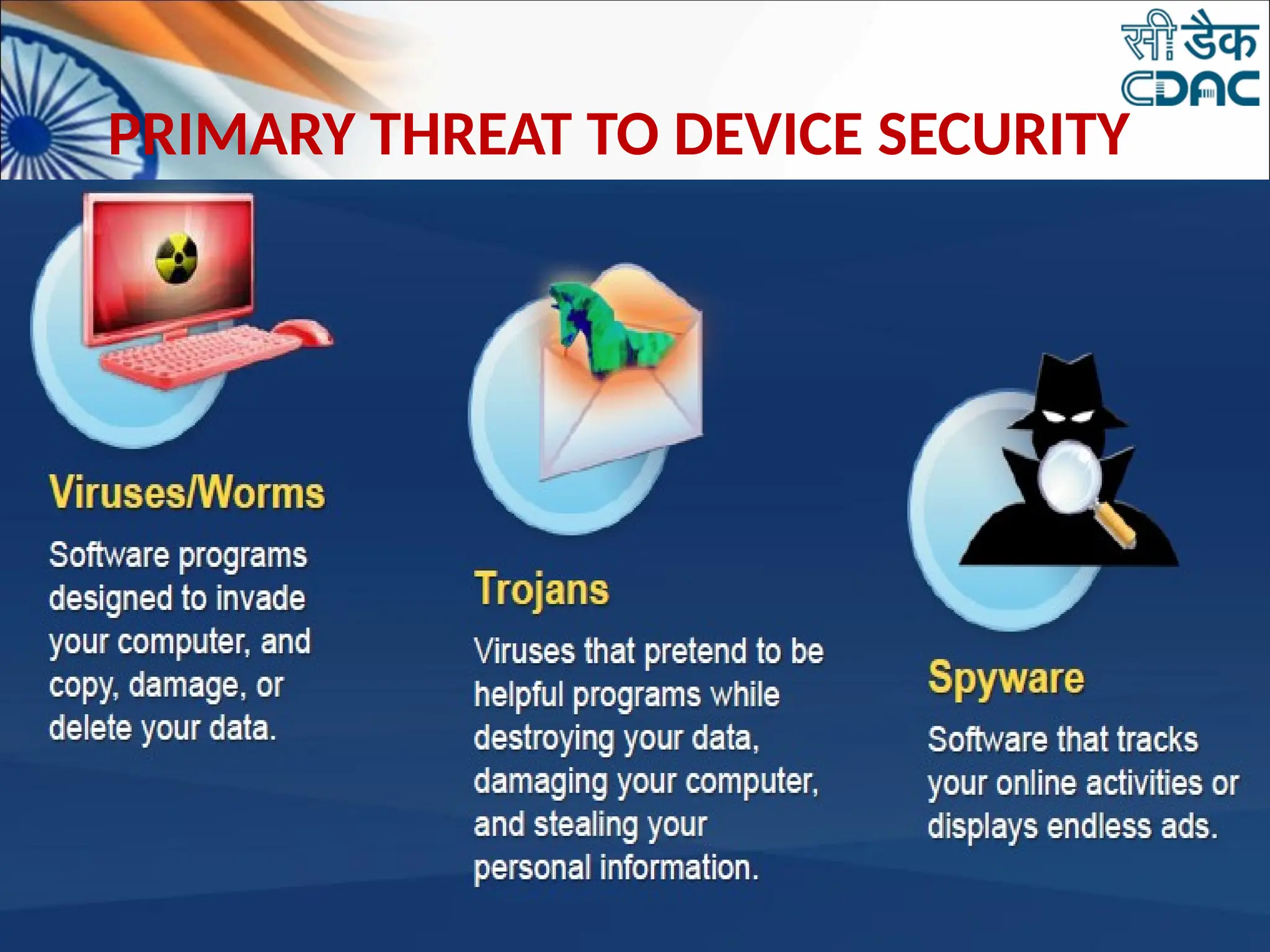
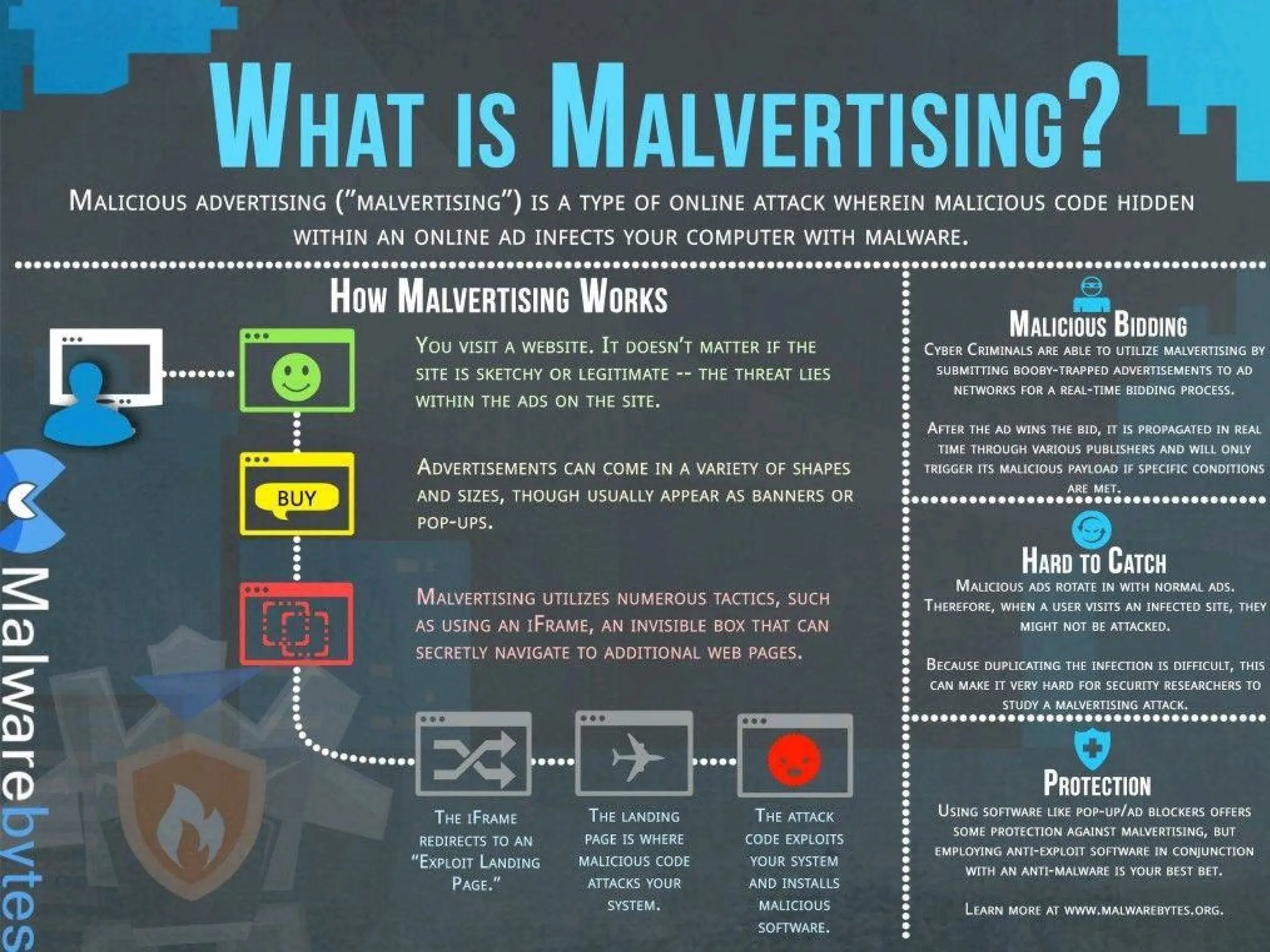
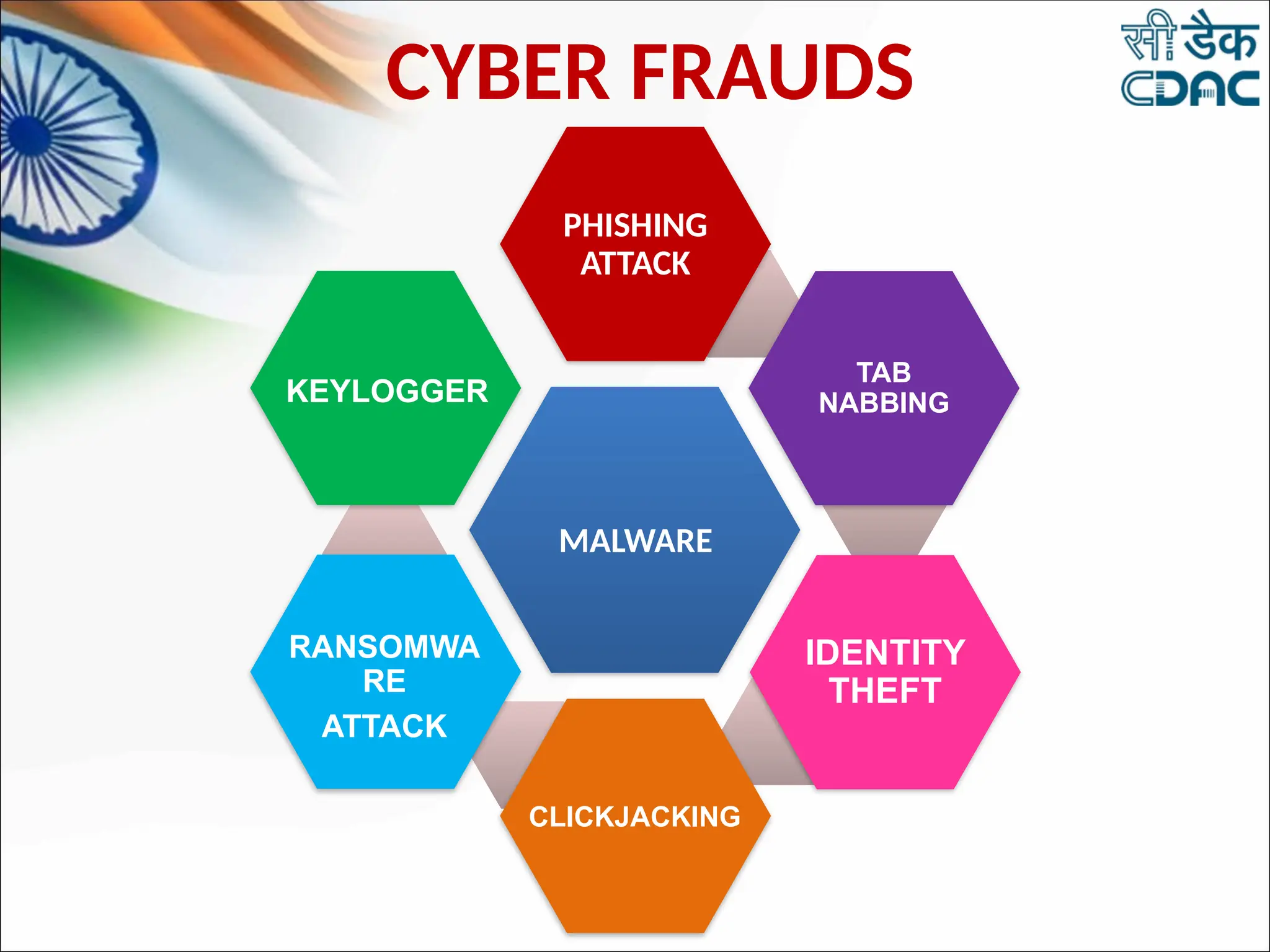
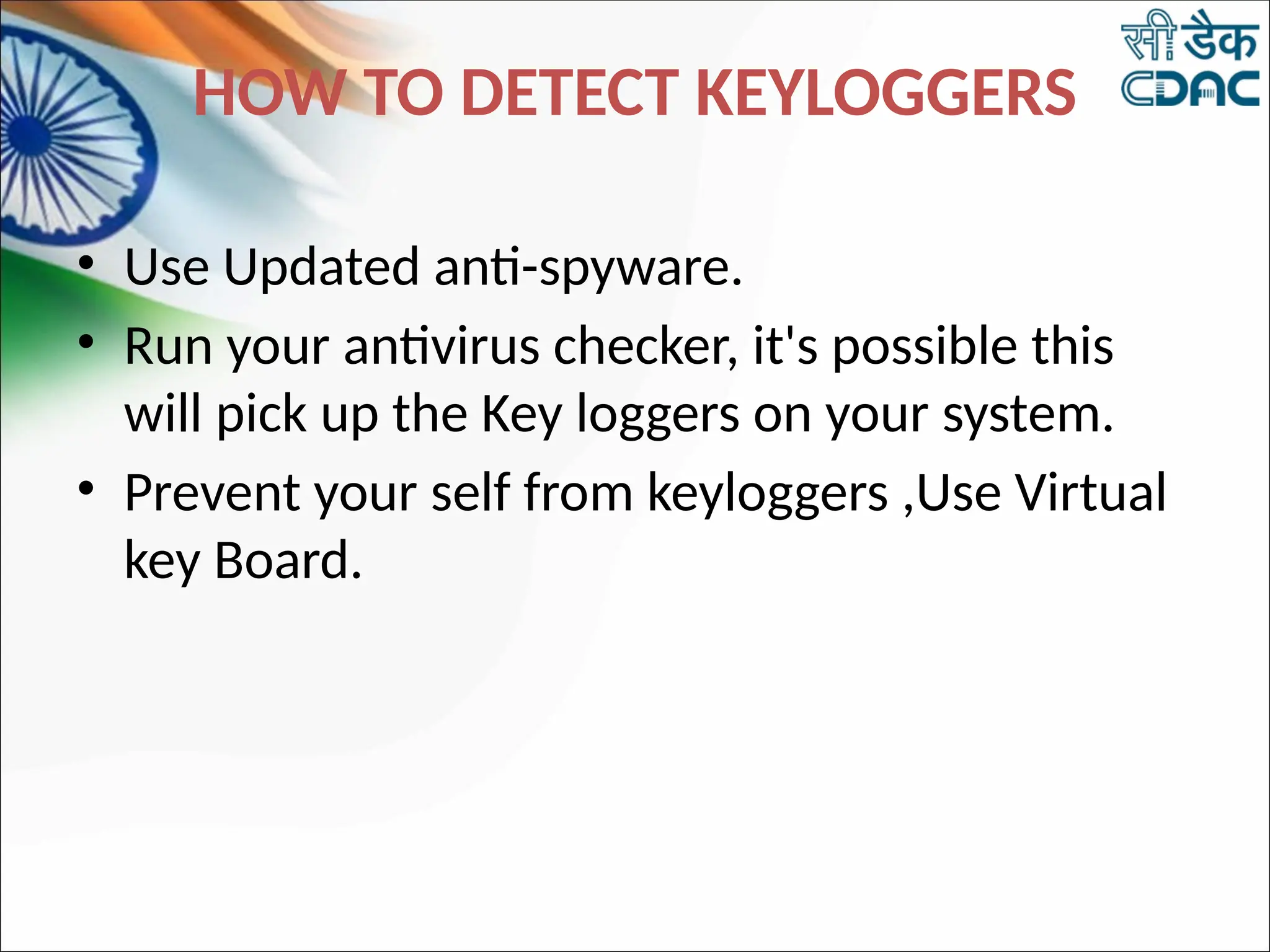
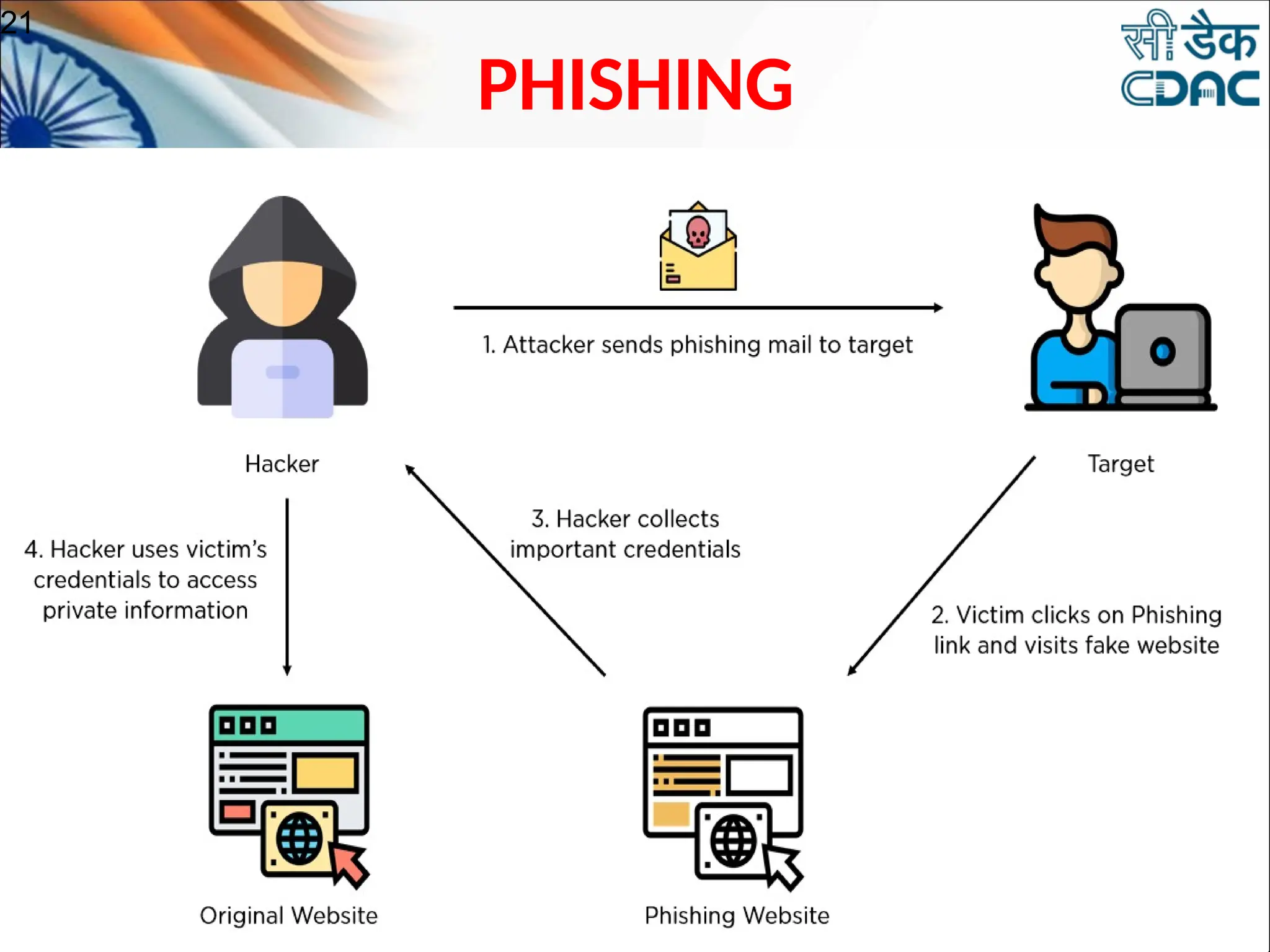
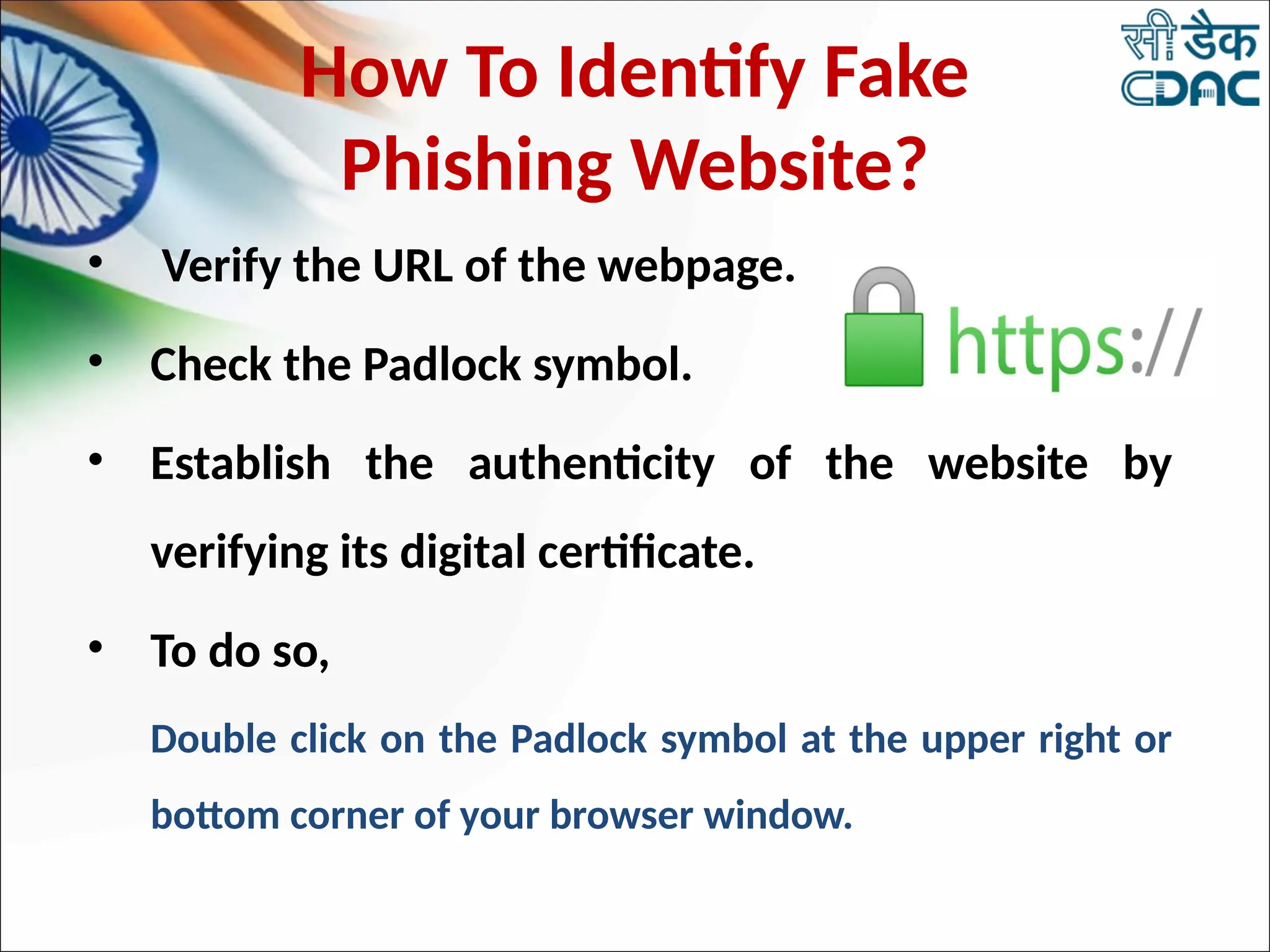
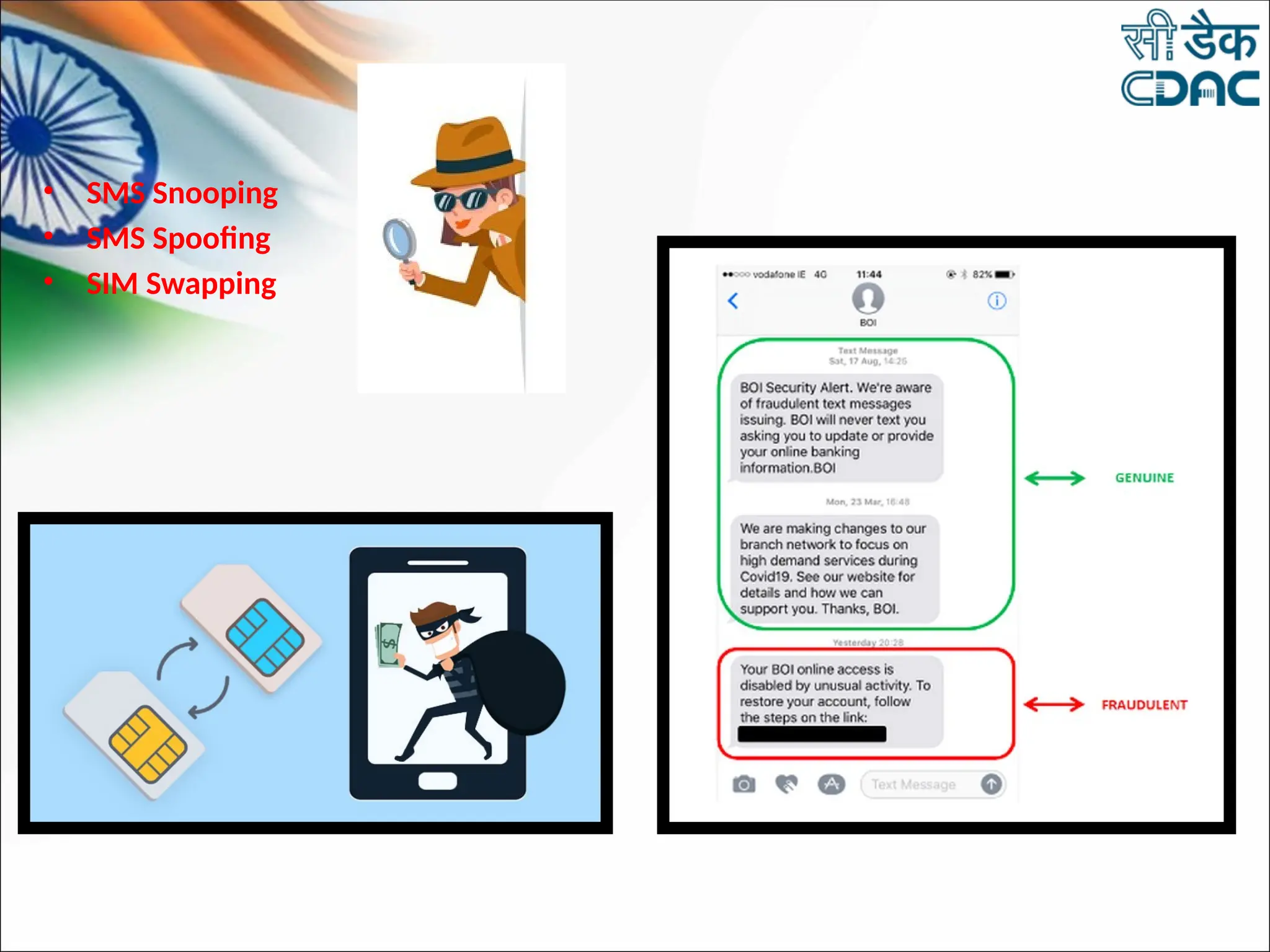
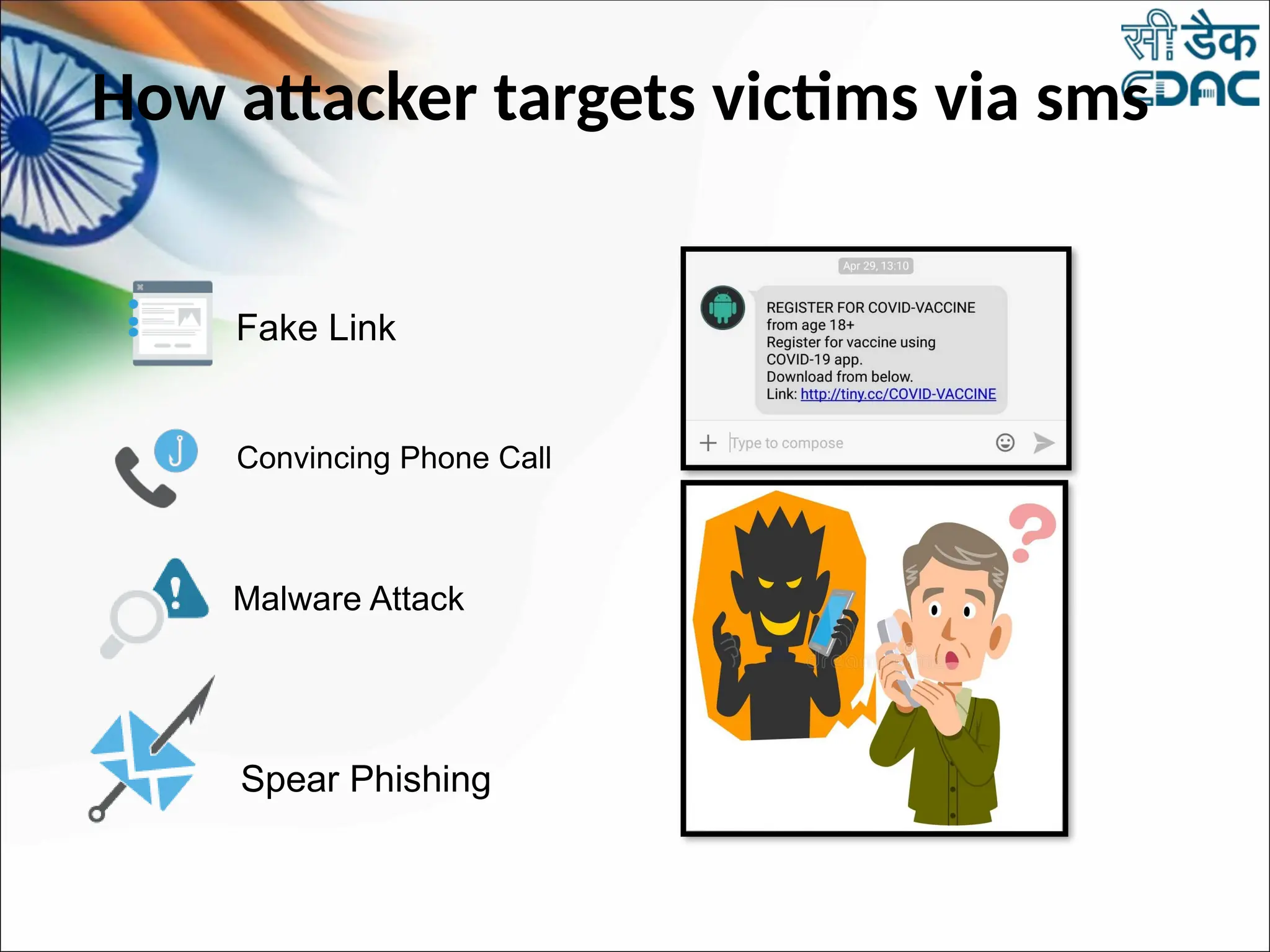
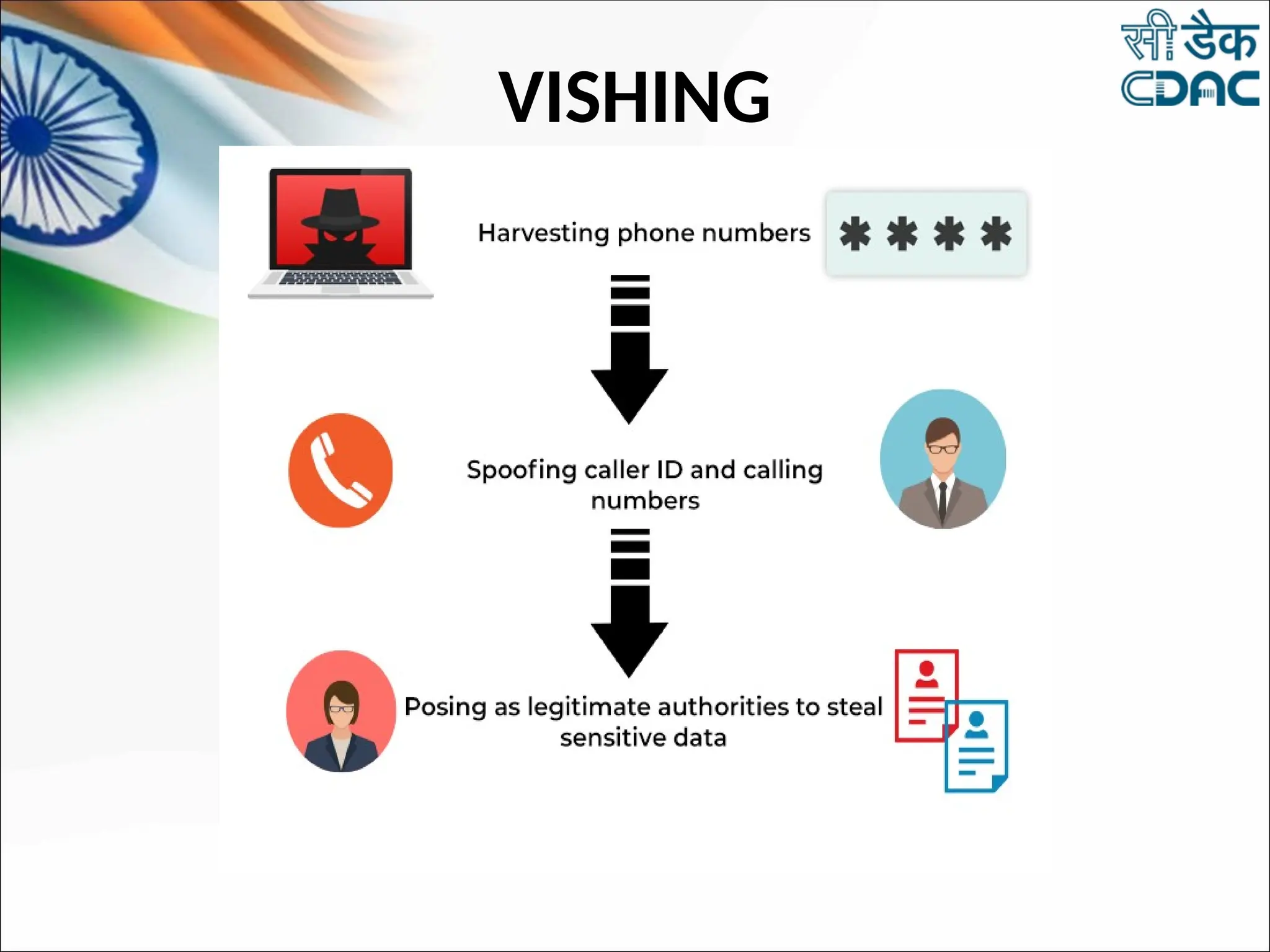
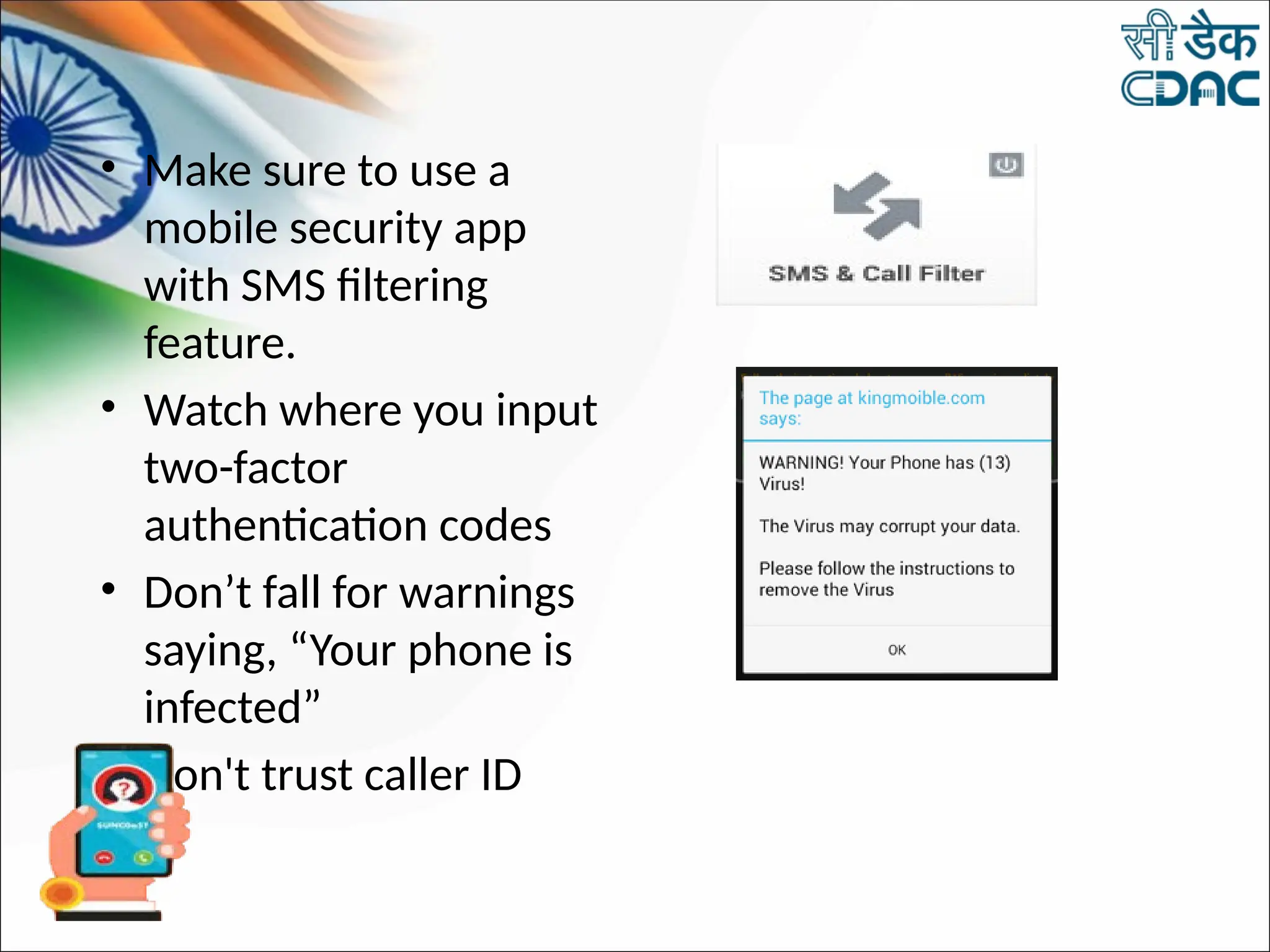
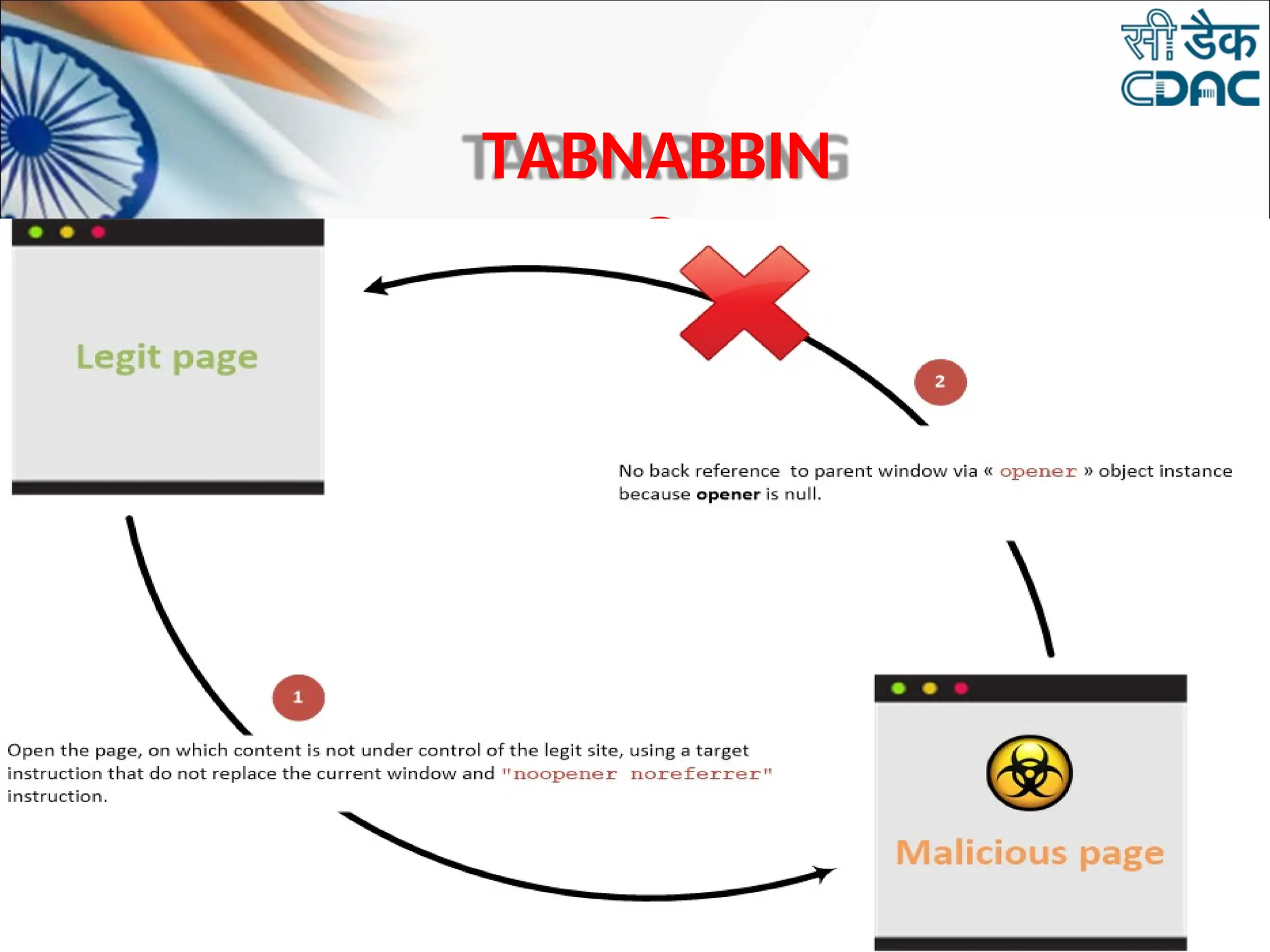
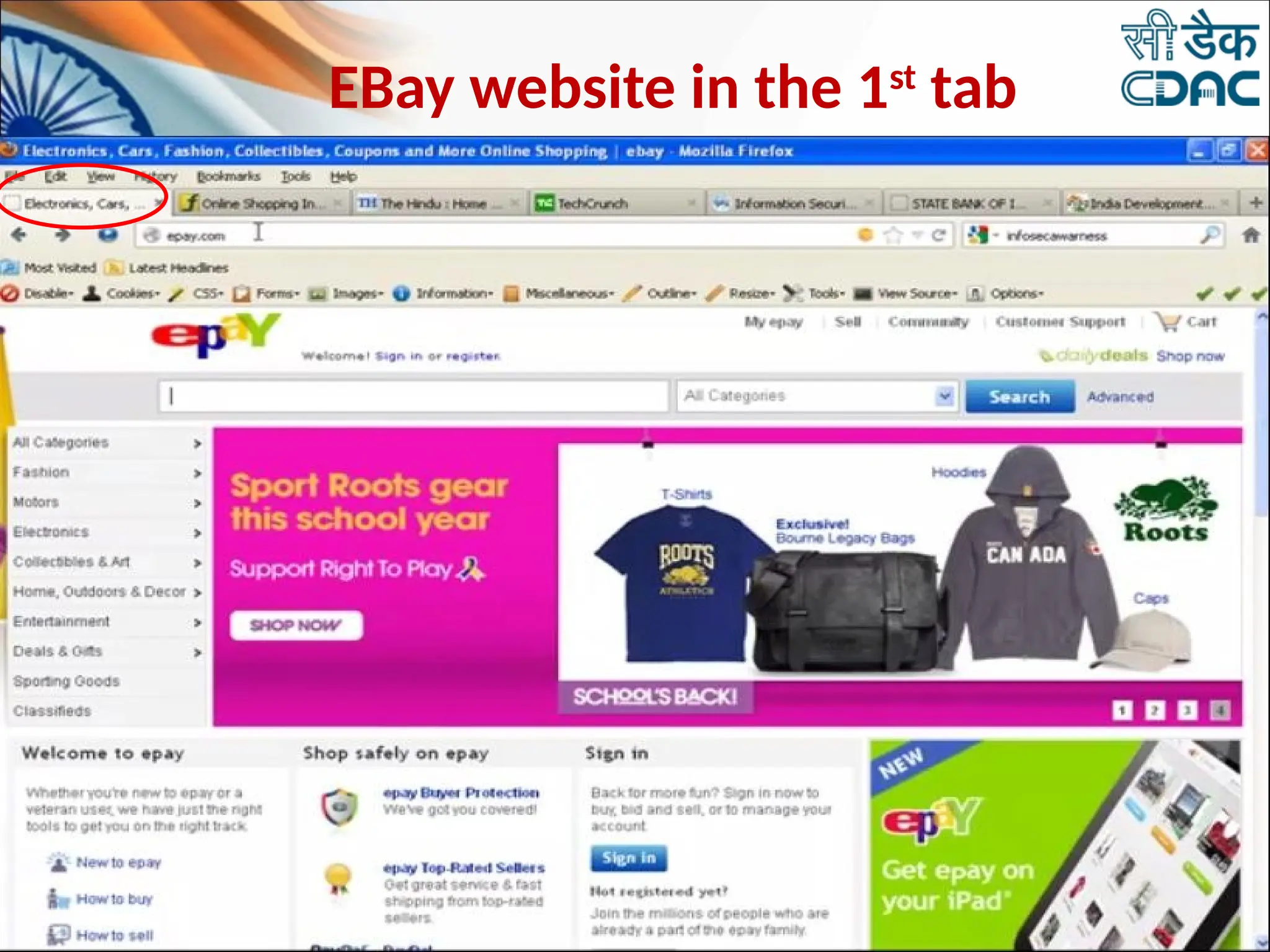
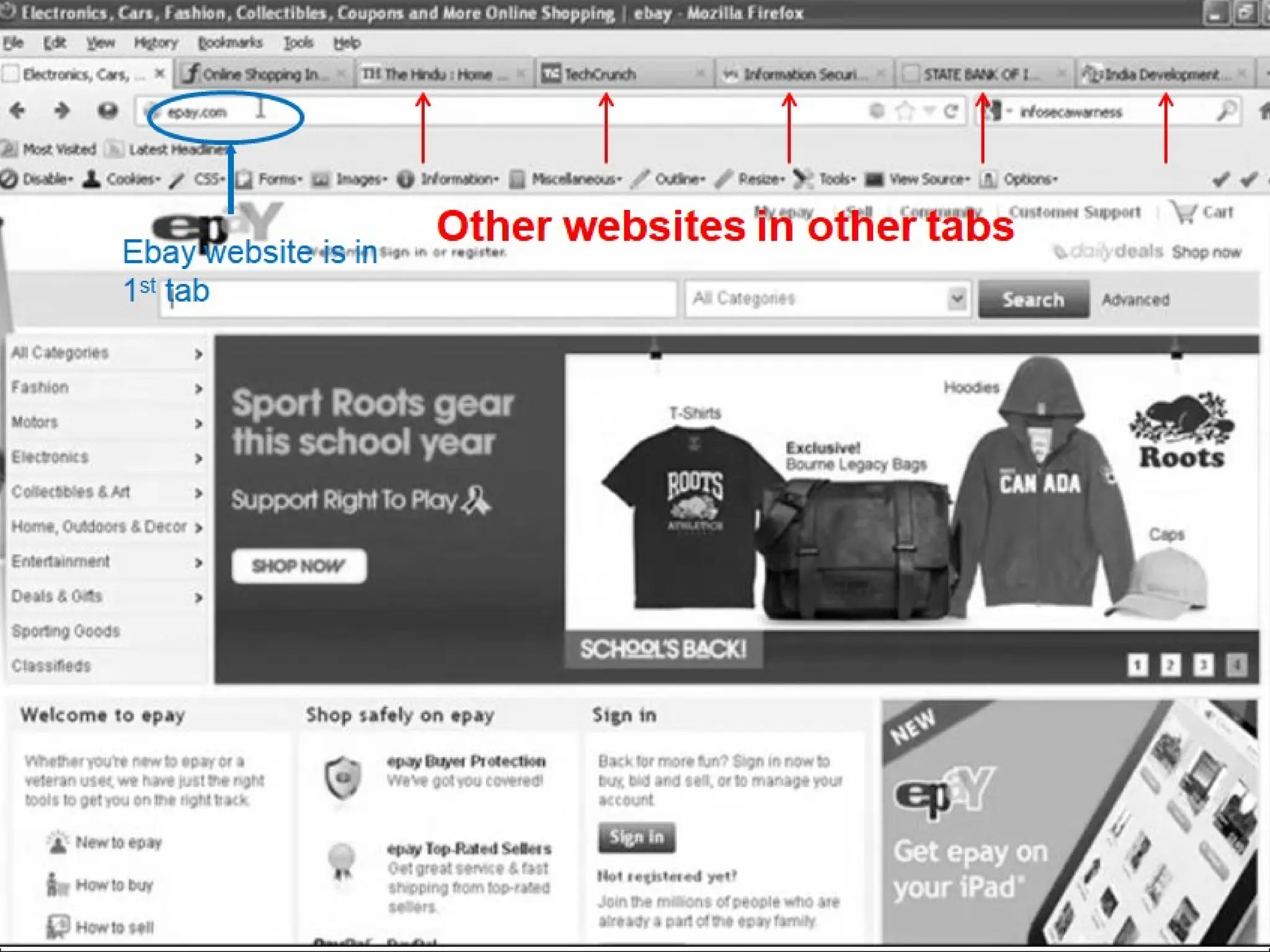
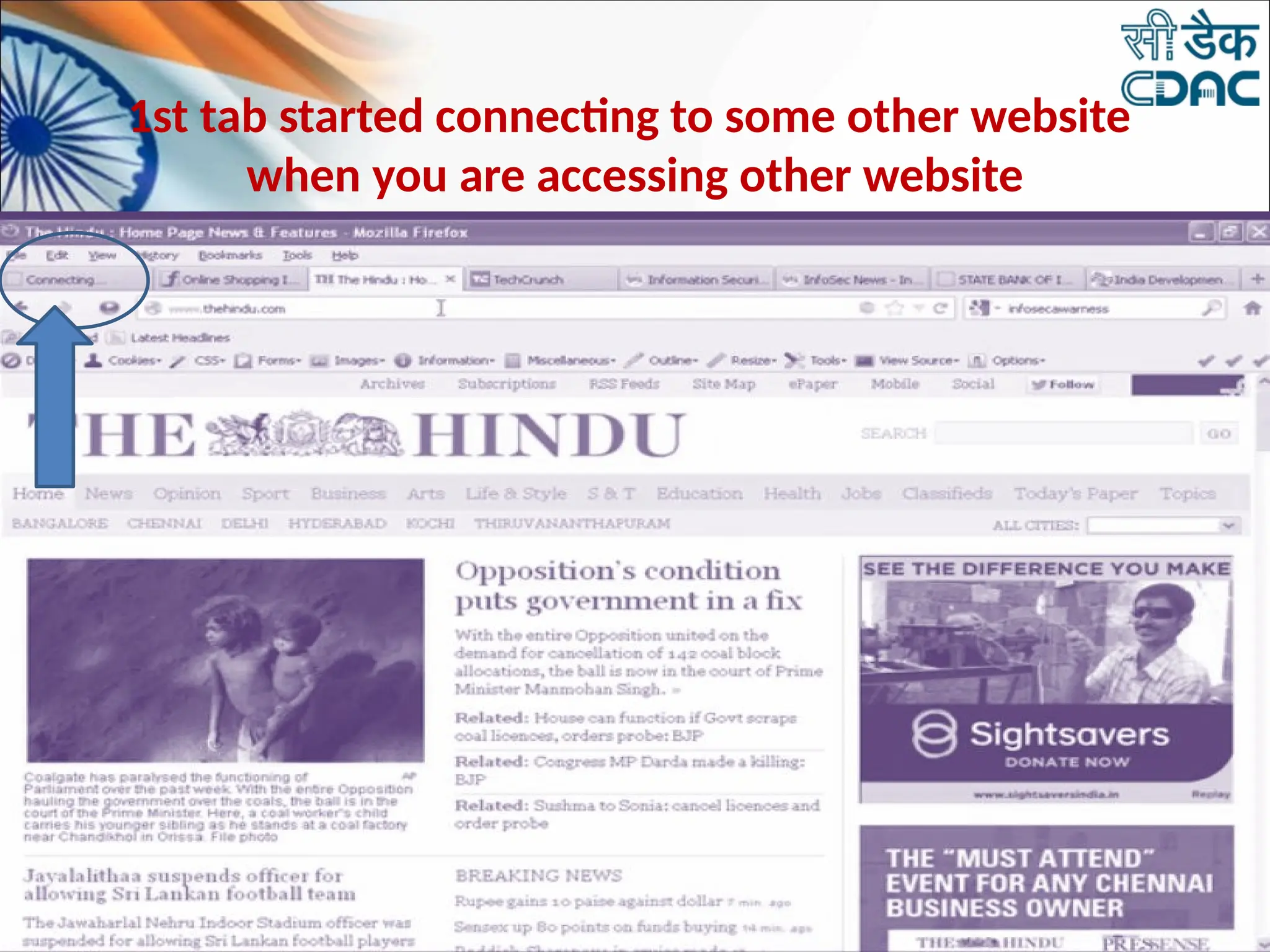
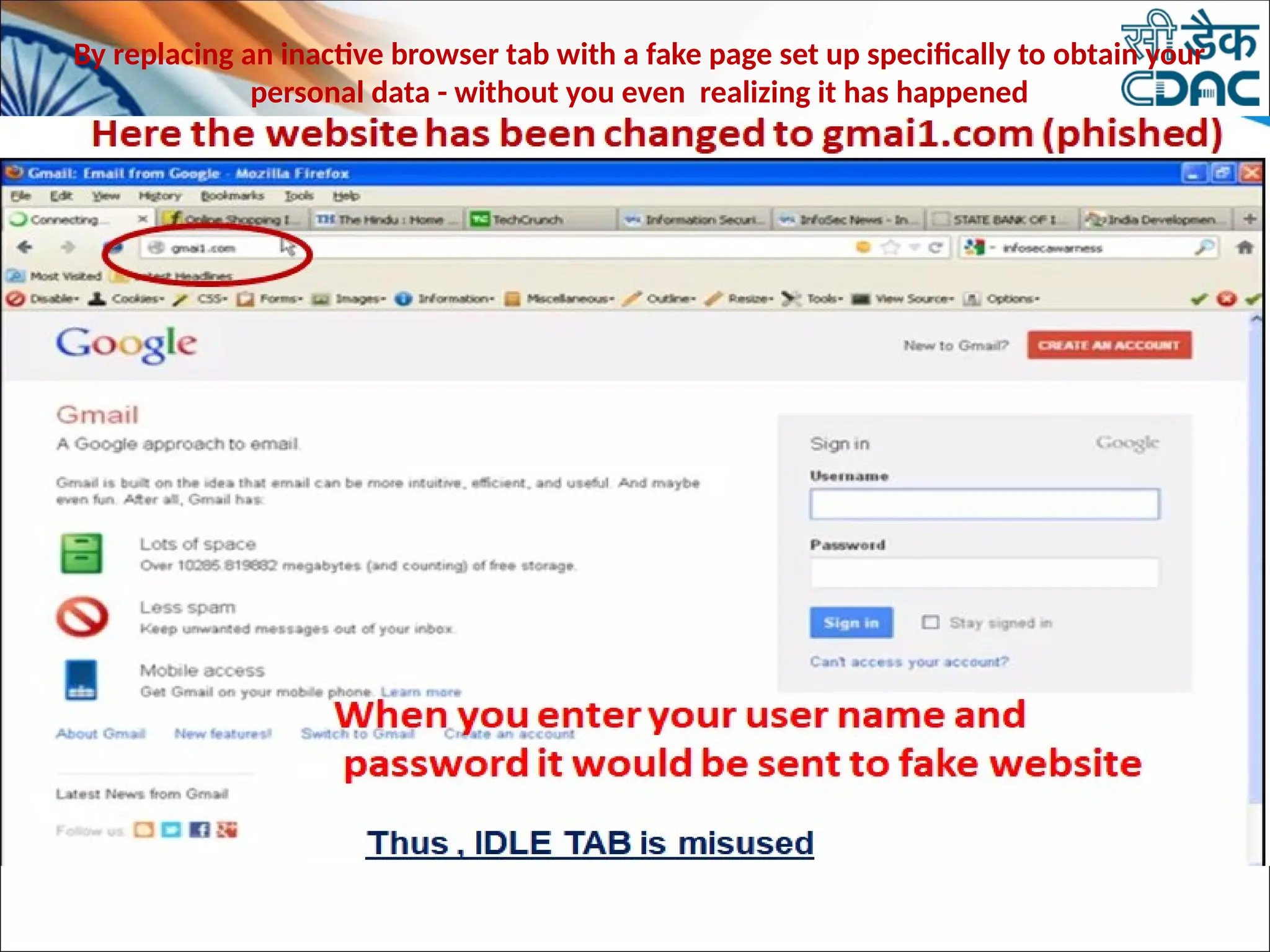
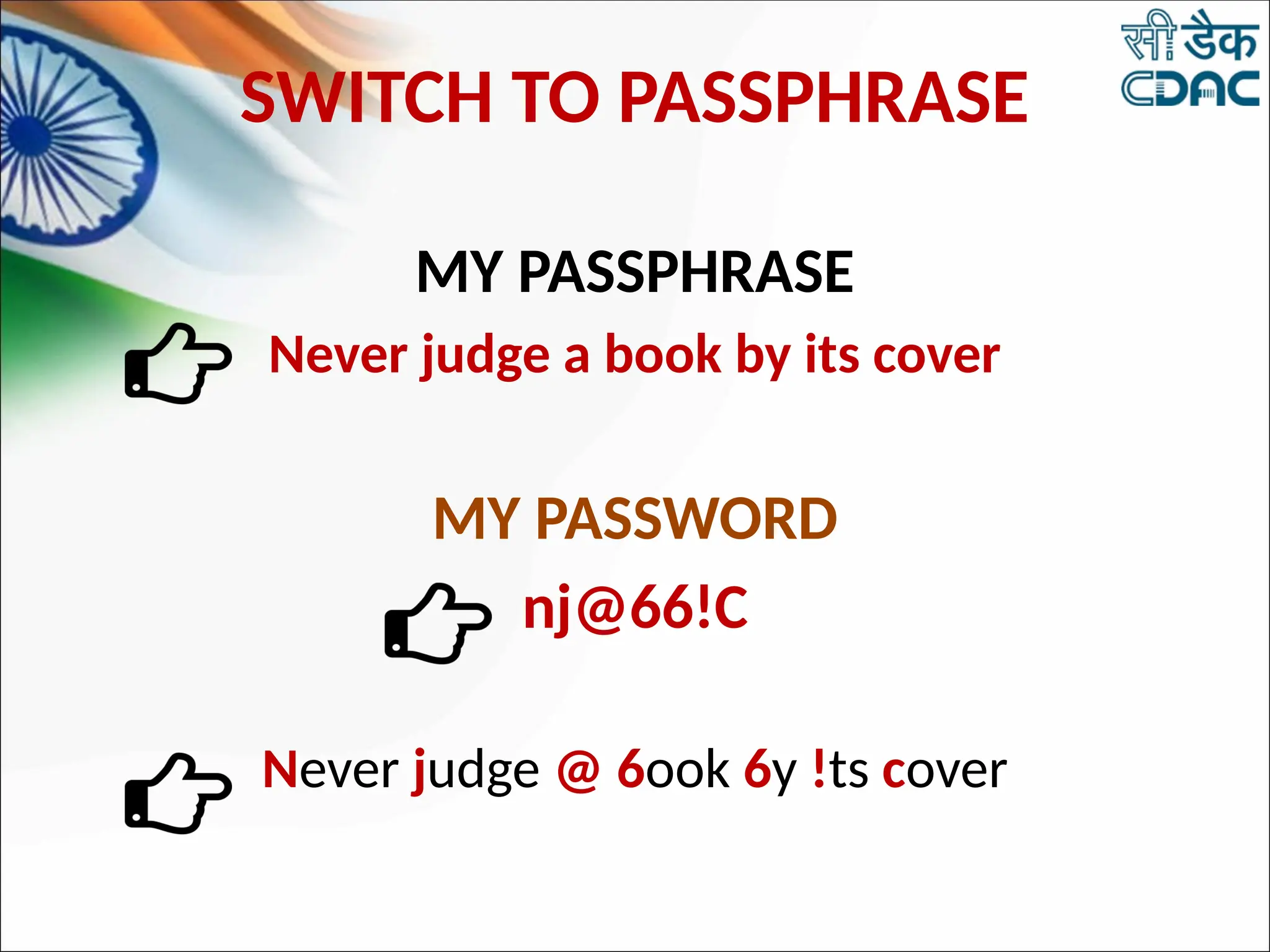
The document discusses data privacy and safeguarding digital footprints, emphasizing the importance of careful sharing and online behavior. It outlines the types of digital footprints, common cyber threats such as phishing and identity theft, and preventive measures individuals can take to secure their personal information. Additionally, it provides tips for using public computers and recognizing phishing attempts, along with recommendations for reporting cyber incidents.